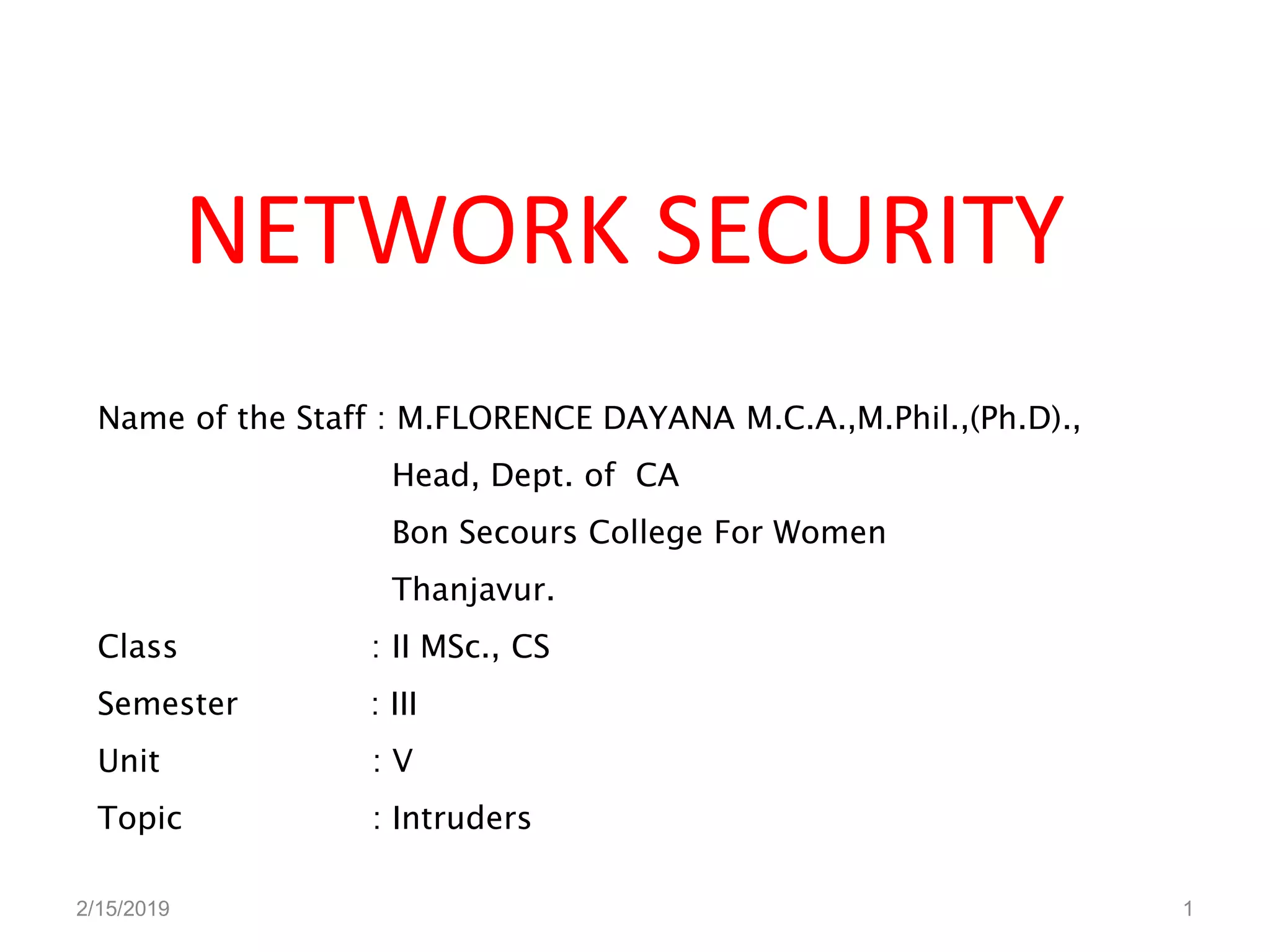
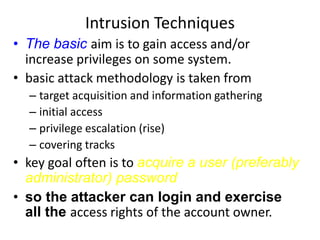
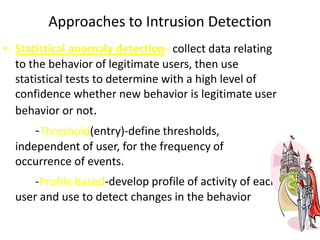
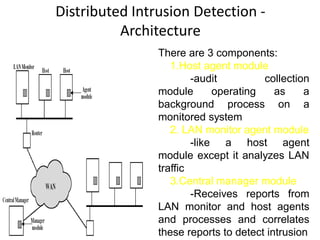
The document discusses network security, focusing on intruders and their classification, including masqueraders, misfeasors, and clandestine users. It outlines intrusion techniques, detection methods, and the importance of maintaining audit records for monitoring user activity, as well as strategies for password management to prevent unauthorized access. Key concepts include the design of distributed intrusion detection systems and the use of honeypots to lure and analyze attackers.