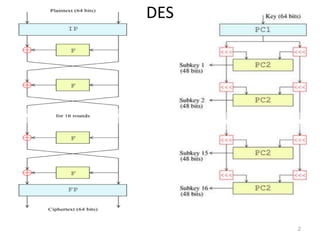
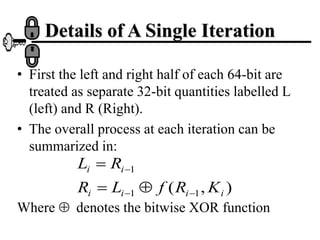
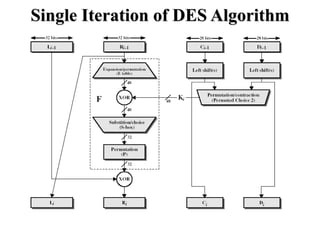
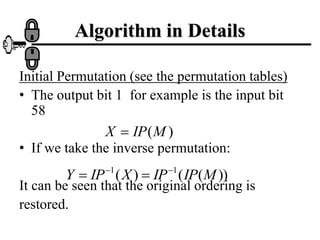
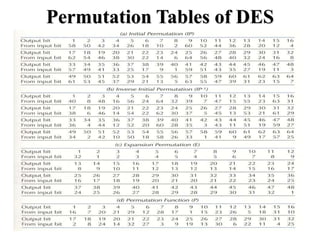
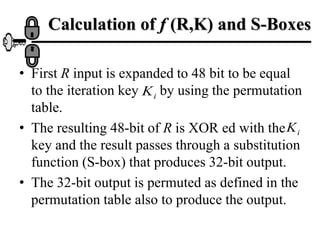
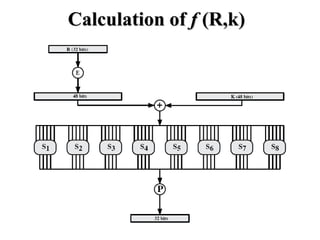
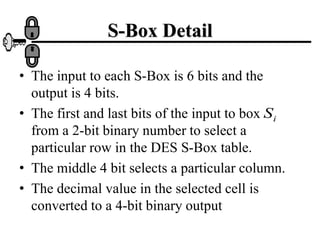
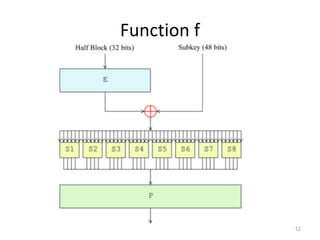
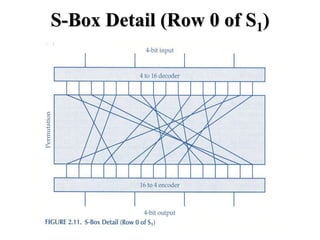
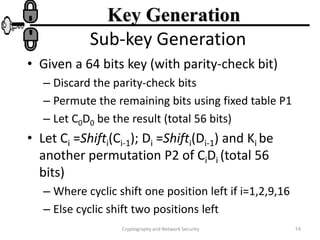
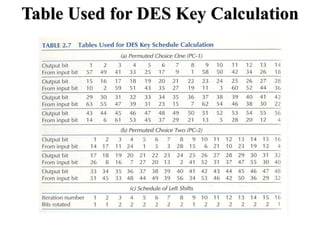
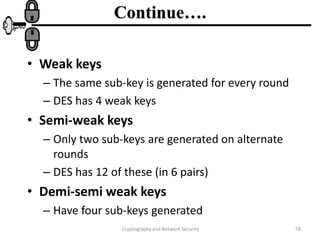
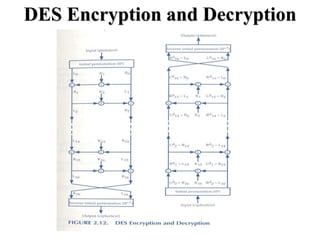
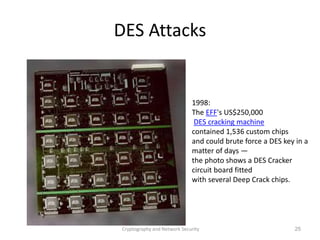
The document discusses the Data Encryption Standard (DES) algorithm. It was adopted in 1977 and encrypts 64-bit blocks using a 56-bit key. The algorithm uses permutations and substitutions to encrypt data in multiple rounds. Weak keys that reduce the algorithm's security are identified. Attacks like differential and linear cryptanalysis have been developed against DES. Alternatives like triple DES and extending the key length were proposed to strengthen it against attacks.









![Double DES
• The simplified form of multiple encryption has
two encryption stage and two keys.
• Given a plaintext P and two keys K1 and K2
one can generate a cipher text C as:
Decryption equation is :
• The key length is 562= 112 bits
]]
[
[ 1
2
P
E
E
C K
K
]]
[
[ 2
1
C
D
D
P K
K
](https://image.slidesharecdn.com/section-8-230517025426-b254be5a/85/section-8-ppt-29-320.jpg)