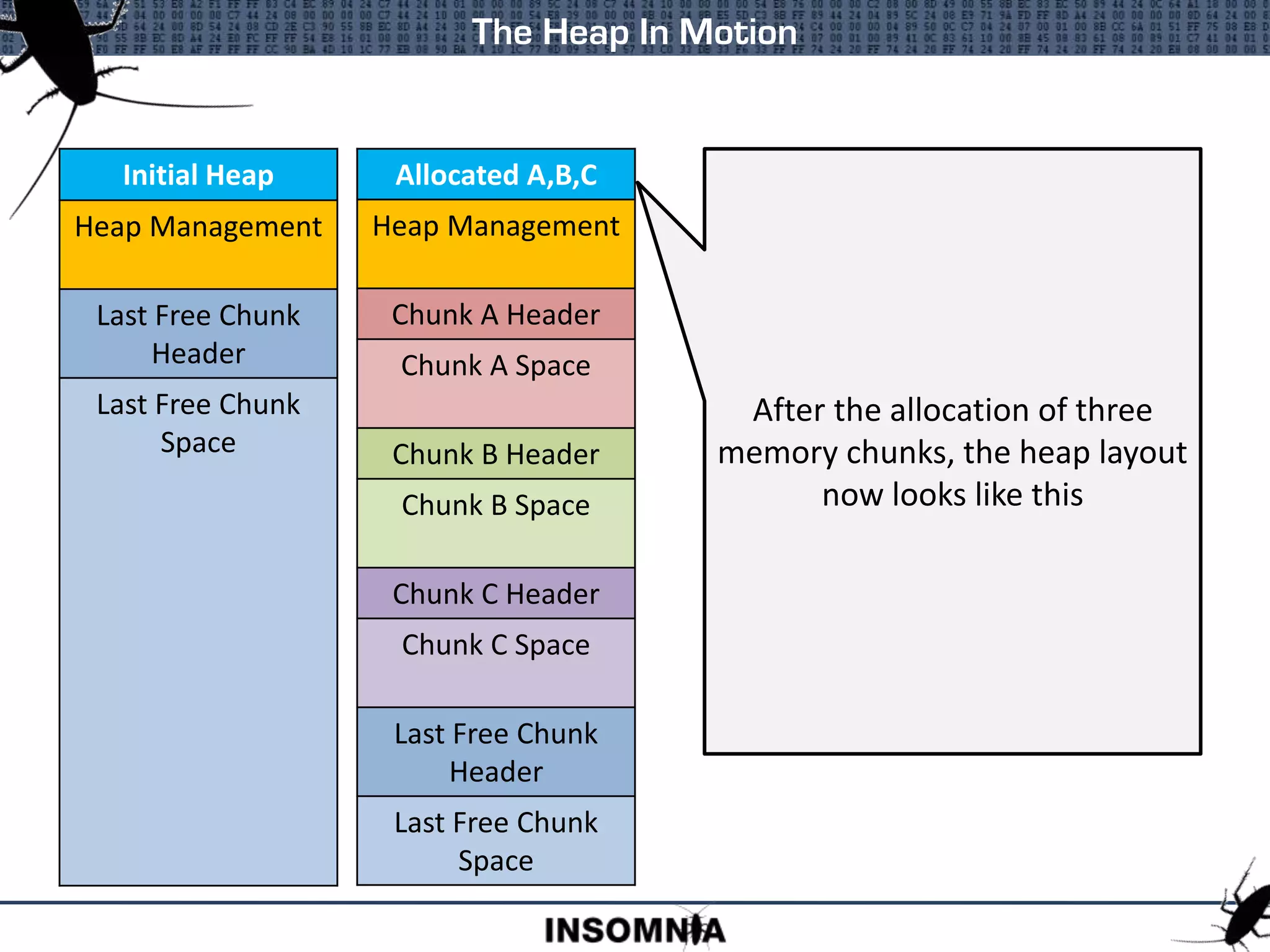
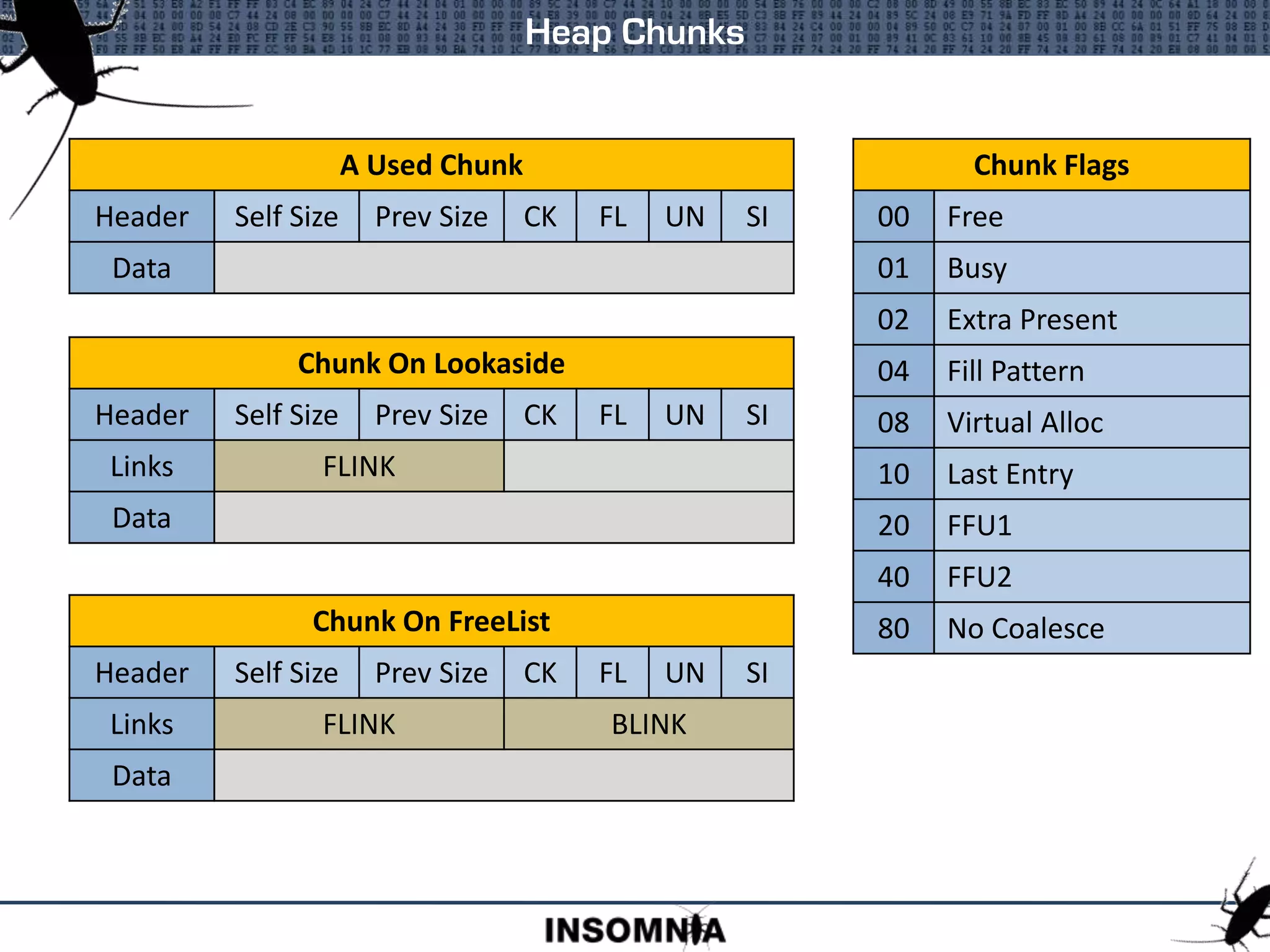
This document discusses Windows 2003 heap exploitation techniques. It begins with an overview of heaps and the Windows 2003 heap structure. It then covers the heap management structure, free lists, lookaside lists, and techniques for manipulating various heap structures like the free list bitmap and size field to enable overwriting arbitrary memory locations. Key points covered include safe unlinking, cookie checks, and how overwriting links in free lists or lookaside lists can lead to memory corruption.



![Heap Management Structure
Heap Management
Address Value Description
00360000 Base Address
0036000C 00000002 Flags
00360010 00000000 ForceFlags
00360014 0000FE00 VirtualMemoryThreshold
00360050 00360050 VirtualAllocatedBlocks List
00360158 00000000 FreeList Bitmap
00360178 00361E90 FreeList[0]
00360180 00360180 FreeList[n]
00360578 00360608 HeapLockSection
0036057C 00000000 Commit Routine Ptr
00360580 00360688 FrontEndHeap
00360586 00000001 FrontEndHeapType
00360678 00361E88 Last Free Chunk
00360688 00000000 Lookaside[n]
All offsets are from the
base of the Heap Object
These Flags hold settings
such as isDebug, Exception
Raising, and Executable
Heap
The maximum size of an
allocation before a Virtual
Memory allocation is
performed
Linked list of blocks
allocated from Virtual
Memory
A four DWORD bitmask
with each bit set if the
corresponding FreeList[n] is
populated
Pointer to the first chunk in
FreeList[0]
FreeList[0] is used to store
Free Chunks > 1016 bytes
Start of double linked lists
to store Free Chunks
Pointer to CriticalSection
that is used to lock the
heap during changes
Pointer to Function() that is
called when the heap is
expanded and more pages
committed
Pointer to the front end
allocator.
This is a pointer to the
Lookaside
Flag that stores settings
about the front end
allocator
Pointer to the Last Free
Chunk in the heap
Start of the 48 byte
Lookaside list headers](https://image.slidesharecdn.com/heapsaboutheaps-brettmoore-221027142032-3e092f7b/75/Heaps-About-Heaps-Brett-Moore-ppt-9-2048.jpg)
![Heap Management Structure - Virtual Memory Allocation
Heap Management
Address Value Description
00360014 0000FE00 VirtualMemoryThreshold
00360050 00360050 VirtualAllocatedBlocks List
00360050 FLINK
00360054 BLINK
7C82AE14 CMP EDI,DWORD PTR DS:[EBX+14]
7C82AE17 JBE ntdll.7C82A2FC
...
7C82AE8E LEA EAX,DWORD PTR DS:[EBX+50]
...
7C82AE97 MOV EDX,DWORD PTR DS:[EAX+4]
...
7C82AEA0 MOV DWORD PTR DS:[ECX],EAX
7C82AEA2 MOV DWORD PTR DS:[ECX+4],EDX
7C82AEA5 MOV DWORD PTR DS:[EDX],ECX
7C82AEA7 MOV DWORD PTR DS:[EAX+4],ECX
EBX is set to Base Address
Check threshold
Load BLINK
Write @NewChunk to
@BLINK+4
ECX is @NewChunk
If the VirtualAllocatedBlocks->BLINK can be overwritten then the address of
the NewChunk can be written to an arbitrary location](https://image.slidesharecdn.com/heapsaboutheaps-brettmoore-221027142032-3e092f7b/75/Heaps-About-Heaps-Brett-Moore-ppt-10-2048.jpg)
![Heap Management Structure - FreeList Bitmap
Heap Management
Address Value Description
00360158 00000000 FreeList Bitmap
7C82A291 LEA ESI,DWORD PTR DS:[EBX+EDX*4+158]
...
7C82A2A8 AND EAX,DWORD PTR DS:[ESI]
...
7C82A2B8 JNZ ntdll.7C82CB46
7C82A2BE TEST EAX,EAX
7C82A2C0 JNZ ntdll.7C82C8C9
7C82A2C6 MOV EAX,DWORD PTR DS:[ESI]
Bitmap is checked when
looking for a FreeList[n]
that fits the request
Bitmap is populated when
chunk added to FreeList[n]
If a match is found then the
corresponding FreeList[n] is
used for the allocation.
If the Bitmap can be manipulated then a pointer to an empty FreeList[n] can
be returned, allowing the overwrite of management structures. [nico]
80 00 00 02 00 00 80 00 00 00 00 00 00 00 00 00
0-7 24-31 48-55](https://image.slidesharecdn.com/heapsaboutheaps-brettmoore-221027142032-3e092f7b/75/Heaps-About-Heaps-Brett-Moore-ppt-11-2048.jpg)
![Heap Management Structure - FreeList Bitmap
Heap Management
Address Value Description
00360158 00000000 FreeList Bitmap
If the Bitmap can be manipulated then a pointer to an empty FreeList[n] can
be returned, allowing the overwrite of management structures. [nico]
80 00 00 02 00 00 80 00 00 00 00 00 00 00 00 00
FreeList[7] is
populated
FreeList[16] is
empty
FreeLists
Address Value Description
003601B0 00364D78 FreeList[7]
... ... ...
003601F8 003601F8 FreeList[16]
Request for block 16 will
create a new block and
return it
Modify bitmap
Request for block 16 will
return 003601F8
80 00 01 02 00 00 80 00 00 00 00 00 00 00 00 00
FreeLists
Address Value Description
003601B0 00364D78 FreeList[7]
... ... ...
003601F8 XXXXXXXX Overwrite
XXXXXXXX Overwrite
XXXXXXXX Overwrite
XXXXXXXX Overwrite
XXXXXXXX Overwrite](https://image.slidesharecdn.com/heapsaboutheaps-brettmoore-221027142032-3e092f7b/75/Heaps-About-Heaps-Brett-Moore-ppt-12-2048.jpg)
![Heap Management Structure - FreeList Bitmap
If the Bitmap can be manipulated then a pointer to an empty FreeList[n] can
be returned, allowing the overwrite of management structures. [nico]
Part Of The Bitmap Loading Code
7C82C8AB MOVZX EAX,AH
7C82C8AE MOVSX EAX,BYTE PTR DS:[EAX+7C82BAB8]
7C82C8B5 ADD EAX,8
7C82C8B8 JMP ntdll.7C82C830
7C82C8BD MOVSX EAX,BYTE PTR DS:[ECX+7C82BAB8]
7C82C8C4 JMP ntdll.7C82C830
7C82C8C9 LEA EDX,DWORD PTR DS:[EBX+178]
7C82C8CF JMP ntdll.7C82C808
7C82C8D4 SHR EAX,18
7C82C8D7 MOVSX EAX,BYTE PTR DS:[EAX+7C82BAB8]
7C82C8DE ADD EAX,18
7C82C8E1 JMP ntdll.7C82C830
[ 7C82BAB8 ]
A Static Pointer To A Bit
Mask Table That Can Be
Modified To Manipulate
The Bitmap Result](https://image.slidesharecdn.com/heapsaboutheaps-brettmoore-221027142032-3e092f7b/75/Heaps-About-Heaps-Brett-Moore-ppt-13-2048.jpg)
![Heap Management Structure – FreeList[n]
Heap Management
Address Value Description
00360178 00361e90 FreeList[0]
00360180 00360180 FreeList[n]
FreeList[0] is similar to
FreeList[n] but holds
chunks > 1016 bytes
00360180 FLINK
00360184 BLINK
Free Chunk Header
Header Self Size Prev Size CK FL UN SI
Links FLINK BLINK
Free Chunk Header
Header Self Size Prev Size CK FL UN SI
Links FLINK BLINK
Double Linked List
connects free
chunks together](https://image.slidesharecdn.com/heapsaboutheaps-brettmoore-221027142032-3e092f7b/75/Heaps-About-Heaps-Brett-Moore-ppt-14-2048.jpg)
![Heap Management Structure - Commit Routine Pointer
Heap Management
Address Value Description
0036057C 00000000 Commit Routine Ptr
7C833BF9 MOV ECX,DWORD PTR DS:[EAX+57C]
7C833BFF TEST ECX,ECX
7C833C01 JNZ ntdll.7C852C9E
...
7C852C9E PUSH EBX
7C852C9F LEA EDX,DWORD PTR SS:[EBP+14]
7C852CA2 PUSH EDX
7C852CA3 PUSH EAX
7C852CA4 CALL ECX
Initially set to nothing
Custom function() called
when committing more
memory to the Heap
This is a static pointer that can be overwritten to gain execution control
Loaded into ECX and called](https://image.slidesharecdn.com/heapsaboutheaps-brettmoore-221027142032-3e092f7b/75/Heaps-About-Heaps-Brett-Moore-ppt-15-2048.jpg)
![Heap Management Structure – Lookaside[n]
Heap Management
Address Value Description
00360688 00000000 Lookaside[n]
003606E8 Lookaside[2]
Lookaside[0] and
Lookaside[1] are not used
48 byte structure
Lookaside List Header
Address Description
+00 Pointer To First Chunk
+04 Depth
+06 Max Depth
+08
Allocation tracking for
automatic Lookaside
Fine Tuning
+0C
+10
...
Lookaside Chunk Header
Header Self Size Prev Size CK FL UN SI
Links FLINK
Lookaside Chunk Header
Header Self Size Prev Size CK FL UN SI
Links FLINK](https://image.slidesharecdn.com/heapsaboutheaps-brettmoore-221027142032-3e092f7b/75/Heaps-About-Heaps-Brett-Moore-ppt-16-2048.jpg)
![Lookaside Lists
Lookaside[n]
FLINK 00000000
Lookaside Starts
Empty
Address FLINK
003620D0 00000000
Lookaside[n]
FLINK 003620D0
Chunk Added To
Top Of Lookaside
Address FLINK
003620E8 003620D0
Lookaside[n]
FLINK 003620E8
Chunk Added To
Top Of Lookaside
Address FLINK
003620D0 00000000
Address FLINK
00362100 003620E8
Lookaside[n]
FLINK 00362100
Chunk Added To
Top Of Lookaside
Address FLINK
003620E8 003620D0
Address FLINK
003620D0 00000000
About To Allocate From The
Lookaside[n]
This Value Gets
Copied
Address FLINK
00362100 003620E8
Lookaside[n]
FLINK 00362100
Address FLINK
003620E8 003620D0
Address FLINK
003620D0 00000000
Chunk Removed From
Top Of Lookaside
Lookaside[n]
FLINK 003620E8
Address FLINK
003620E8 003620D0
Address FLINK
003620D0 00000000
Copied To Here
There is no Safe Unlinking or Cookie check for Lookaside Lists
Well known attack is to overwrite the FLINK of a chunk on a Lookaside. This
will populate the Lookaside[n]->FLINK with an arbitrary value to be returned
at allocation.
Overwrite the FLINK of the
top chunk
Lookaside[n]
FLINK 003620E8
Address FLINK
003620E8 XXXXXXXX
Address FLINK
003620D0 00000000
Lookaside[n]->FLINK
is corrupted
Lookaside[n]
FLINK XXXXXXXX](https://image.slidesharecdn.com/heapsaboutheaps-brettmoore-221027142032-3e092f7b/75/Heaps-About-Heaps-Brett-Moore-ppt-18-2048.jpg)
![Freelist[n] Lists
Lookaside[n]
FLINK 00000000
Freelist Starts
Empty
Lookaside[n]
FLINK 003620D0
Lookaside[n]
FLINK 003620E8
Lookaside[n]
FLINK 00362100
Lookaside[n]
FLINK 00362100
Lookaside[n]
FLINK 003620E8
Safe Unlinking and Cookie checks will prevent Unlinking
Overwriting the Freelist[n]->BLINK will cause the address of the Free’d Chunk
to be written to an arbitrary location
Lookaside[n]
FLINK 003620E8
Freelist[n]
Address FLINK BLINK
00360190 00360190 00360190
Address FLINK BLINK
00362130 00360190 00360190
Chunk Added To
Bottom
Freelist[n]
Address FLINK BLINK
00360190 00362130 00362130
Address FLINK BLINK
00362160 00360190 00362130
Chunk Added To
Bottom
Freelist[n]
Address FLINK BLINK
00360190 00362130 00362160
Address FLINK BLINK
00362130 00362160 00360190
Chunk Removed
From Bottom
Freelist[n]
Address FLINK BLINK
00360190 00362130 00362130
Address FLINK BLINK
00362130 00360190 00360190
Freelist Is Empty](https://image.slidesharecdn.com/heapsaboutheaps-brettmoore-221027142032-3e092f7b/75/Heaps-About-Heaps-Brett-Moore-ppt-19-2048.jpg)
![Freelist[n] Lists
Freelist Searching
: If a freelist[n] of requested size not available
bitmap is used to find larger populated freelist[n]
Chunk Size
: Size field of the chunk header used as offset to bitmap
: Bitmap is updated on allocate/free if needed
: Size field is used to calculate freelist[n] to free to
Manipulating Size Field
: Allocation can control bitmap flipping
: Free can have chunk free’d to different lookaside/freelist
Header Self Size Prev Size CK FL UN SI](https://image.slidesharecdn.com/heapsaboutheaps-brettmoore-221027142032-3e092f7b/75/Heaps-About-Heaps-Brett-Moore-ppt-20-2048.jpg)
![Flipping Bitmap On Allocate
Size Is Overwritten
FLINK / BLINK Can Be
Overwritten
7C82C8E6 MOVZX ECX,WORD PTR DS:[ESI] ; Load Self Size
7C82C8E9 MOV EDX,ECX
..
7C82C902 8DBC1A 58010000 LEA EDI,DWORD PTR DS:[EDX+EBX+158]
Calculate Bitmap
Bitmap Attack Explained Earlier
Chunk On FreeList
Header #### Prev Size CK FL UN SI
Links FLINK BLINK
Data
If Last Chunk On Freelist Then Bitmap Updated
If FLINK and BLINK Overwritten with
Valid For Read and
FLINK == BLINK
Then Bitmap Updated](https://image.slidesharecdn.com/heapsaboutheaps-brettmoore-221027142032-3e092f7b/75/Heaps-About-Heaps-Brett-Moore-ppt-21-2048.jpg)
![Free To Arbitrary Lookaside[n]/FreeList[n]
Size Is Overwritten
Cookie Is Left Intact
Chunk To Be Freed
Header #### Prev Size CK FL UN SI
Data
7C829F1B MOVZX EAX,WORD PTR DS:[ESI] ; Load self size
7C829F1E MOV DWORD PTR SS:[EBP-20],EAX
7C829F21 CMP EAX,80
7C829F26 JNB ntdll.7C82A7BC
7C829F2C PUSH DWORD PTR SS:[EBP+10]
7C829F2F LEA EAX,DWORD PTR DS:[EAX+EAX*2] ; Calculate Lookaside
7C829F32 SHL EAX,4
7C829F35 ADD EAX,ECX
7C829F37 PUSH EAX
7C829F38 CALL ntdll.7C829F8F ; Push to Lookaside
Freeing To
Lookaside[n]
Could This Be Useful When Filling In Gaps?
7C82A84C MOVZX EAX,WORD PTR SS:[EBP-20] ; Load selfsize
7C82A850 LEA EBX,DWORD PTR DS:[EDI+EAX*8+178] ; Calculate
7C82A857 MOV DWORD PTR SS:[EBP-88],EBX
7C82A85D CMP DWORD PTR DS:[EBX],EBX ; Check Freelist
Freeing To
Freelist[n]
Coalescing Is A Problem That Needs To Be Dealt With](https://image.slidesharecdn.com/heapsaboutheaps-brettmoore-221027142032-3e092f7b/75/Heaps-About-Heaps-Brett-Moore-ppt-22-2048.jpg)
![FreeList[0] - Free
Address FLINK BLINK
00361E90 003622D0 00360178
Freelist[0]
Address FLINK BLINK
00360178 00361E90 00362B60
Address FLINK BLINK
003622D0 00362B60 00361E90
Address FLINK BLINK
00362B60 00360178 003622D0
Populated
Freelist[0]
Load Freelist[0]->FLINK
Check Size Is Larger Than
Chunk Been Free’d
Not Greater, Load
Chunk->FLINK
Check Size Is Great Than
Chunk Been Free’d
If It Is Greater Then
Insert Chunk
Exploitable Condition On Freelist[0] Insert](https://image.slidesharecdn.com/heapsaboutheaps-brettmoore-221027142032-3e092f7b/75/Heaps-About-Heaps-Brett-Moore-ppt-23-2048.jpg)
![Exploiting FreeList[0] - Free
Exploitable Condition On Freelist[0] Insert
7C82A982 CMP DX,WORD PTR DS:[EAX] ; Compare chunk size
7C82A985 JA ntdll.7C82FDC4 ; To large move to next
7C82A98B LEA EAX,DWORD PTR DS:[ESI+8] ; Header of free’d chunk
7C82A98E MOV DWORD PTR SS:[EBP-7C],EAX
7C82A991 MOV EDX,DWORD PTR DS:[ECX+4] ; Load BLINK of current chunk
7C82A994 MOV DWORD PTR SS:[EBP-84],EDX
7C82A99A MOV DWORD PTR DS:[EAX],ECX ; Set free’d->FLINK == current
7C82A99C MOV DWORD PTR DS:[EAX+4],EDX ; Set free’d->BLINK ==current->BLINK
7C82A99F MOV DWORD PTR DS:[EDX],EAX ; Write @free’d to [current->BLINK]
7C82A9A1 MOV DWORD PTR DS:[ECX+4],EAX ; Set current->BLINK == @free’d
An Overwritten Chunk In Freelist[0] Can Be Exploited To Write The Address
Of The Chunk Being Freed To An Arbitrary Location](https://image.slidesharecdn.com/heapsaboutheaps-brettmoore-221027142032-3e092f7b/75/Heaps-About-Heaps-Brett-Moore-ppt-24-2048.jpg)
![Exploiting FreeList[0] - Free
Exploitable Condition On Freelist[0] Insert
Chunk To Be Freed @003622D0
8400 Prev Size CK FL UN SI
Overwritten Chunk @00361E90
FFFF ???? ?? 02 ?? ??
FFFFFFFF 00360718
Place Where We Want To Write 003622D0
Could Be A Function Table, This Is A Lookaside
Chunk To Be Freed @003622D0
8400 Prev Size CK FL UN SI
00361E90 00360718 Overwritten Chunk @00361E90
FFFF ???? ?? 02 ?? ??
FFFFFFFF 003622D0
Overwritten Lookaside Now Populated
Three Requests And We Get Our Set Location
Chunk Is Inserted Before The
Overwritting Chunk.
FLINK and BLINK updated](https://image.slidesharecdn.com/heapsaboutheaps-brettmoore-221027142032-3e092f7b/75/Heaps-About-Heaps-Brett-Moore-ppt-25-2048.jpg)
![FreeList[0] - Allocate
Address FLINK BLINK
00361E90 003622D0 00360178
Freelist[0]
Address FLINK BLINK
00360178 00361E90 00362B60
Address FLINK BLINK
003622D0 00362B60 00361E90
Address FLINK BLINK
00362B60 00360178 003622D0
Populated
Freelist[0]
Load Freelist[0]->BLINK
Check Size Is Large
Enough For Request
Load Freelist[0]->FLINK
Check Size Is Large
Enough For Request
Too Small,
Load Chunk->FLINK
Check Size Is Large
Enough For Request
Large Enough,
Return Chunk
Exploitable Condition On Freelist[0] Allocate](https://image.slidesharecdn.com/heapsaboutheaps-brettmoore-221027142032-3e092f7b/75/Heaps-About-Heaps-Brett-Moore-ppt-26-2048.jpg)
![Exploiting FreeList[0] - Searching
Exploitable Condition On Freelist[0] Allocate - Searching
Overwritten Chunk @003622C8
0100 ???? ?? ?? ?? ??
00360188 ????????
Fake Chunk @00360180
8001 3600 80 01 36 00
00360188 00360188
Must Be Readable
Must Be Readable
= Requested Size
(+1 block)
Request Made For Size
0x0BF8
FLINK Points To Fake
Chunk
FLINK Points To Fake
Chunk+8
Chunk Returned To Caller
This Address Is In The
Freelists](https://image.slidesharecdn.com/heapsaboutheaps-brettmoore-221027142032-3e092f7b/75/Heaps-About-Heaps-Brett-Moore-ppt-27-2048.jpg)
![Exploiting FreeList[0] - Relinking
Exploitable Condition On Freelist[0] Allocate - Relinking
Overwritten Chunk @003622C8
0202 ???? ?? ?? ?? ??
0036057C READ
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXXX.....
Request Made For Size
Smaller Than Our Overwrite
Fake Chunk @00360574
7005 3600 08 06 36 00
???????? 00360688
Must Be Read/Write
> Relink Chunk Size
FLINK Points To Fake
Chunk
FLINK Points To Fake
Chunk+8
Relink Chunk Address
Written To 00360580
This Is The FrontEndHeap
(Lookaside Base)](https://image.slidesharecdn.com/heapsaboutheaps-brettmoore-221027142032-3e092f7b/75/Heaps-About-Heaps-Brett-Moore-ppt-29-2048.jpg)
![When Allocated Chunk Is To Large
: Checked when allocation from other list
: Chunk is cut to size, New header is written
: Chunk is inserted to freelist[n] or freelist[0]
: Size manipulated to put new chunk into arbitrary Freelist
Splitting / Resizing
7C82A3DB CMP EBX,1 ; Larger than one block difference
7C82A3DE JE ntdll.7C82E5A4
7C82A3E4 MOV EAX,DWORD PTR SS:[EBP-48] ; Load requested size
7C82A3E7 LEA EDI,DWORD PTR DS:[ESI+EAX*8] ; Move to create the new chunk
..
7C82A3F3 MOV BYTE PTR DS:[EDI+5],CL ; Store new flag
7C82A3F6 MOV WORD PTR DS:[EDI+2],AX ; Store Prev Size
..
7C82A400 MOV WORD PTR DS:[EDI],BX ; Store new size
7C82A403 TEST CL,10 ; Is chunk new LAST CHUNK
7C82A406 JNZ ntdll.7C82A65E ; Jump if chunk is last chunk
7C82A40C LEA EAX,DWORD PTR DS:[EDI+EBX*8] ; Move to NEXT chunk based on size
7C82A40F MOV DWORD PTR SS:[EBP-50],EAX ; Will try and coalesce with next
Can Skip By
Setting As Last
Chunk](https://image.slidesharecdn.com/heapsaboutheaps-brettmoore-221027142032-3e092f7b/75/Heaps-About-Heaps-Brett-Moore-ppt-30-2048.jpg)
![When Chunk Is Free’d To Freelist
: Size field is used to locate previous and next chunk
: Requires valid FLINK/BLINK on chunks to colaesce
: An overflow can control all of this to prevent coalesce
Coalesced Chunks
7C82A6F6 JE SHORT ntdll.7C82A702 ; If prev size is 0 jump
7C82A6F8 TEST BYTE PTR DS:[ESI+5],1 ; Is prev chunk BUSY?
7C82A6FC JE ntdll.7C82CA7A ; If not then coalesce
7C82A702 TEST BYTE PTR DS:[EDI+5],10 ; Is our chunk the last chunk?
7C82A706 JNZ ntdll.7C82A7B3 ; If so can't coalesce
7C82A70C MOV EAX,DWORD PTR SS:[EBP+10]
7C82A70F MOV EAX,DWORD PTR DS:[EAX] ; Load our block size
7C82A711 LEA ESI,DWORD PTR DS:[EDI+EAX*8] ; Move to next chunk
7C82A714 TEST BYTE PTR DS:[ESI+5],1 ; Is next chunk BUSY?
7C82A718 JNZ ntdll.7C82A7B3 ; Yup, so don't colaesce
Test Flag Of
Previous
Chunk
Test Flag
Of Next
Chunk
Header Self Size Prev Size CK FL UN SI](https://image.slidesharecdn.com/heapsaboutheaps-brettmoore-221027142032-3e092f7b/75/Heaps-About-Heaps-Brett-Moore-ppt-31-2048.jpg)

![How To Prevent A Free
: Set the chunks flag to FAIL the BUSY check
Why Prevent A Free()
: Remove chunk from Lookaside
Can be overwritten before allocation
: Remove chunk from Freelist[]
Flag gets reset on allocation
Bypass Cookie Check
: Will cause a heap exception, doesn’t stop execution
Preventing A Free
Move To Chunk
Header
Load Flag and
Test If Busy](https://image.slidesharecdn.com/heapsaboutheaps-brettmoore-221027142032-3e092f7b/75/Heaps-About-Heaps-Brett-Moore-ppt-36-2048.jpg)
![What Is Heap/Stack Flipping
: Exploit data is on the heap
: For fine grained control, it needs to be on the stack
Requirements
: Pointer to exploit data; on stack, in a register, in [reg +/- n]
: Locate instructions to manipulate pointer and pop esp, ret
: Overwrite function pointer to return to instructions
Populate ESP With The Pointer To Exploit Data
Heap / Stack Flipping
PUSH EBX
POP ESP
POP EBP
RET
EBX -> DATA
LEAVE
RET
EBP -> DATA ECX -> DATA
MOV ESP,ECX
RET 8
EAX-> DATA
XCHG EAX,ESP
RET](https://image.slidesharecdn.com/heapsaboutheaps-brettmoore-221027142032-3e092f7b/75/Heaps-About-Heaps-Brett-Moore-ppt-40-2048.jpg)
![Bypassing DEP
Perfect
Instruction Set
NtSetInformationProcess(
NtCurrentProcess(), // (HANDLE)-1
ProcessExecuteFlags, // 0x22
&ExecuteFlags, // ptr to 0x2
sizeof(ExecuteFlags)); // 0x4
Requires [ESI+37] To Be Writable
Correctly Set Stack
BUT!](https://image.slidesharecdn.com/heapsaboutheaps-brettmoore-221027142032-3e092f7b/75/Heaps-About-Heaps-Brett-Moore-ppt-46-2048.jpg)

![The Lookaside Lists
Lookaside[8] Has A Top Chunk That Sits
After Lookaside[7] Top Chunk On All Runs
AND
The Difference Is Greater Than 0x3C
0x0a871cc8 – 0x0a871c60
= 0x68
0x0a871c38 – 0x0a871bd0
= 0x68
0x0a871d00 – 0x0a871c98
= 0x68](https://image.slidesharecdn.com/heapsaboutheaps-brettmoore-221027142032-3e092f7b/75/Heaps-About-Heaps-Brett-Moore-ppt-60-2048.jpg)
![First Request
: Request Lookaside[7]
: Overwrite Lookaside[8]
: Free Request
Problem
: If we now had two allocations of Lookaside[8]
: But we only have one
Solution
: Set flag of top chunk of Lookaside[8] to be FREE
: Then when free() is called it will be skipped
Lets Try It](https://image.slidesharecdn.com/heapsaboutheaps-brettmoore-221027142032-3e092f7b/75/Heaps-About-Heaps-Brett-Moore-ppt-61-2048.jpg)
![First Request
: Request Lookaside[7]
: Overwrite Lookaside[8]
: Free Request
Second Request
: Request Lookaside[8]
: Top Chunk Is Popped
: Free Request
Third Request
: Request Lookaside[8], Our Address Is Returned
Lets Try It](https://image.slidesharecdn.com/heapsaboutheaps-brettmoore-221027142032-3e092f7b/75/Heaps-About-Heaps-Brett-Moore-ppt-62-2048.jpg)