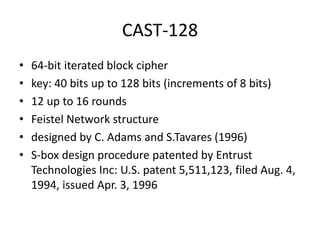
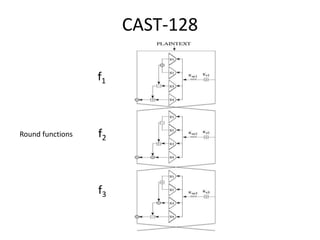
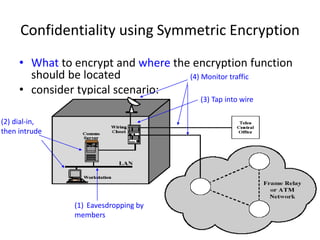
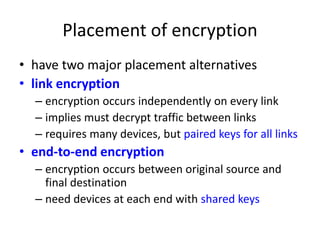
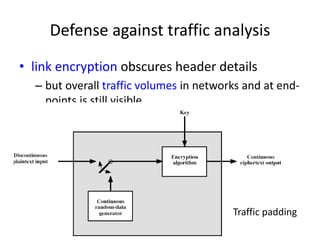
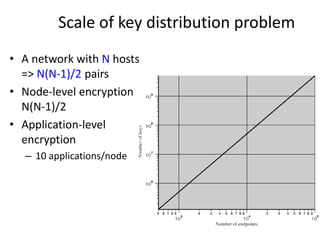
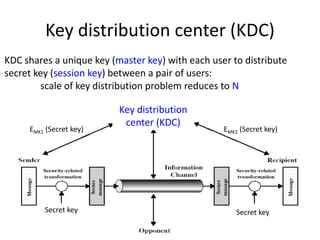
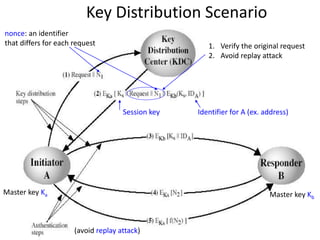
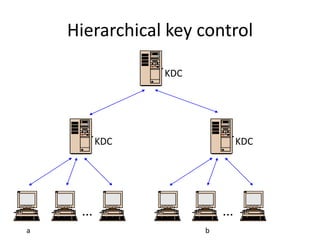
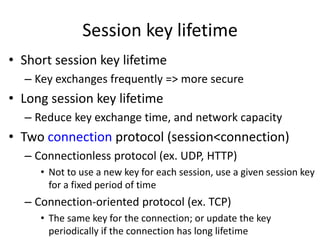
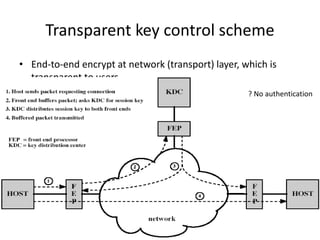
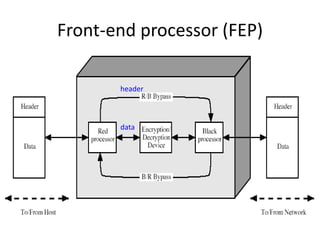
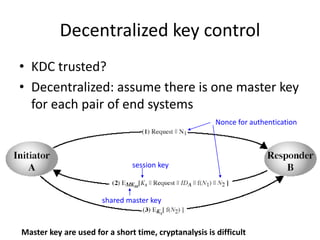
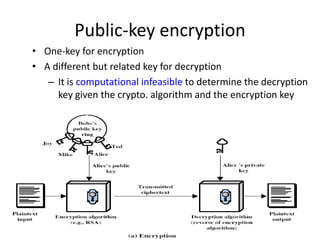
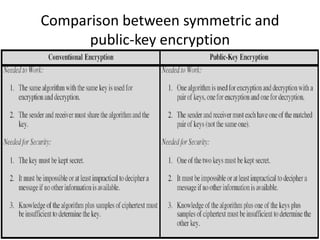
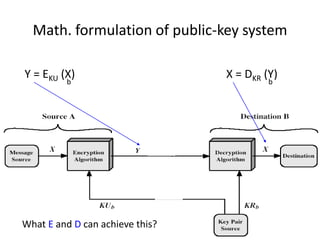
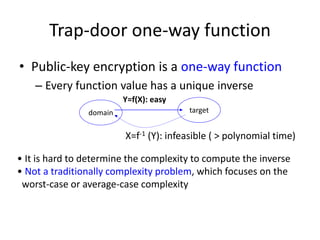
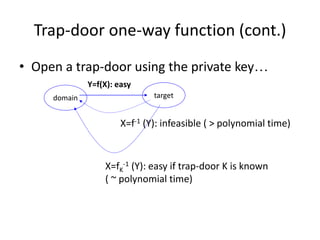
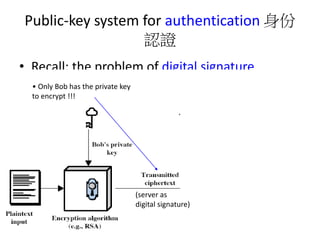
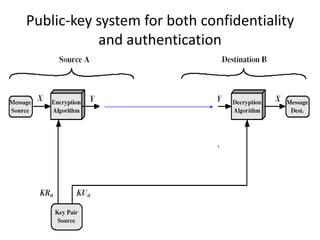
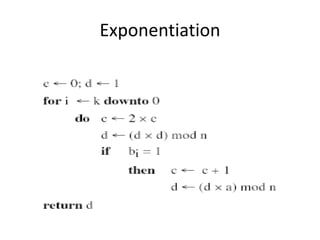
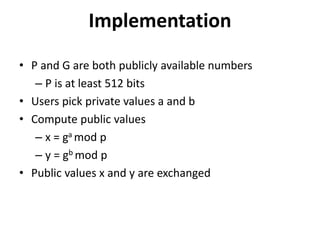
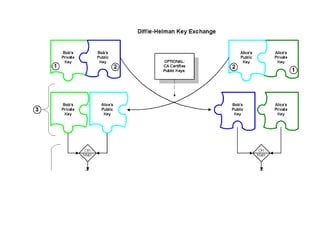
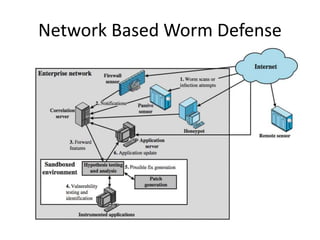
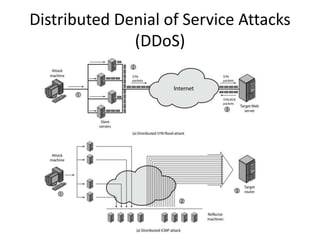
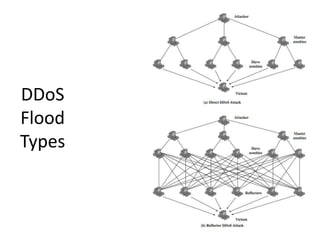
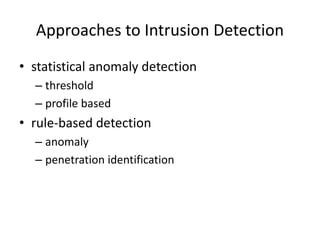
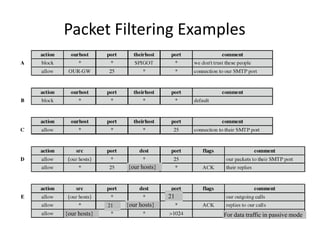
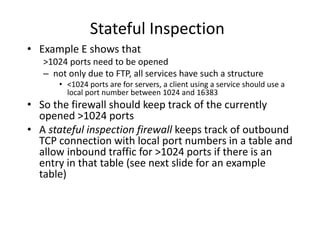
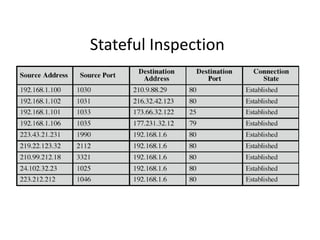
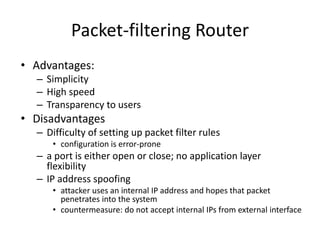
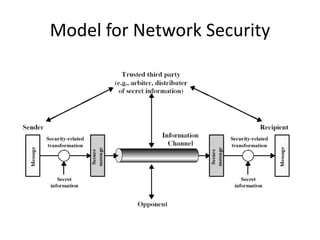
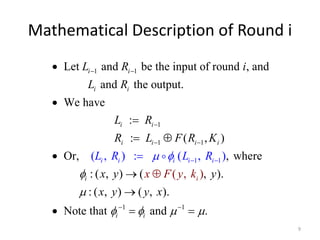
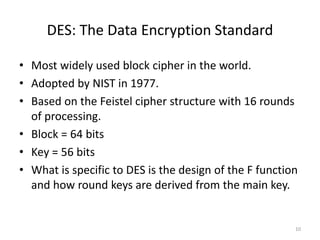
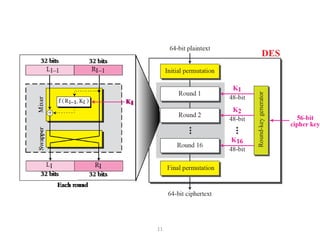
The document provides an overview of key concepts in cryptography and network security, focusing on confidentiality, integrity, and availability, along with the distinction between passive and active attacks. It dives into various encryption methods such as DES, 3DES, RC5, and Blowfish, detailing their algorithms, key management, and security features. Additionally, it discusses the importance of key distribution and placement of encryption in network design to ensure data confidentiality and protection against eavesdropping.













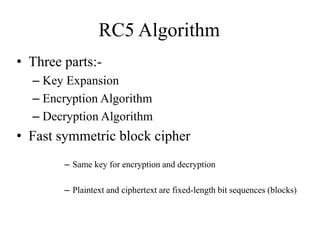


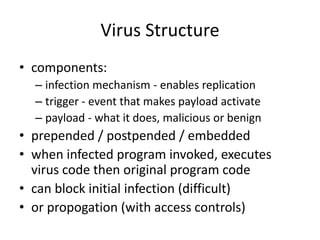
![RC5 Algorithm – Key Expansion
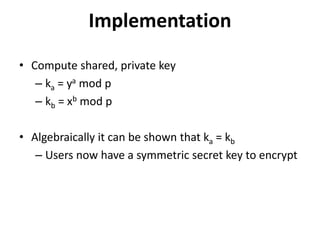
• Requirements of key expansion
– Filling the expanded key table array S[0…t – 1]
with random binary words
• “t” – Size of table “S” => 2 ( r+1 )
– S table is not an “S-box” like DES.
• Entries in S sequentially, one at a time.
– Random binary words are derived from the K.](https://image.slidesharecdn.com/presentation1-141119103935-conversion-gate01/85/Overview-on-Cryptography-and-Network-Security-28-320.jpg)
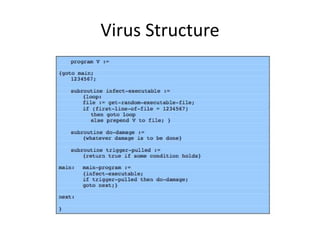
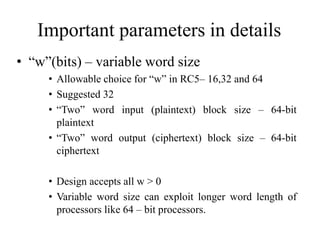
![RC5 Algorithm
• Encryption Algorithm
– Two w-bit words are denoted as A and B
A = A + S[0];
B = B + S[1];
for i = 1 to r do
A = (( A ⊕ B ) <<< B ) + S[ 2 * i ];
B = (( B ⊕ A) <<< A ) + S[ 2 * i + 1];
The output is in the registers A and B.
Work is done on both A and B, unlike DES
where only half input is updated.](https://image.slidesharecdn.com/presentation1-141119103935-conversion-gate01/85/Overview-on-Cryptography-and-Network-Security-29-320.jpg)
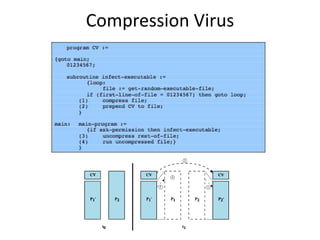
![RC5 Algorithm
• Decryption Algorithm
– (easily derived from encryption)
– Two w-bit words are denoted as A and B
for i = r downto 1 do
B = (( B – S[ 2 * i + 1 ]) >>> A) ⊕ A;
A = (( A – S[ 2 * i ] >>> B) ⊕ B;
B = B - S[1];
A = A - S[0];
The output is in the registers A and B.](https://image.slidesharecdn.com/presentation1-141119103935-conversion-gate01/85/Overview-on-Cryptography-and-Network-Security-30-320.jpg)
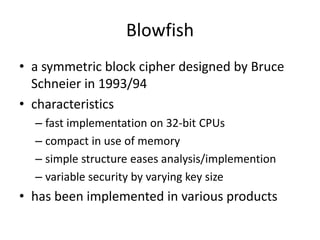

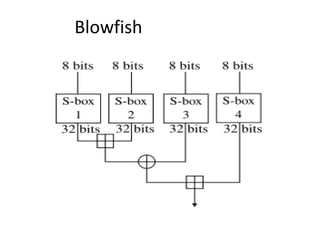
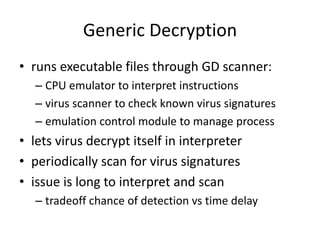
![Blowfish Encryption
• uses two primitives: addition & XOR
• data is divided into two 32-bit halves L0 & R0
for i = 1 to 16 do
Ri = Li-1 XOR Pi;
Li = F[Ri] XOR Ri-1;
L17 = R16 XOR P18;
R17 = L16 XOR i17;
• where
F[a,b,c,d] = ((S1,a + S2,b) XOR S3,c) + S4,a](https://image.slidesharecdn.com/presentation1-141119103935-conversion-gate01/85/Overview-on-Cryptography-and-Network-Security-34-320.jpg)