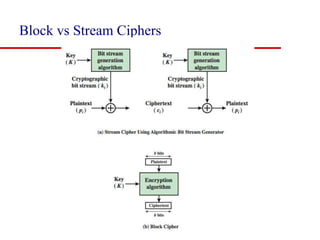
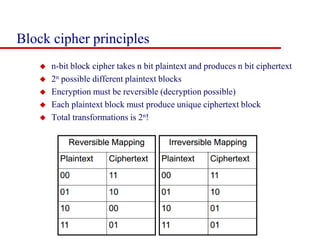
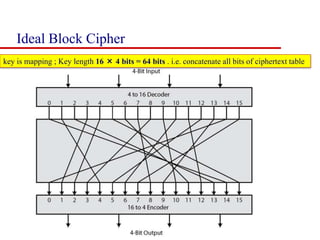
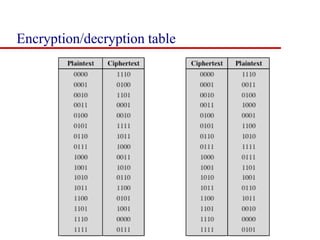
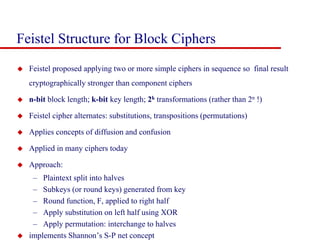
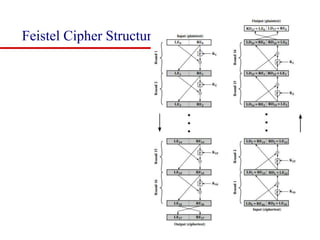
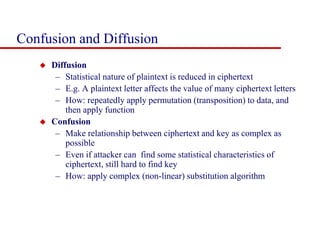
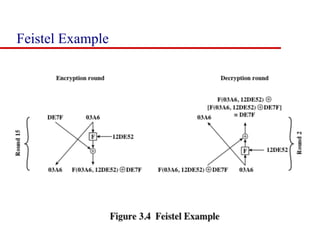
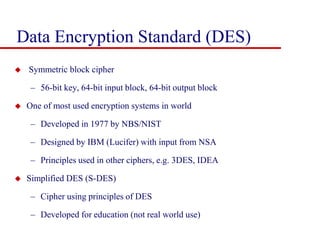
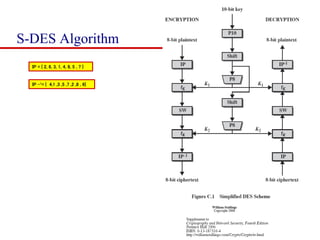
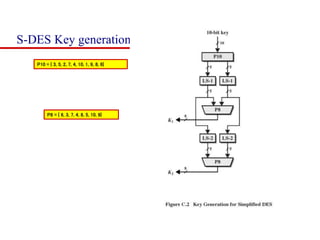
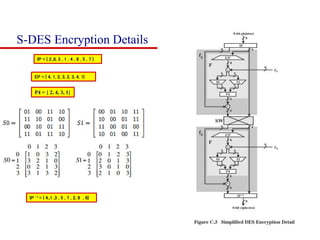
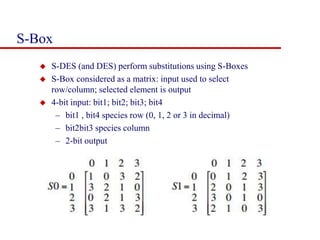
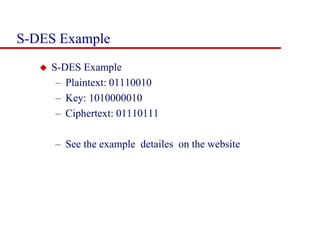
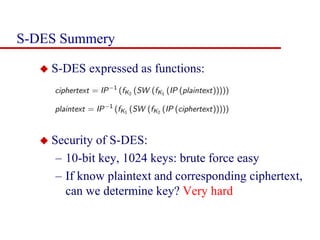
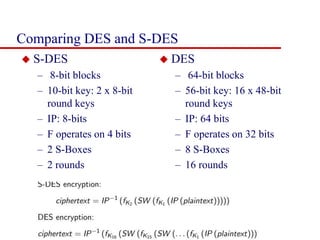
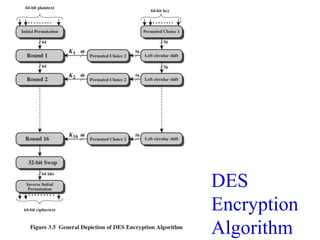
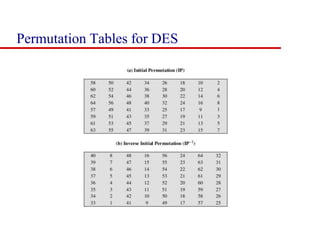
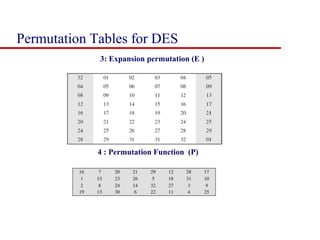
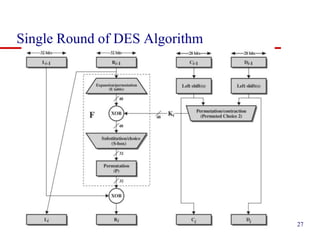
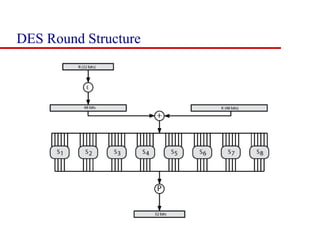
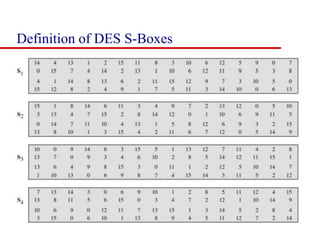
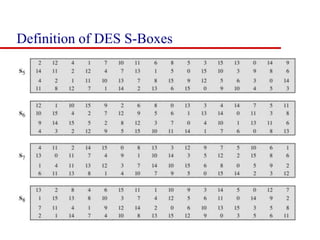
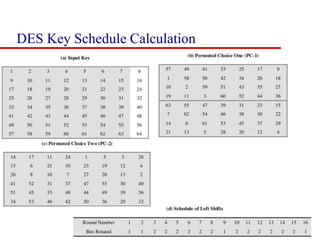
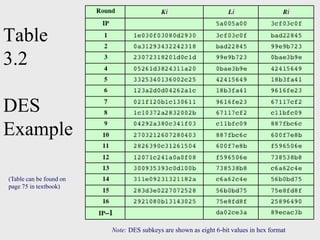
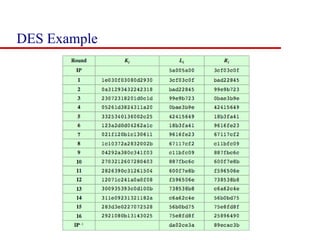
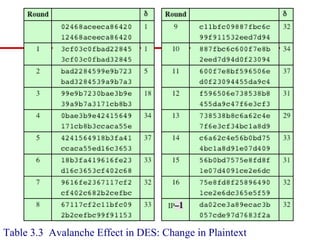
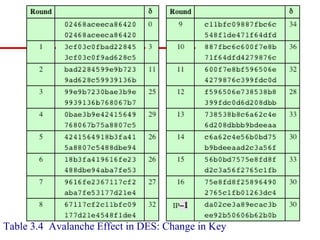
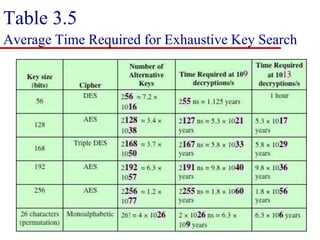
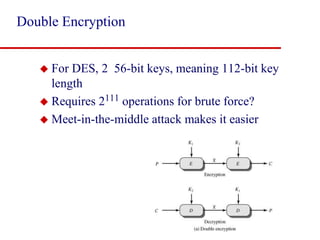
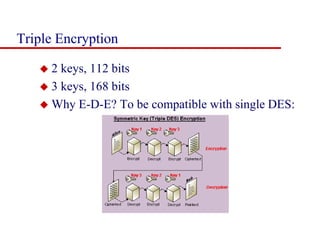
This document discusses block ciphers and summarizes the Data Encryption Standard (DES) algorithm. It introduces block ciphers and the Feistel structure used in many modern block ciphers. It then describes the DES algorithm in detail, including its 56-bit key, 64-bit block size, Feistel structure using substitution boxes and round keys, and vulnerability to brute force attacks. It also summarizes triple DES which strengthens DES security by using 168-bit keys.