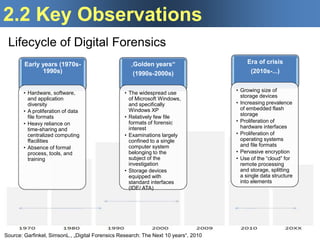
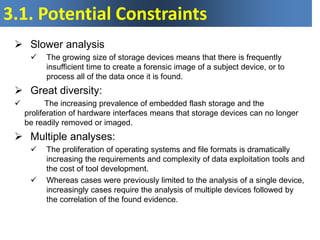
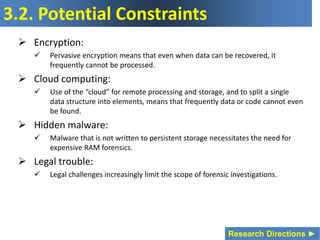
The document presents a presentation on digital forensics research, outlining objectives and key observations regarding the field's evolution, challenges, and research directions for the next decade. It emphasizes the need for improved methodologies to address technological advancements, legal constraints, and the complexity of digital evidence gathering. It highlights critical issues such as the impact of encryption, cloud computing, and the lack of standard tools, particularly for mobile devices, which impede effective forensic analysis.