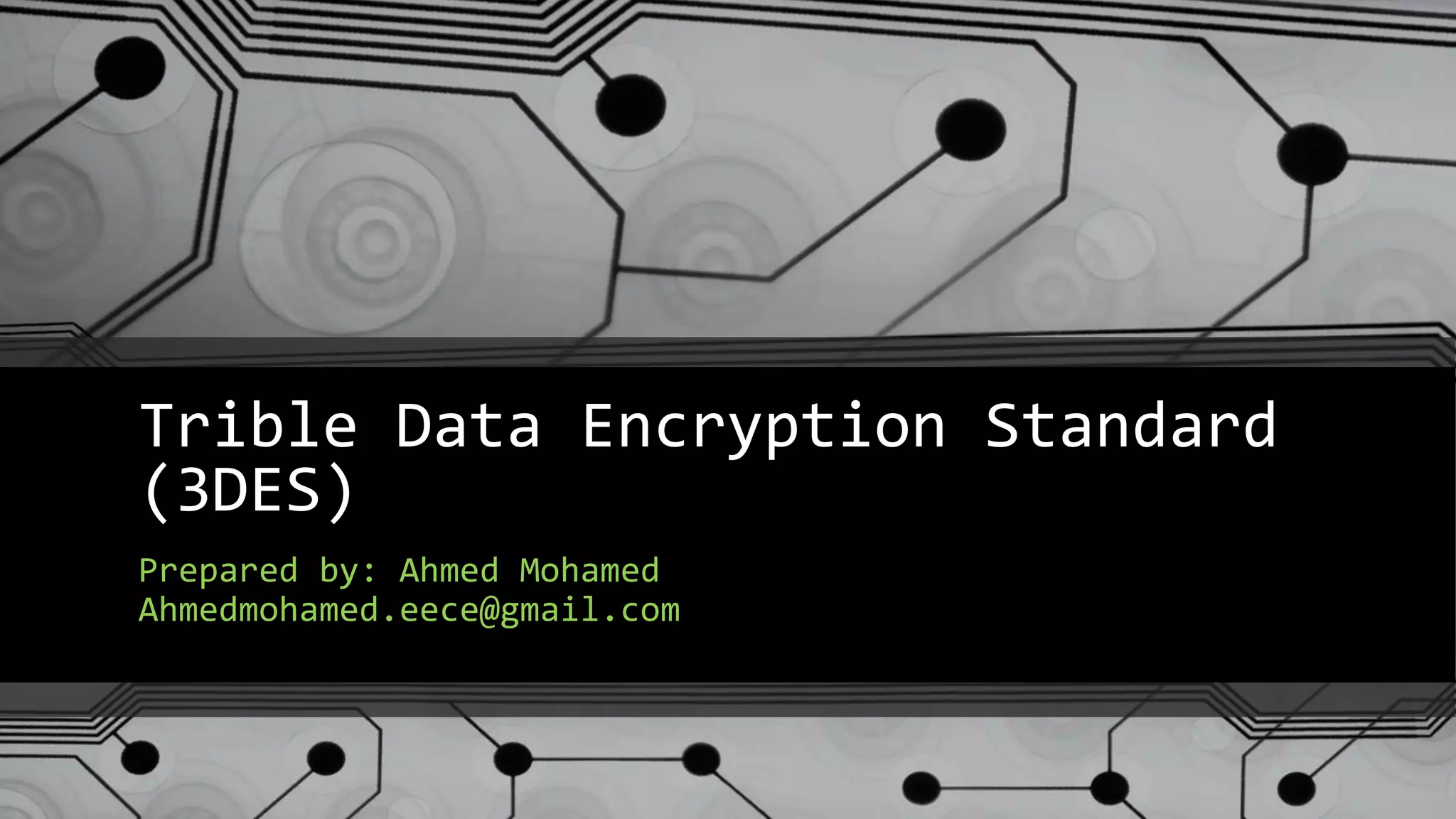
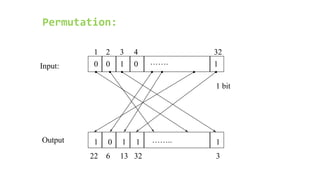
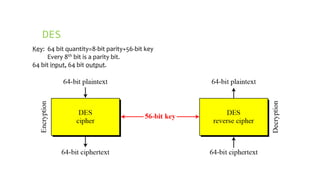
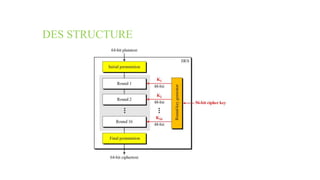
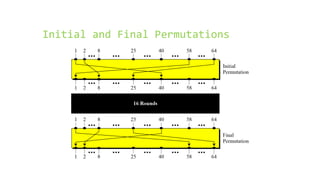
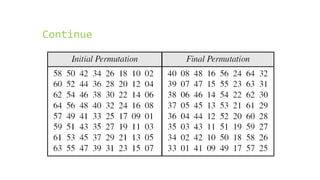
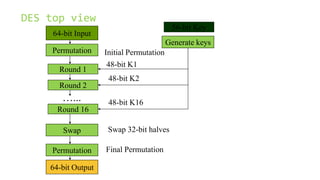
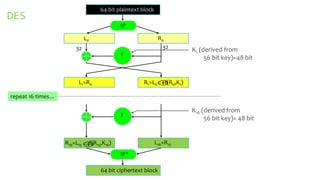
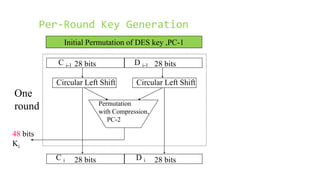
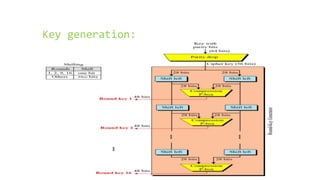
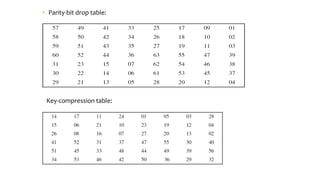
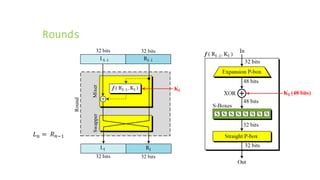
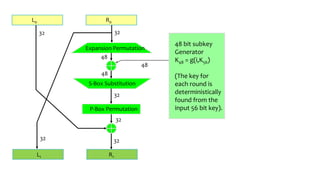
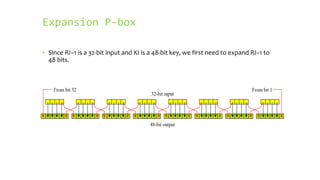
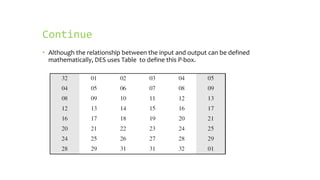
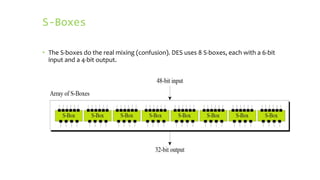
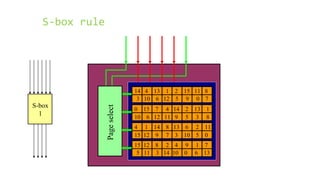
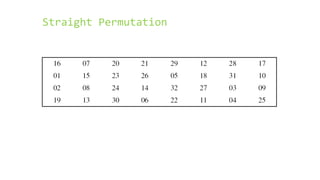
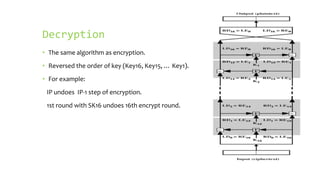
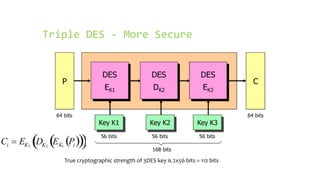
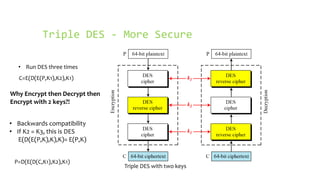
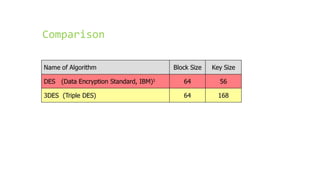
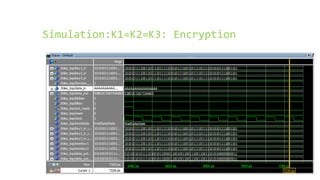
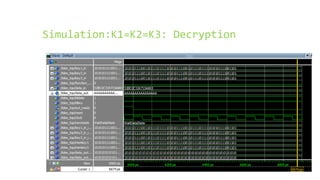
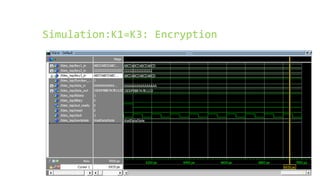
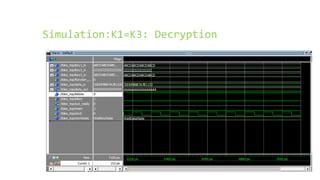
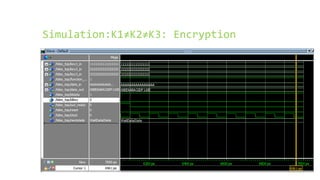
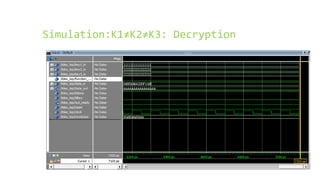
This document provides an overview of the Triple Data Encryption Standard (3DES). It first briefly describes the original Data Encryption Standard (DES) and its key components including the initial and final permutations, substitution boxes, and key schedule. It then explains that 3DES applies DES three times with three different keys to strengthen security by effectively doubling the key size to 112 bits. Simulations are included showing encryption and decryption using 3DES with equal and different keys.