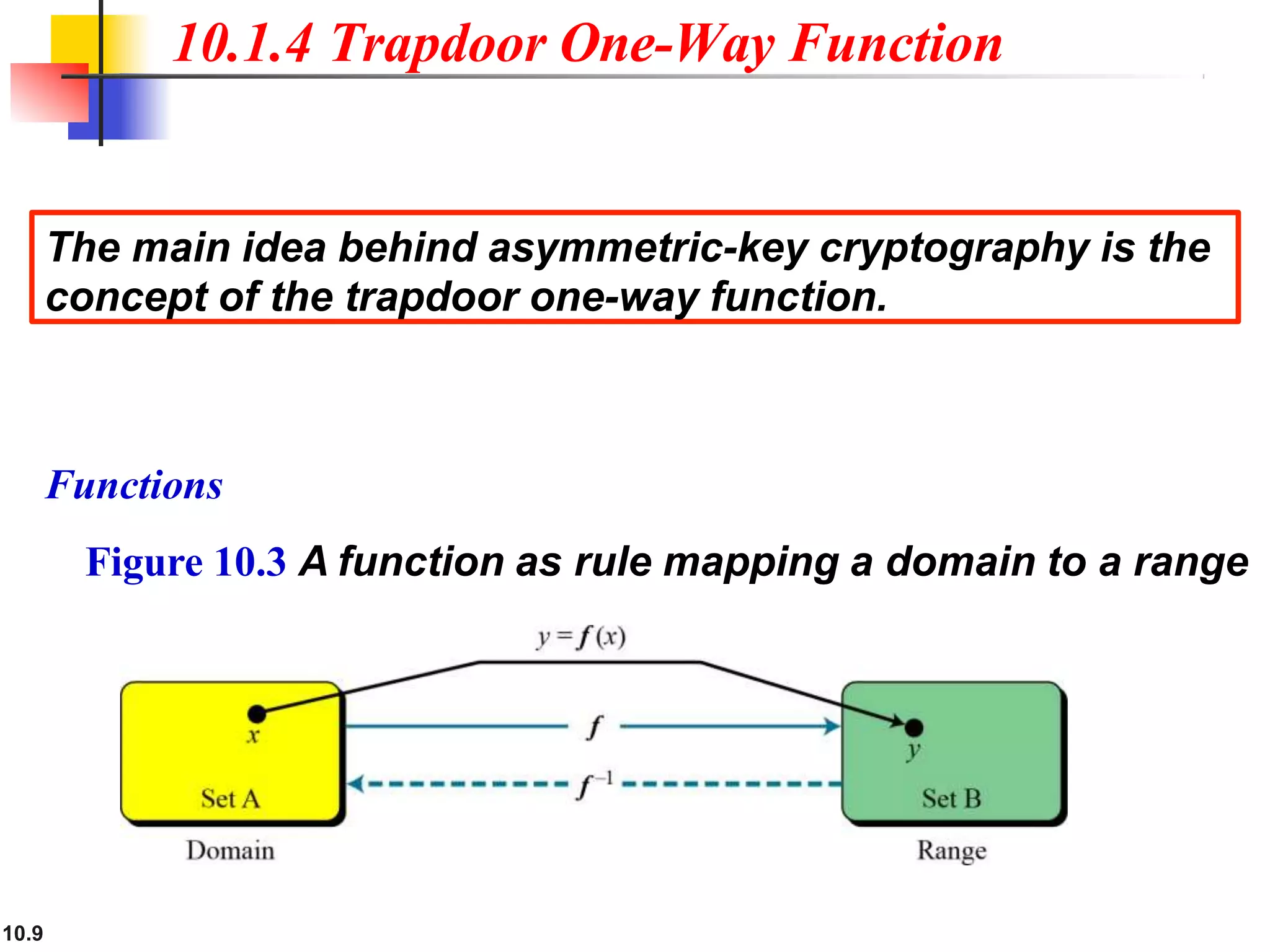
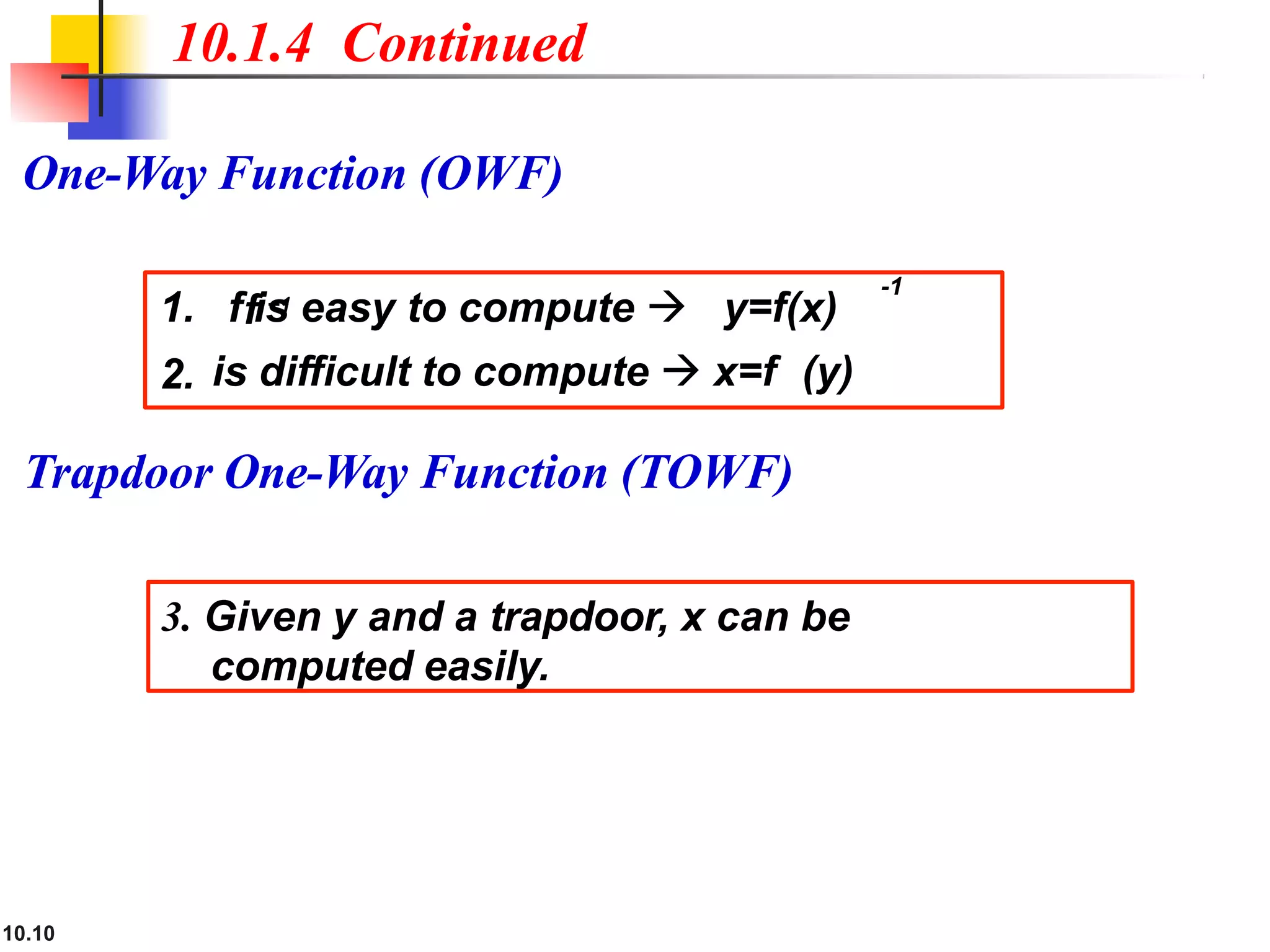
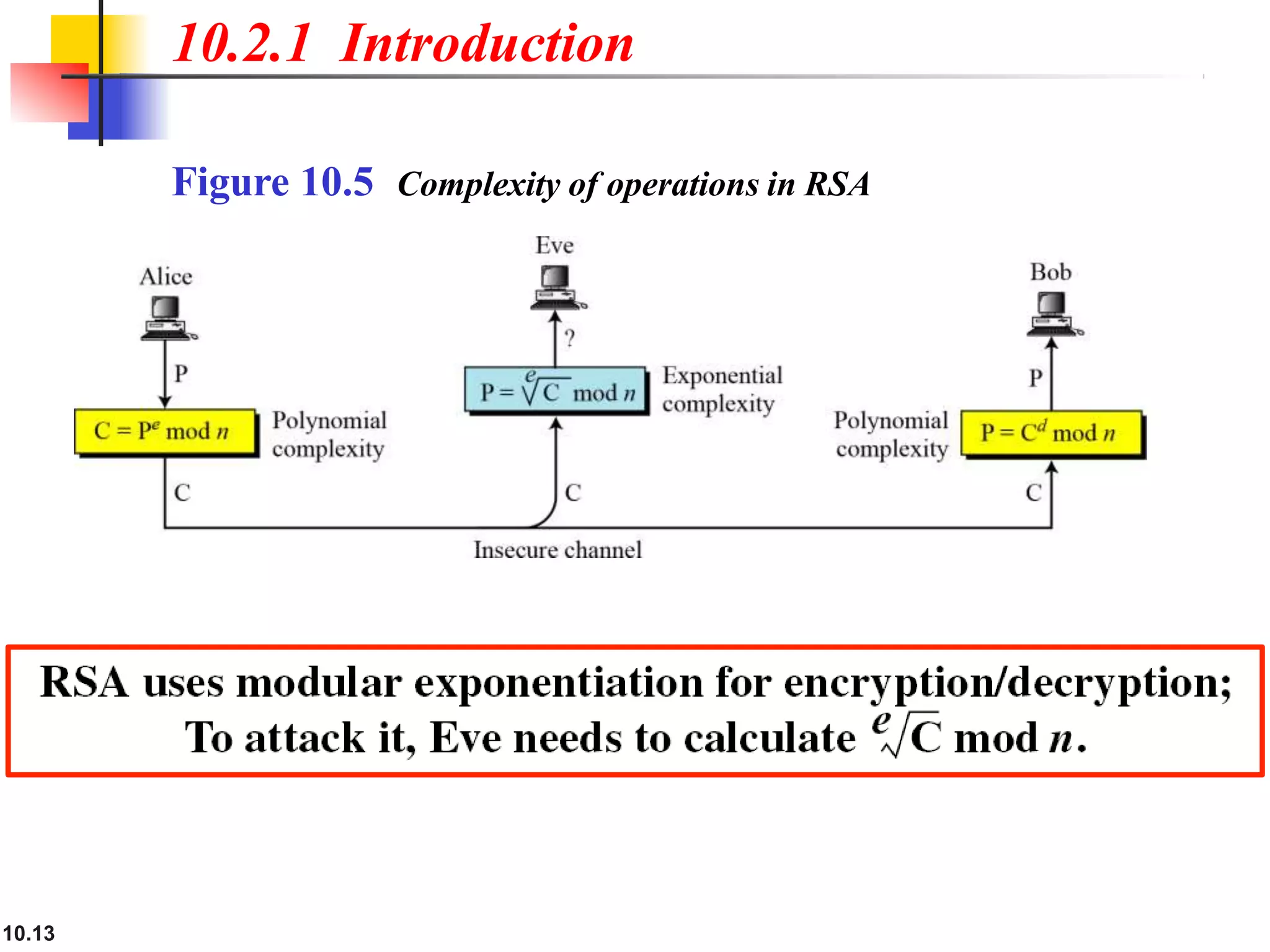
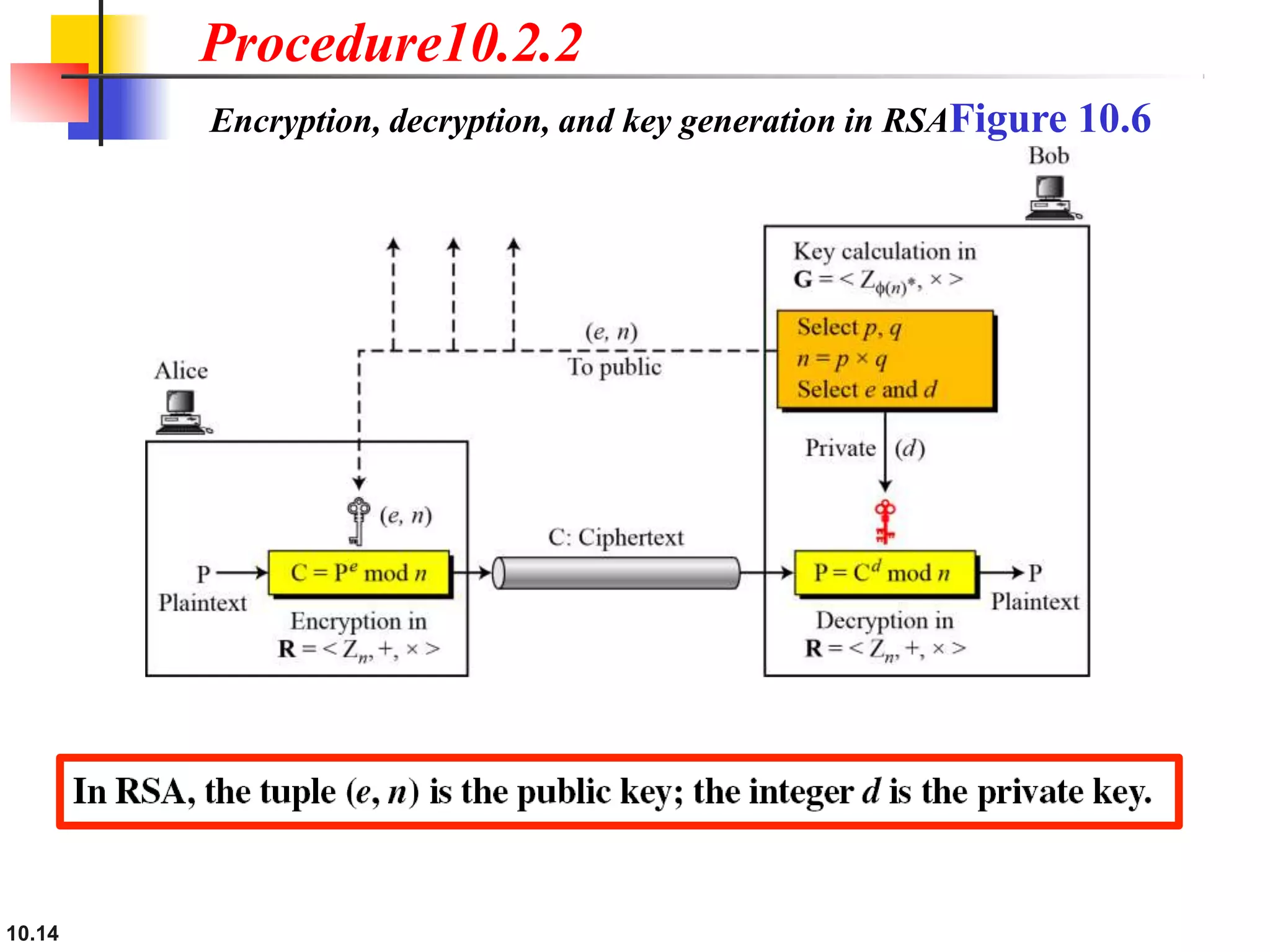
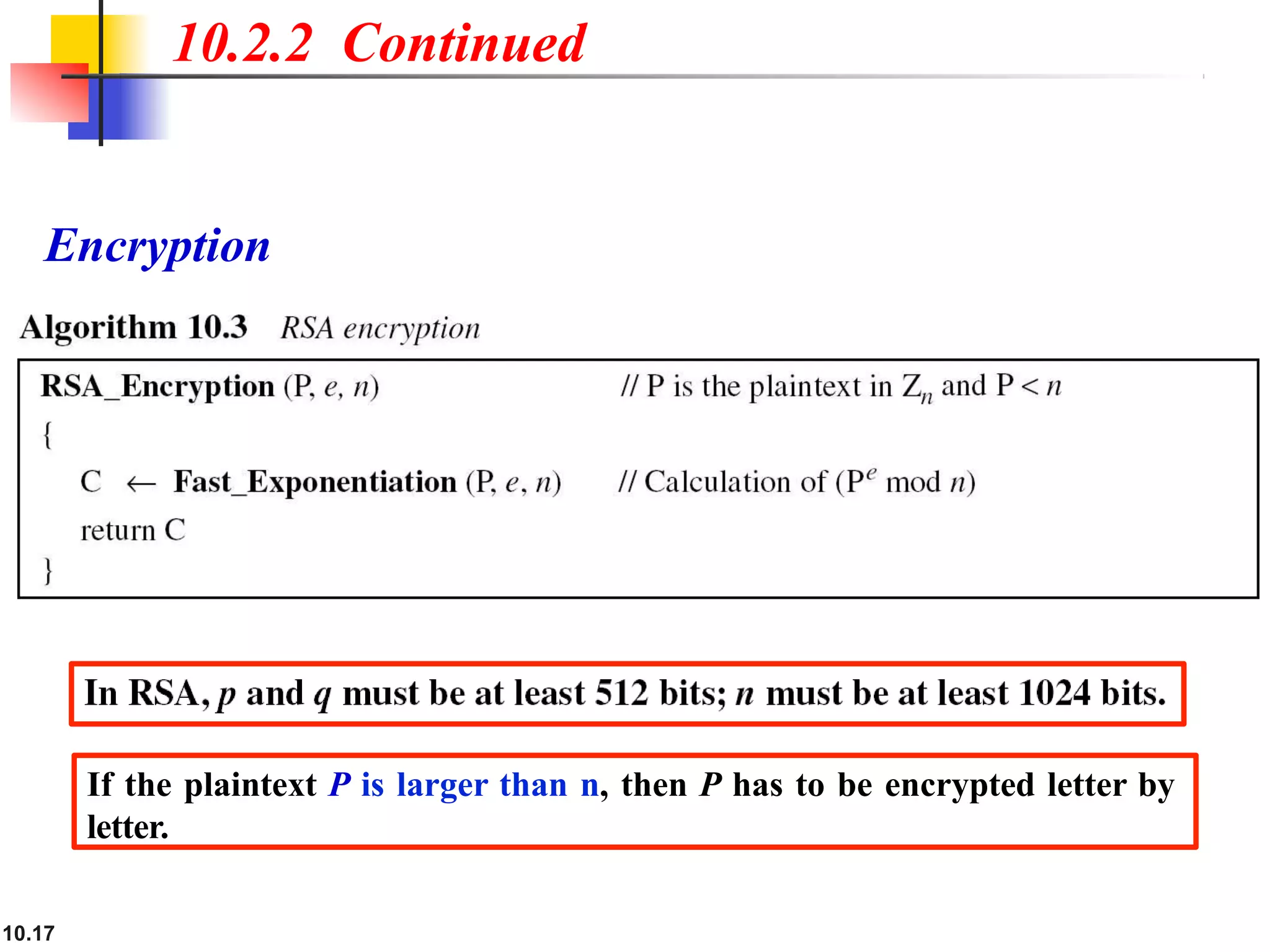
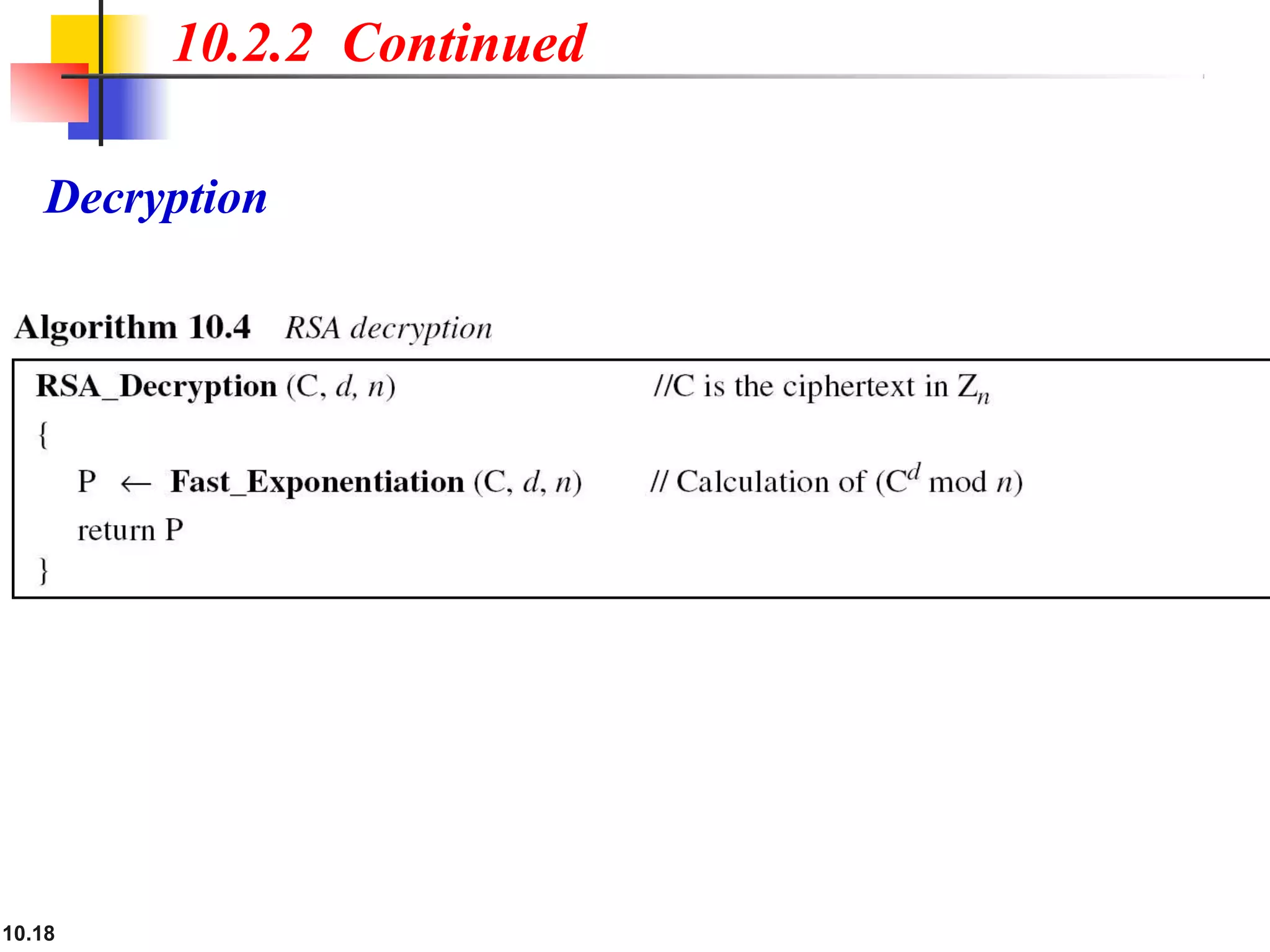
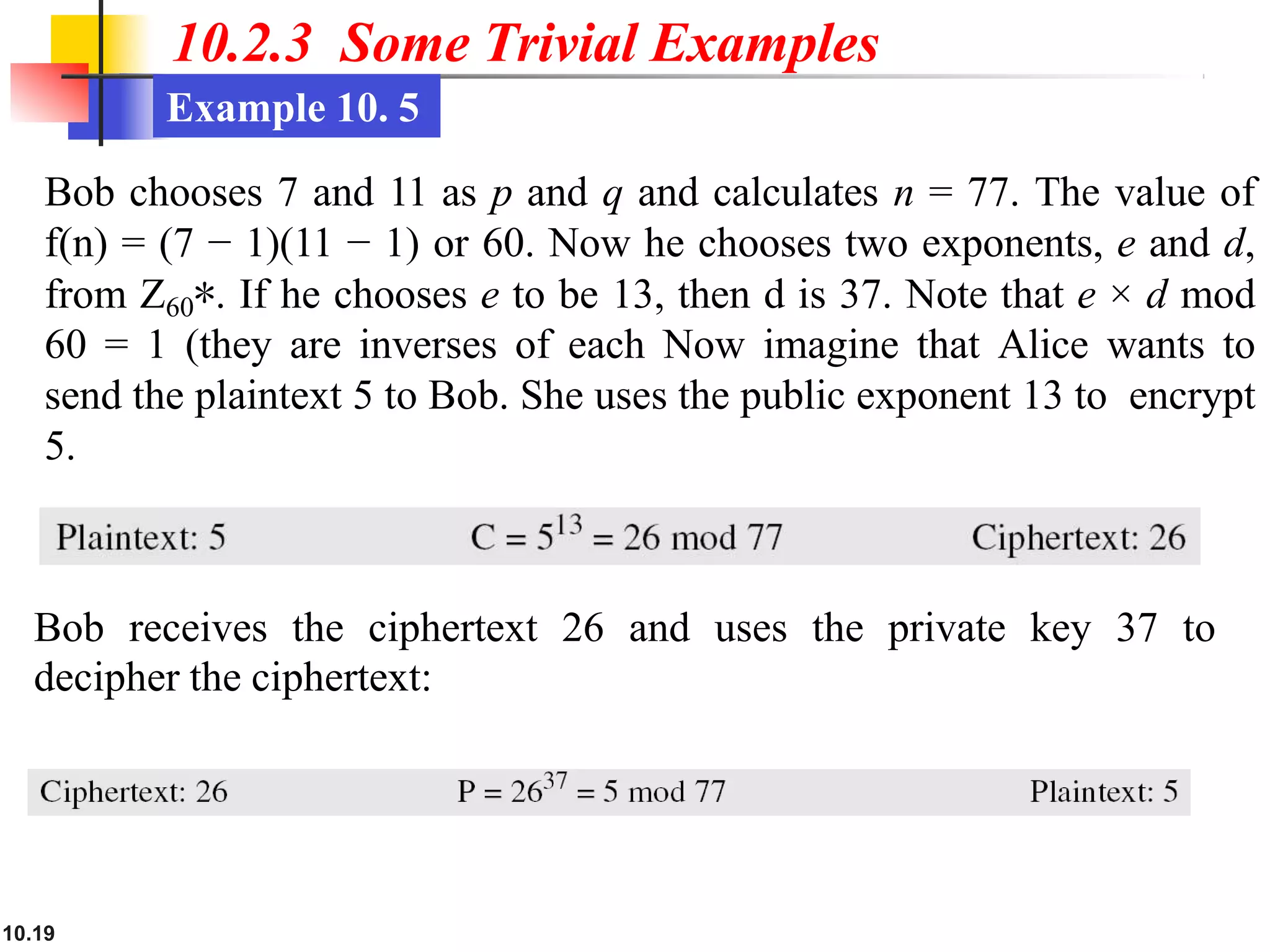
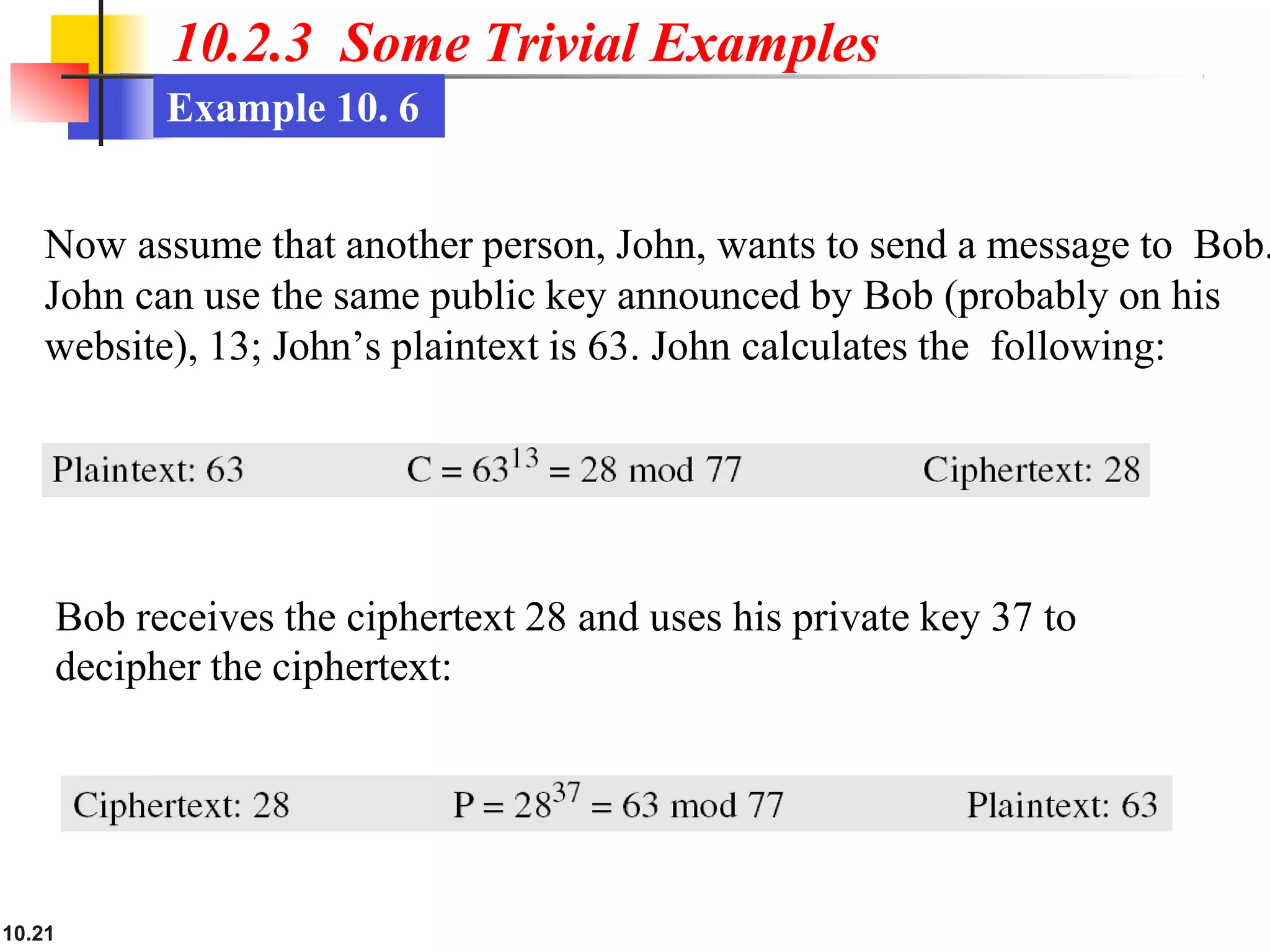
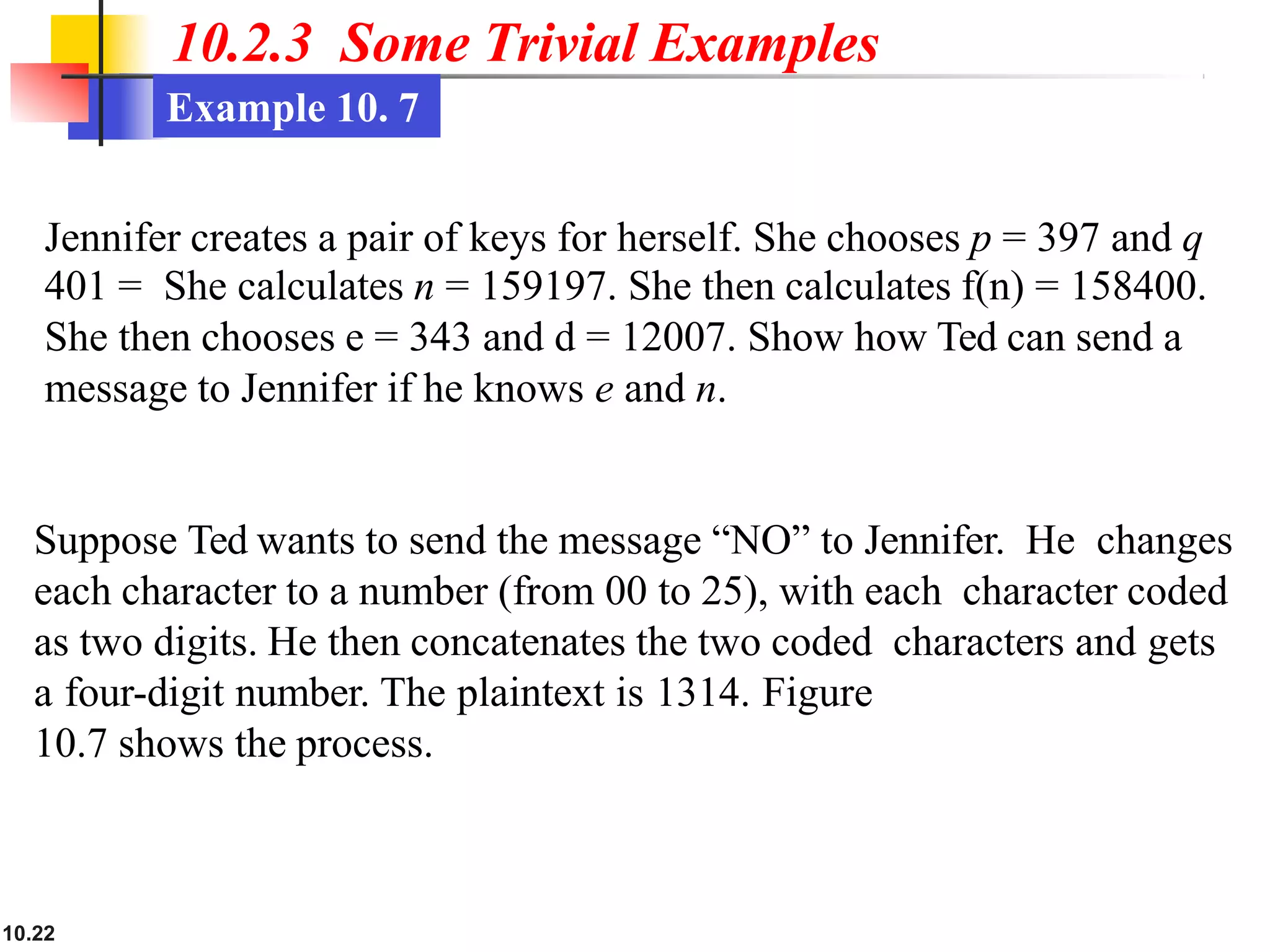
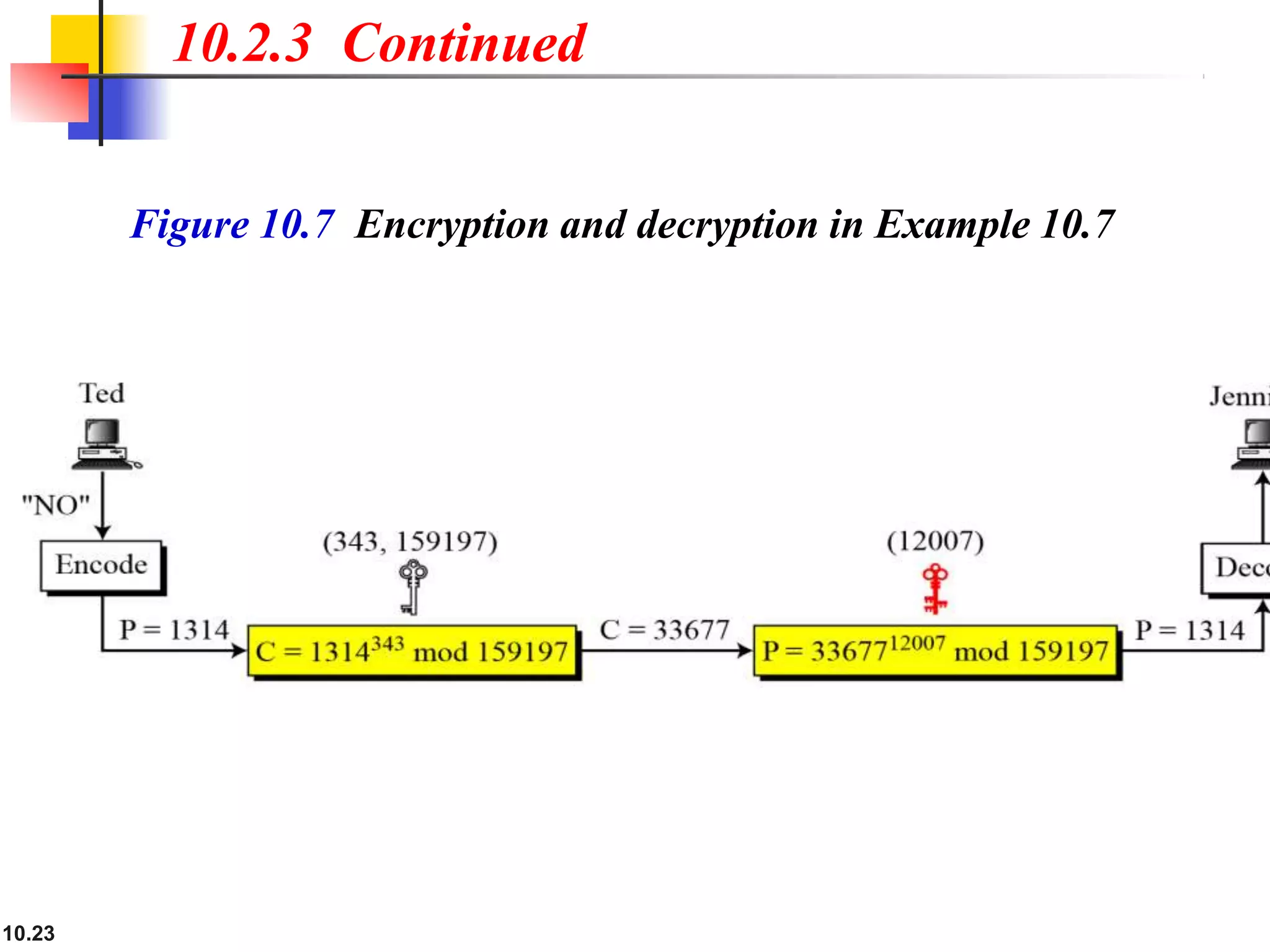
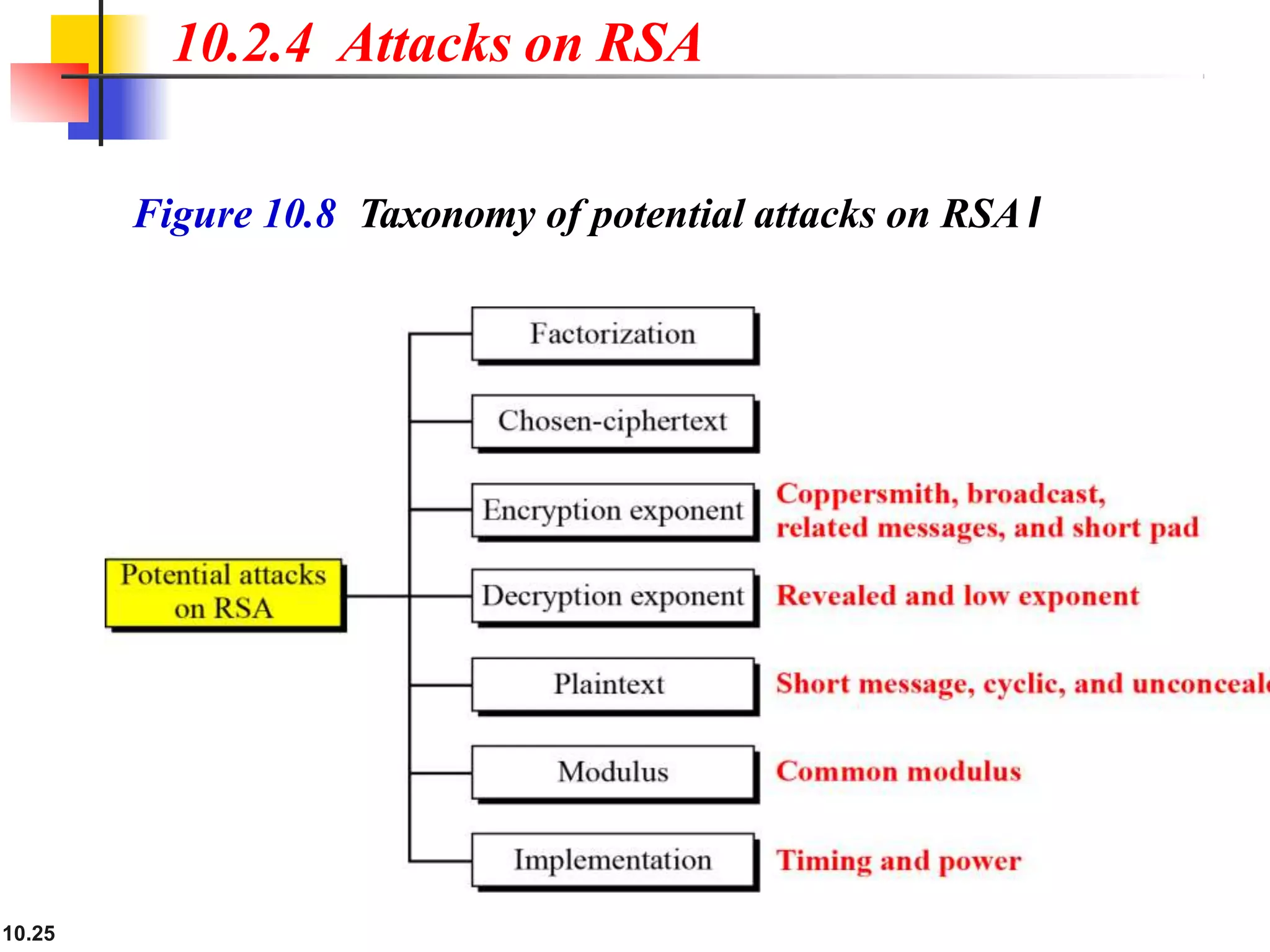
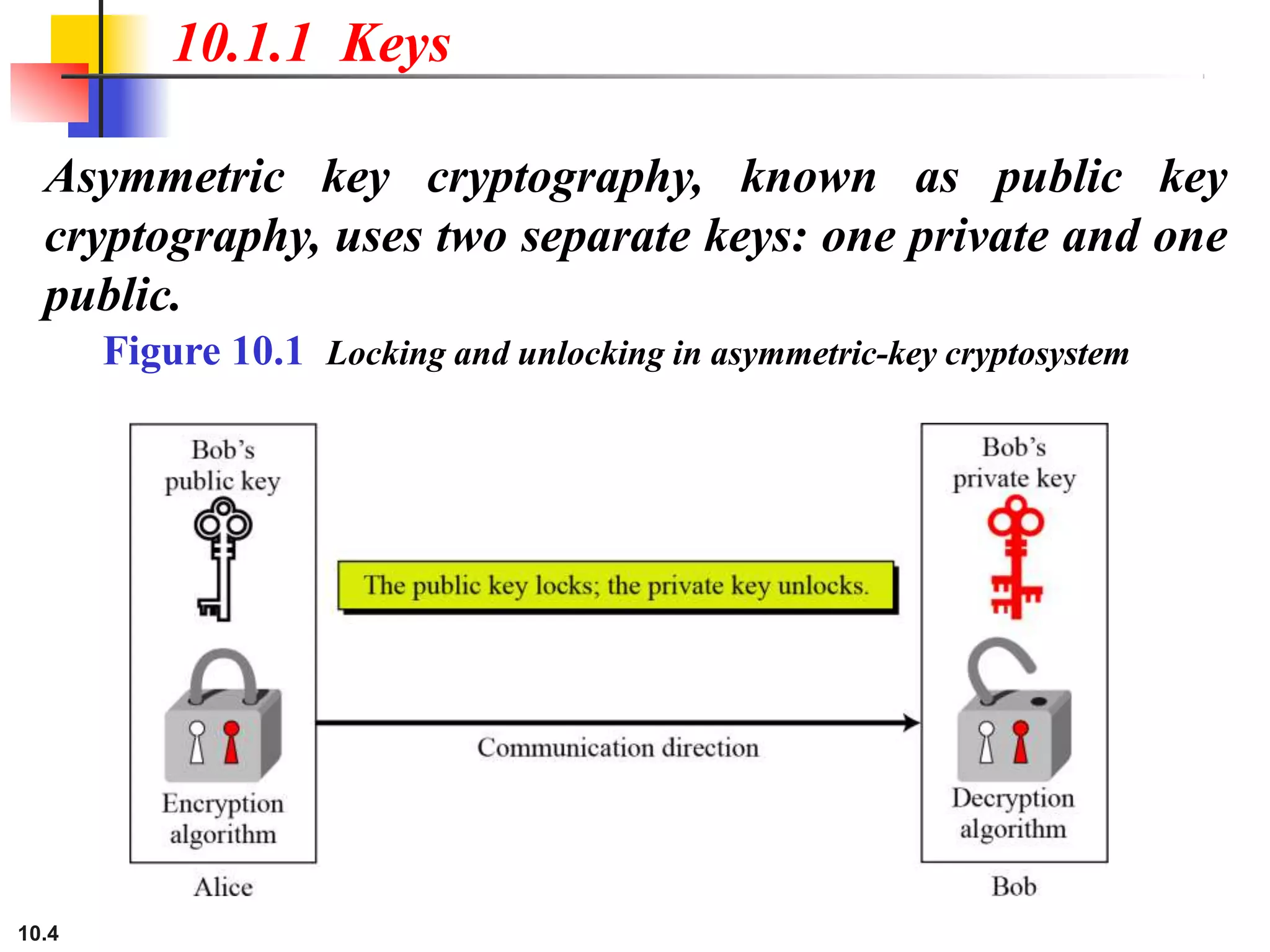
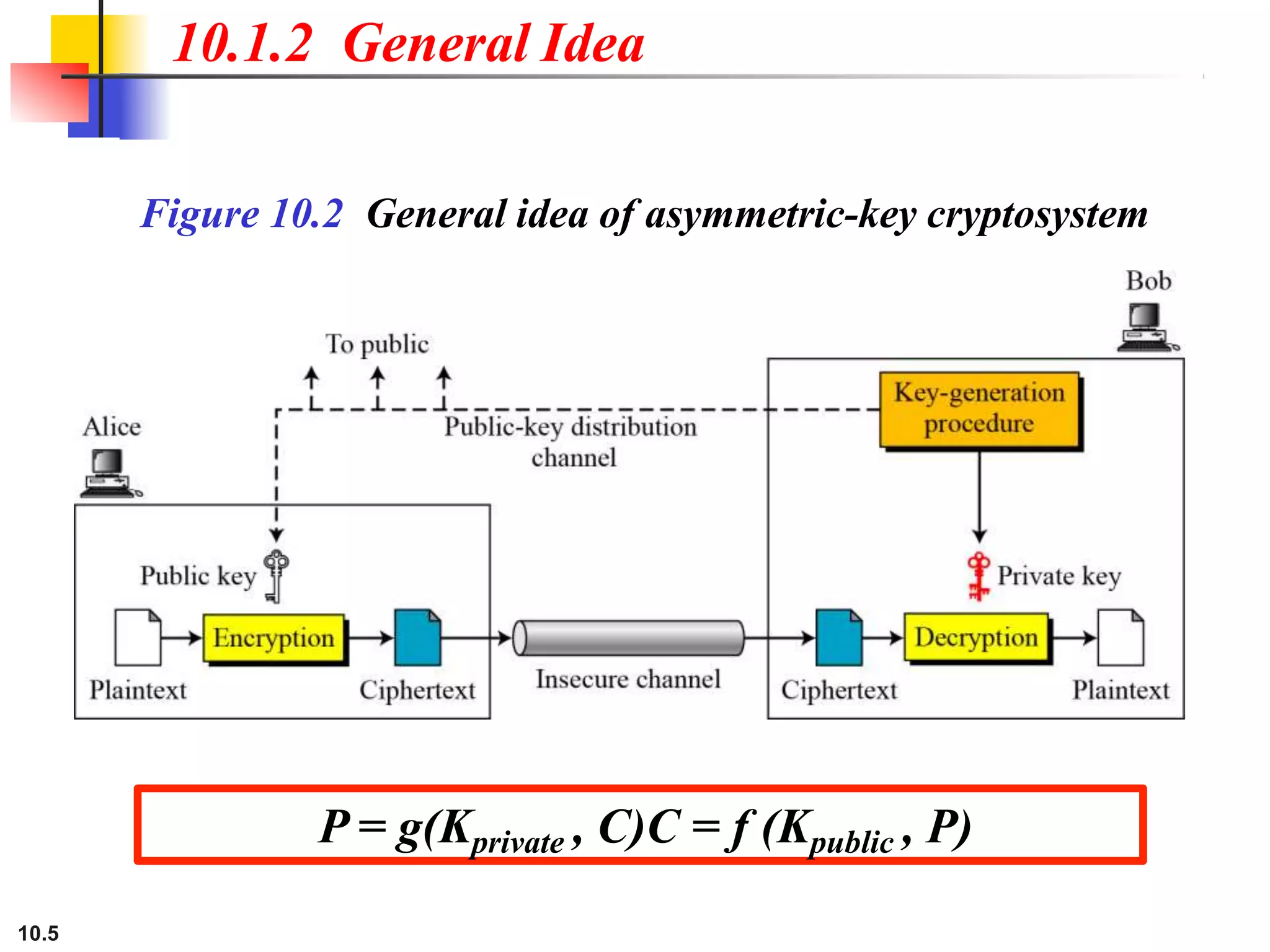
This document discusses asymmetric key cryptography and the RSA cryptosystem. It begins by distinguishing between symmetric and asymmetric key cryptography, noting they serve complementary roles. It then covers the basics of public key cryptography using two keys: a private key and public key. The RSA cryptosystem is described as the most common public key algorithm, involving key generation, encryption with the public key, and decryption with the private key. Examples are provided to illustrate the RSA process. Potential attacks on RSA like factorization are also summarized along with recommendations to strengthen security.



![Asymmetric Cryptography Practices [2]
10.6](https://image.slidesharecdn.com/7asymmetriccryptography-221231183731-eee09836/75/Asymmetric-Cryptography-pptx-6-2048.jpg)