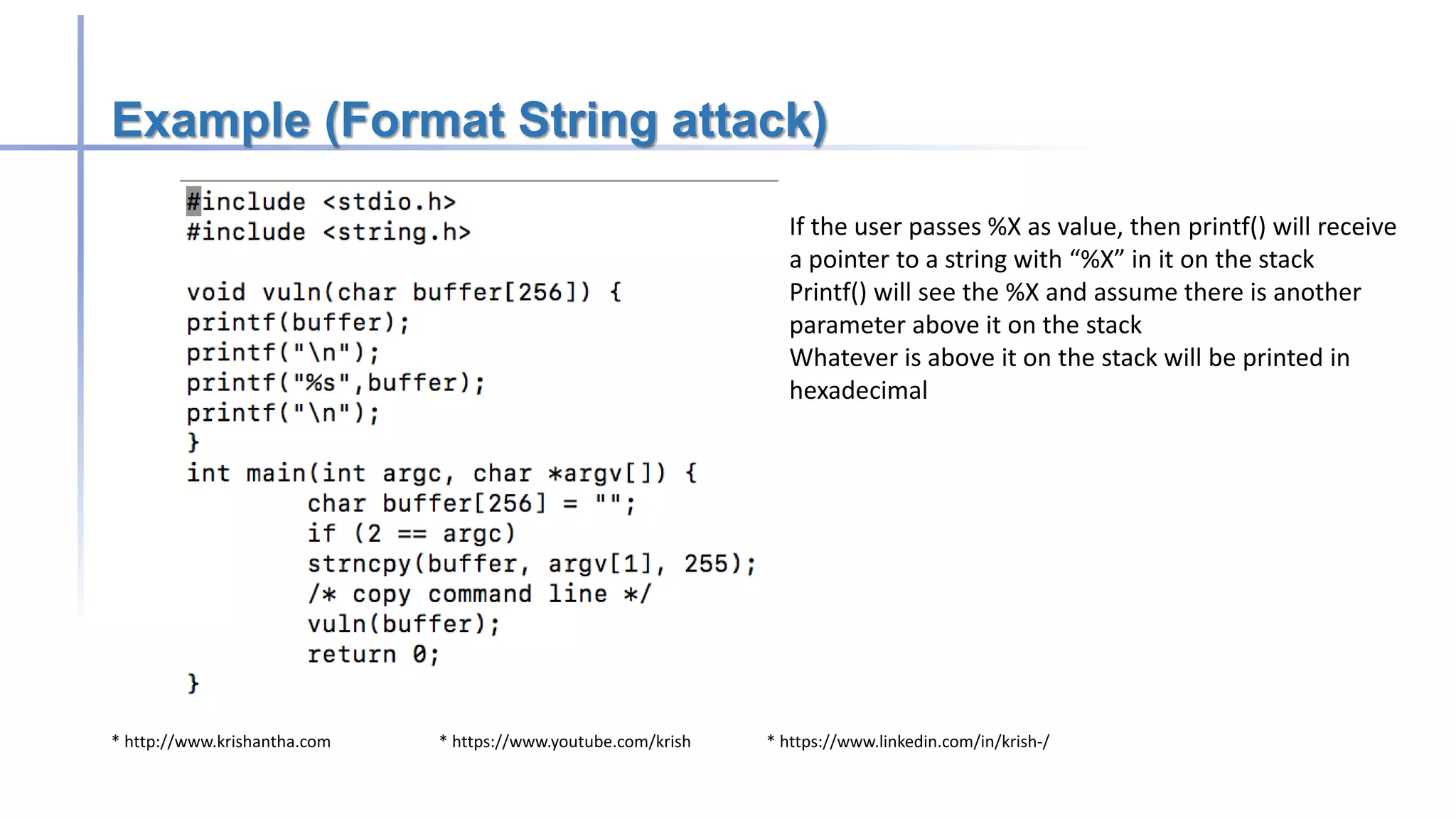
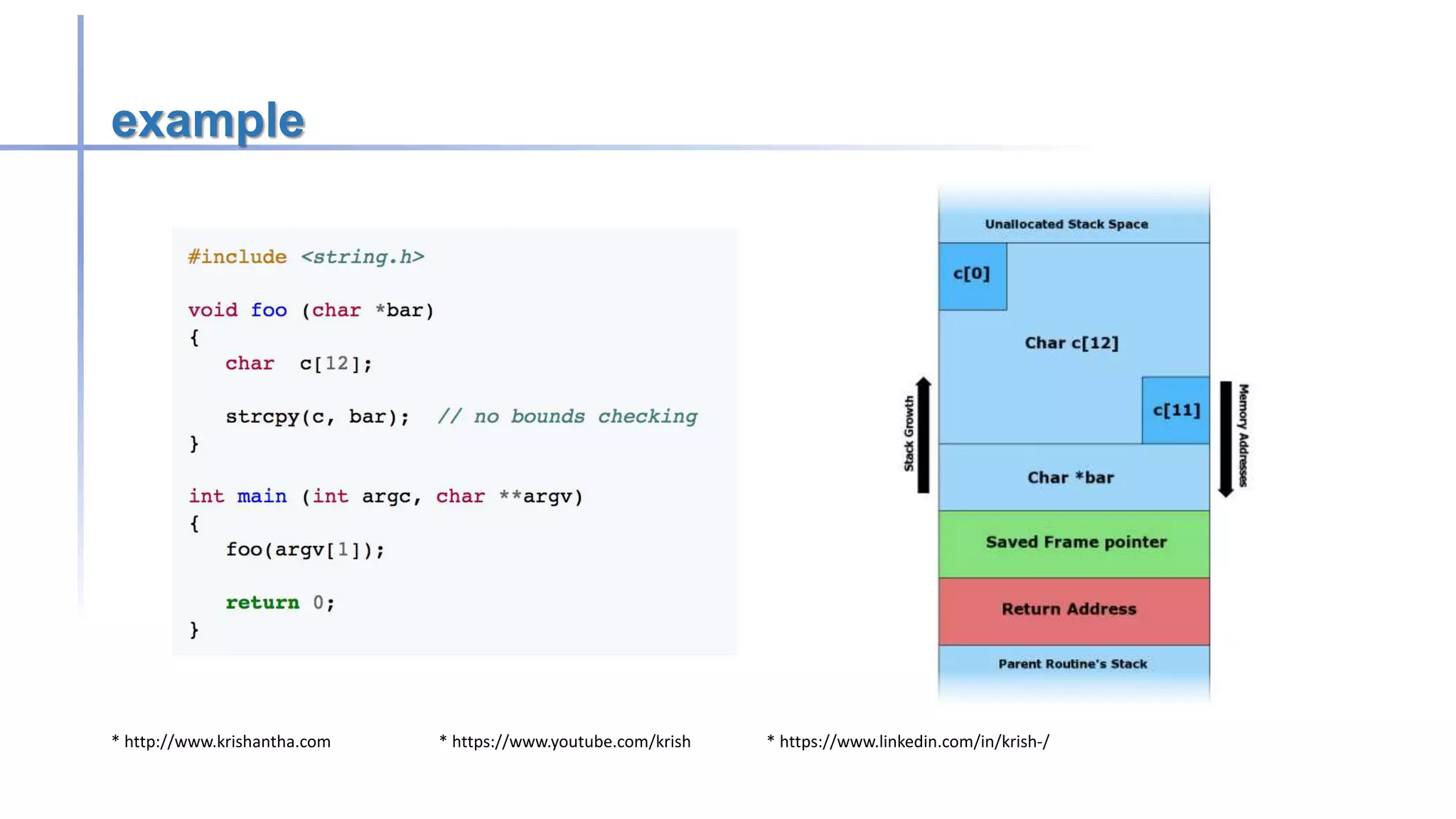
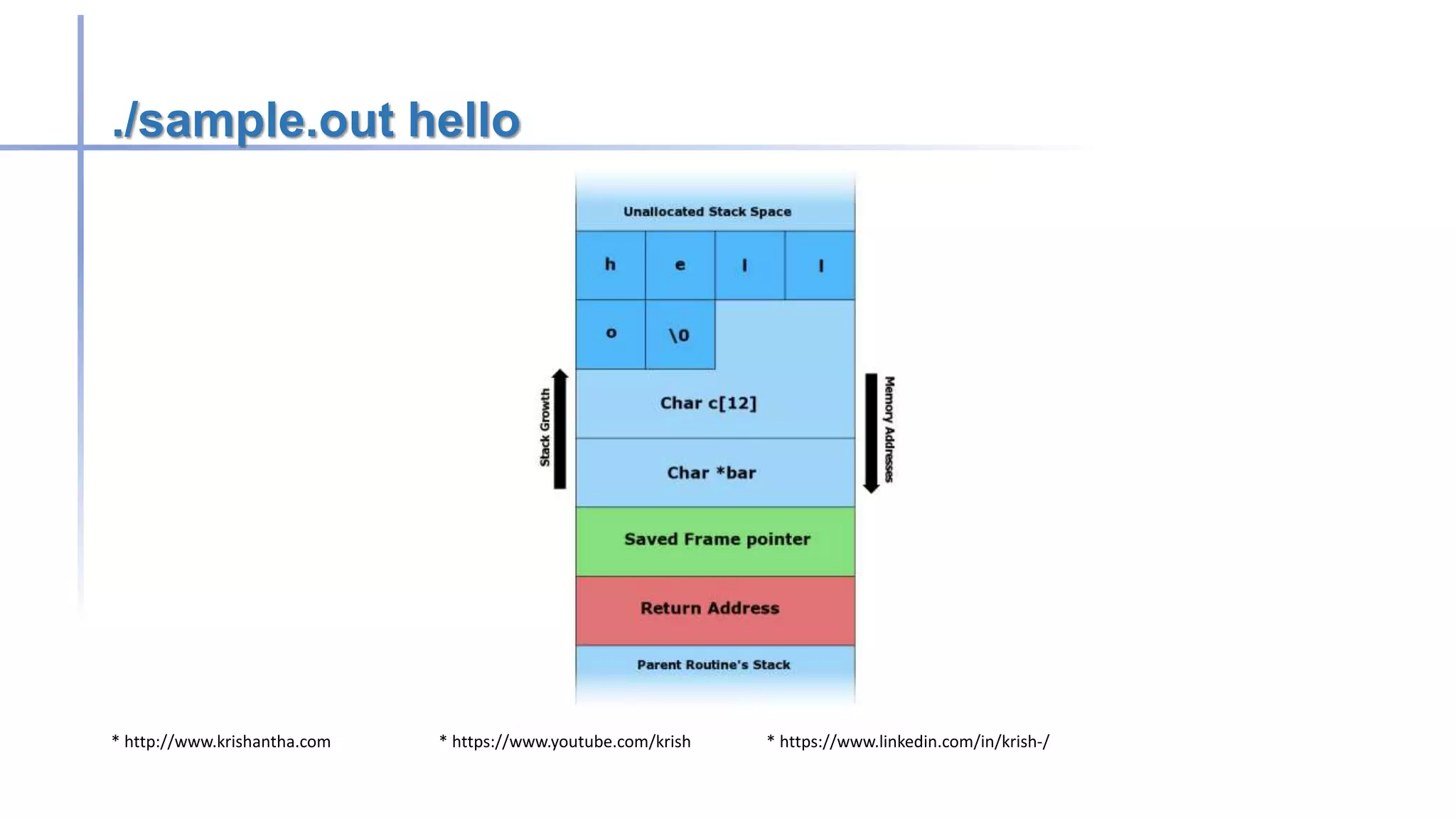
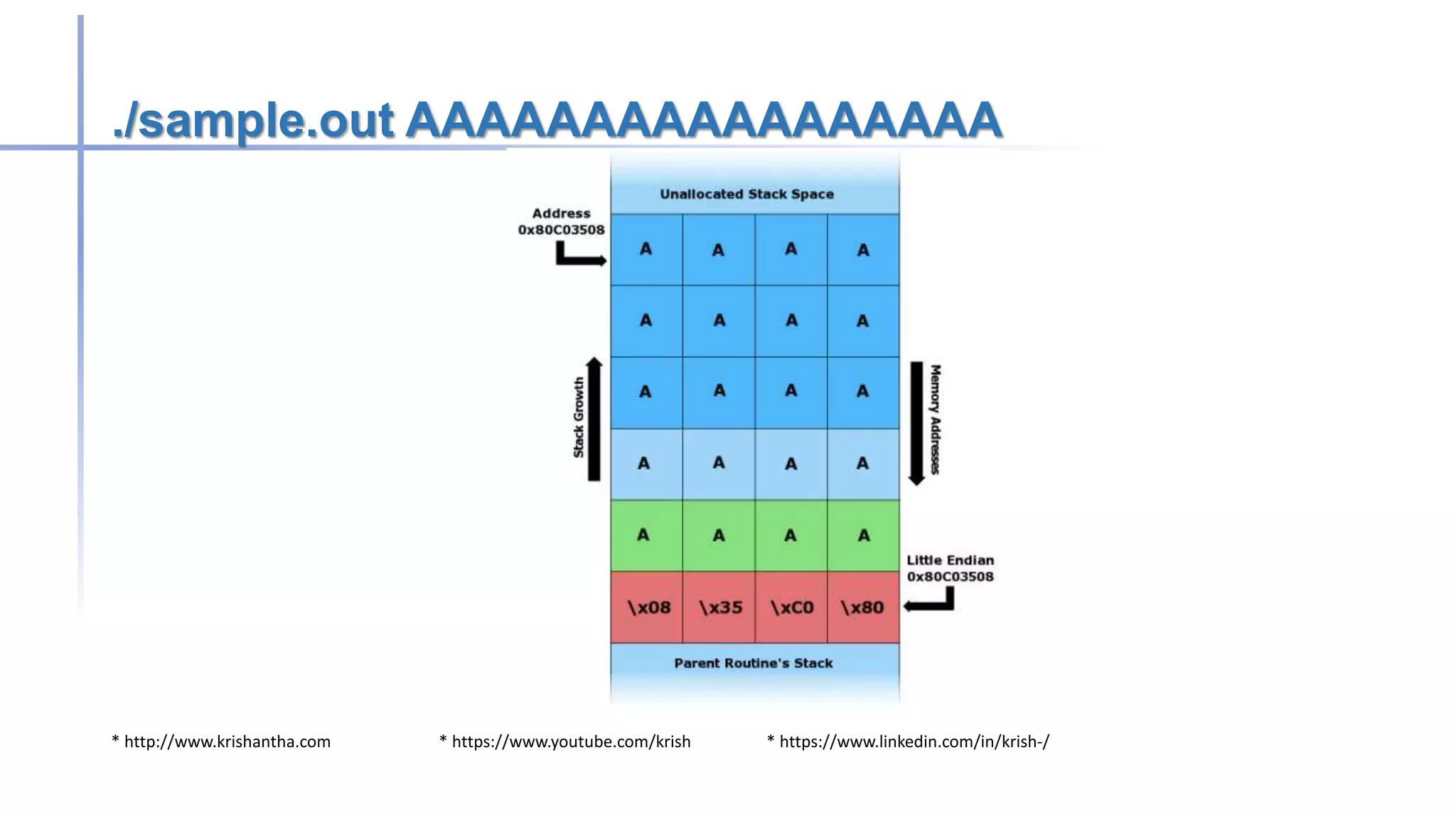
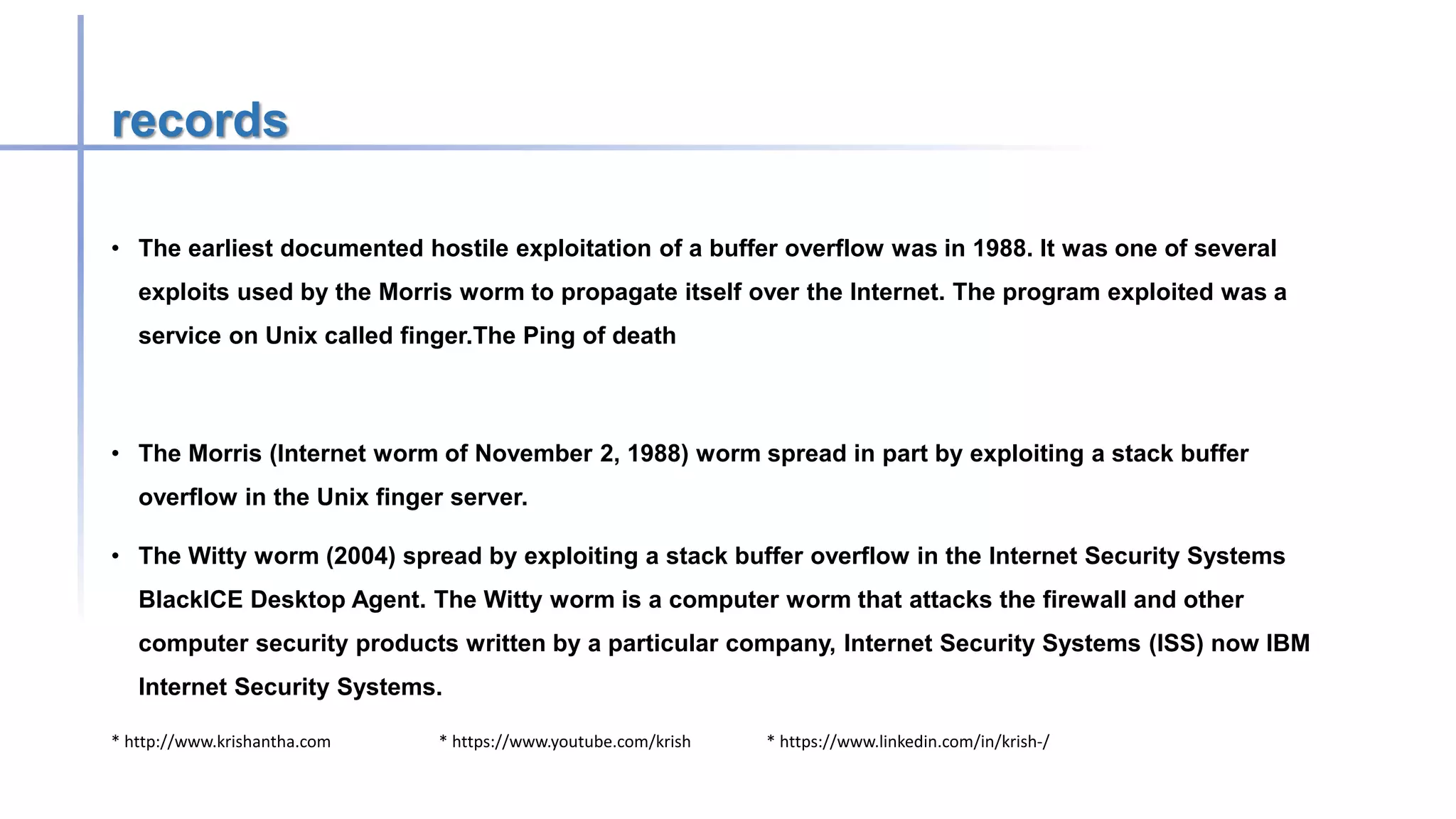
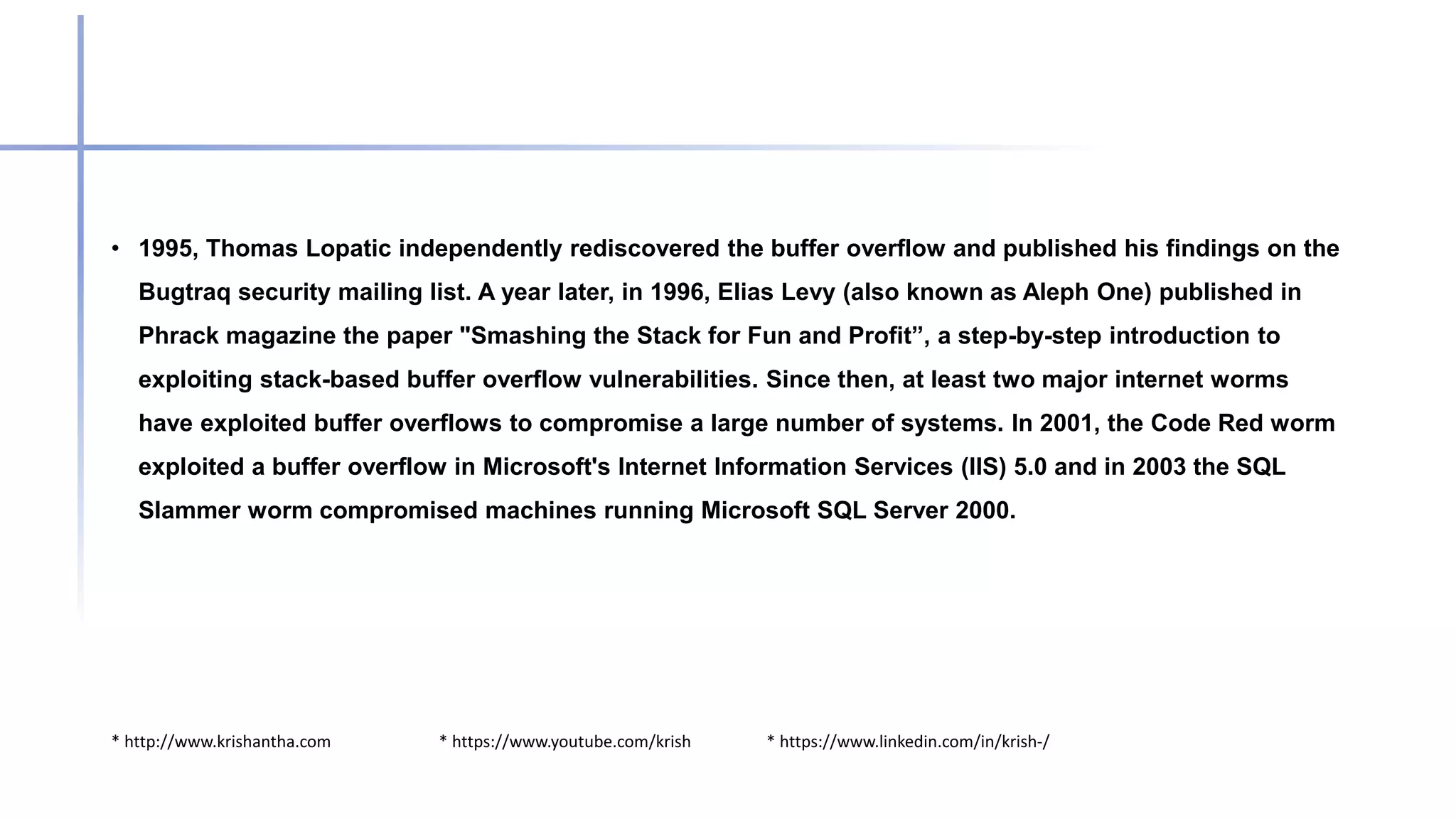
Buffer overflow attacks occur when a program writes more data to a buffer than it can hold, potentially leading to erratic behavior or crashes. These vulnerabilities primarily affect applications written in C/C++, and methods to prevent them include avoiding unsafe functions, inserting bounds checking, and using safer programming languages. Historically, notable worms like the Morris and Code Red exploited buffer overflow vulnerabilities to compromise systems.