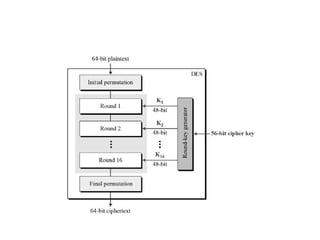
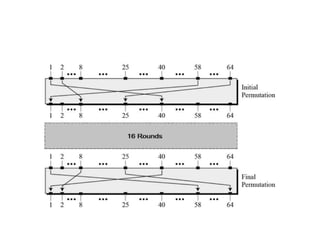
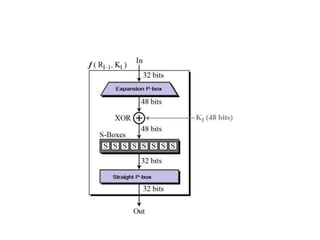
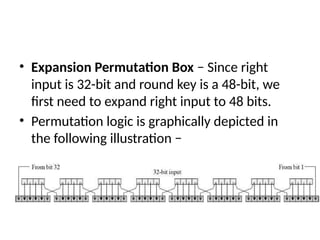
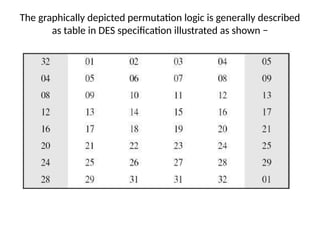
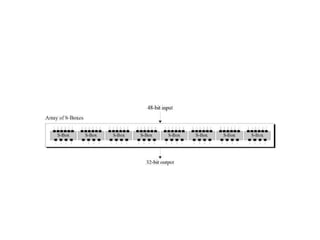
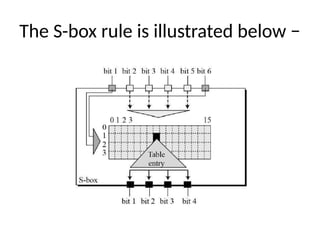
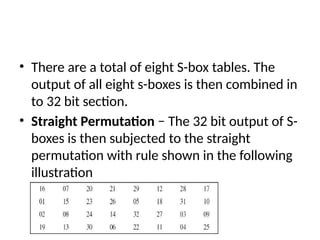
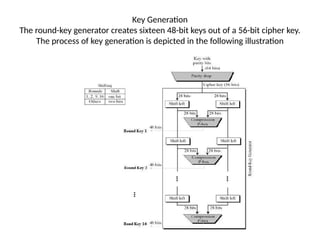
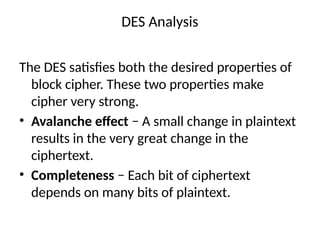
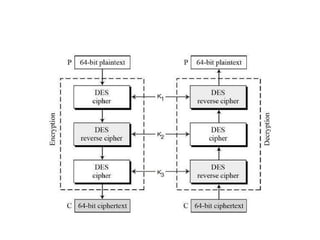
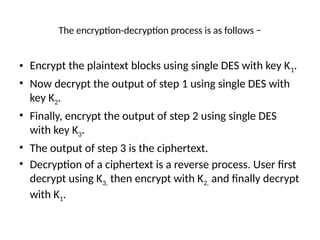
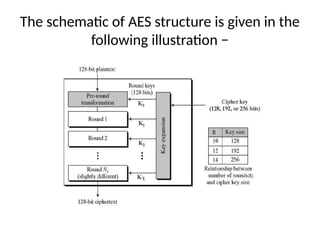
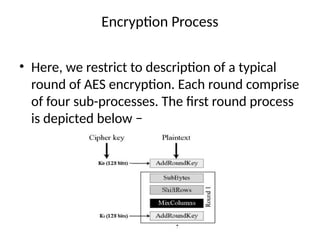
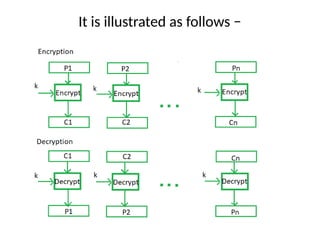
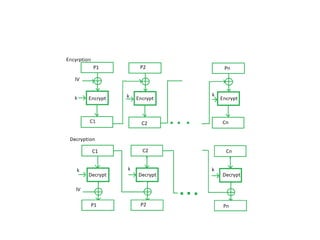
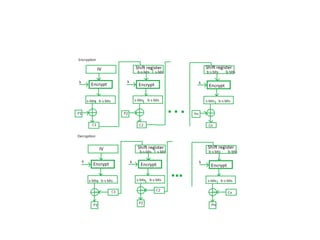
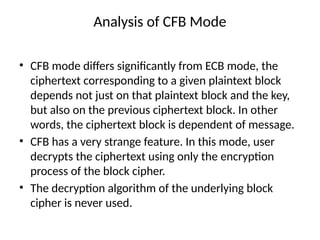
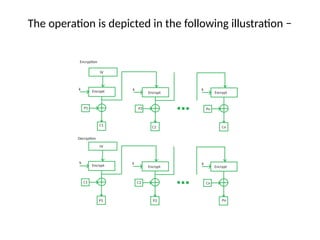
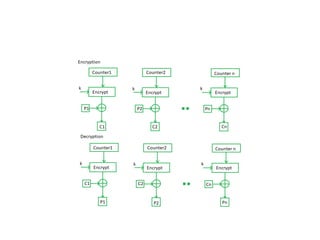
The document provides an overview of various encryption standards, namely DES, Triple DES, and AES, detailing their structures, key management, and modes of operation. DES is a symmetric-key block cipher with a 56-bit effective key length, while Triple DES enhances security by applying DES three times with different keys. AES, considered superior, employs a substitution-permutation network with variable rounds based on key length, and has gained wide adoption due to its speed and robustness against cryptanalysis.