Embed presentation




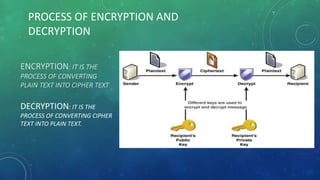


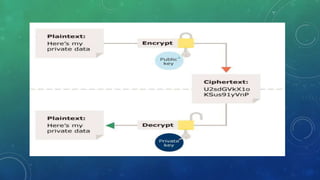

Encryption is the process of converting a readable plaintext message into an unreadable cipher text message. Decryption is the reverse process of converting cipher text back into a readable plaintext format. The encryption process uses a public key at the sender's end to encrypt the message into unreadable cipher text. Decryption uses a private key at the receiver's end to decode the cipher text back into the original readable plaintext message. Encryption and decryption ensure secure transmission and storage of sensitive data that can only be accessed by authorized parties with the proper keys.








