Embed presentation
Downloaded 18 times

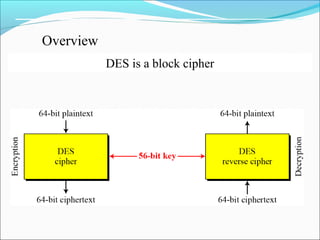

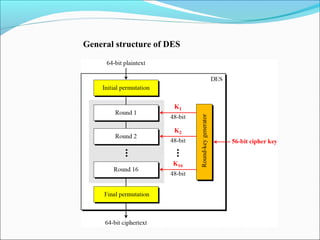
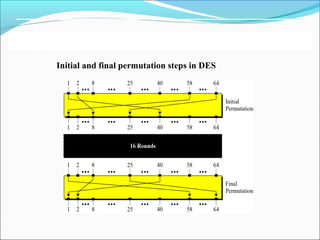
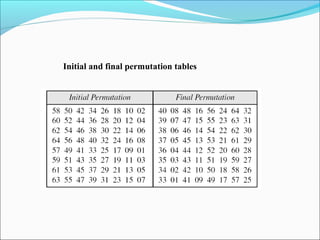

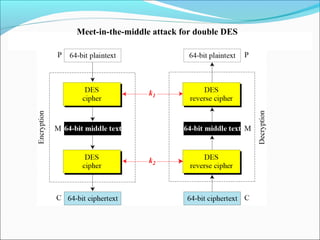

The document discusses the Data Encryption Standard (DES), which is a symmetric-key block cipher published by the National Institute of Standards and Technology (NIST). DES uses an initial and final permutation on data blocks, along with 16 rounds of permutations called Feistel rounds to encrypt data. It also discusses approaches for encrypting data using DES, such as making the last round different by removing the swapper, and how triple DES with three keys provides more security than double or single DES.









