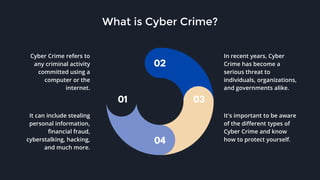
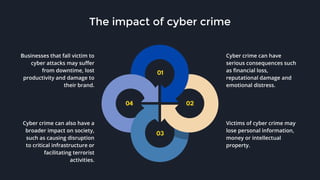
This presentation by Mehedi Hasan raises awareness about cyber crime, highlighting its various forms such as malware, phishing, identity theft, and hacking, which pose significant risks to individuals, businesses, and governments. It emphasizes the importance of taking proactive measures to protect oneself online, including using strong passwords, enabling two-factor authentication, and staying informed about current threats. Overall, the presentation aims to educate the audience on cyber crime's impact and the strategies to mitigate risks associated with it.