Digital Forensics: Analyzing Cyber Crimes & Investigations
This comprehensive guide on Digital Forensics covers key concepts, tools, and methodologies used in investigating cyber crimes. It explores forensic techniques, evidence collection, data recovery, malware analysis, and incident response with real-world applications.
Topics Covered:
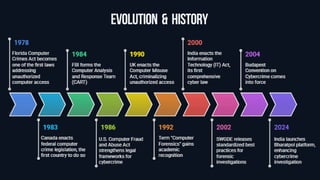
Introduction to Digital Forensics
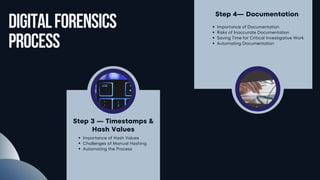
Cybercrime Investigation Process
Digital Evidence & Chain of Custody
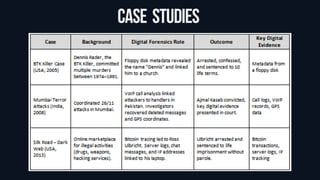
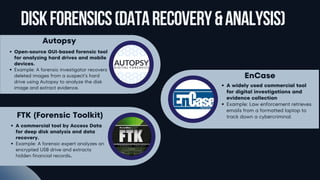
Popular Forensic Tools (Autopsy, EnCase, FTK)
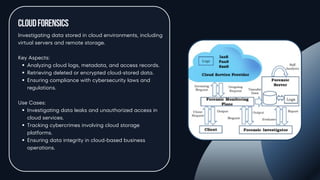
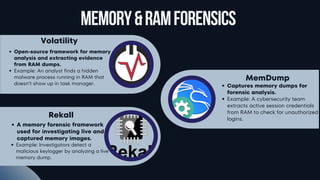
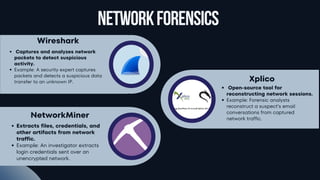
Memory & Network Forensics
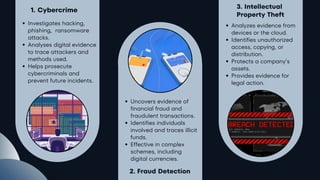
Challenges in Modern Cyber Investigations
Ideal for students, cybersecurity professionals, and forensic analysts, this resource provides valuable insights into digital investigations.