The document covers heap-based exploitation techniques and the structure of heaps in memory management, primarily focusing on the dlmalloc algorithm used in Linux. It outlines several exercises from a training environment called Protostar, which include challenges like basic heap overflow, code flow hijacking, and issues related to stale pointers. Each challenge provides insights into how heap vulnerabilities can be exploited to manipulate memory and execute arbitrary code.




















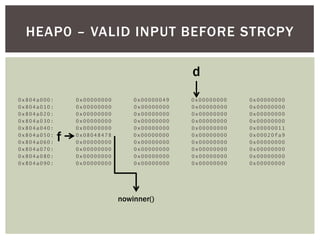
![ Relevant Code:
struct data *d;
struct fp *f;
d = malloc(sizeof(struct data));
f = malloc(sizeof(struct fp));
f->fp = nowinner;
printf("data is at %p, fp is at %pn", d, f);
strcpy(d->name, argv[1]);
f->fp();
HEAP0 - CODE](https://image.slidesharecdn.com/heapbasedexploitation-180820045054/85/Heap-Base-Exploitation-23-320.jpg)





![ Relevant Code
struct internet *i1, *i2, *i3;
i1 = malloc(sizeof(struct internet));
i1->priority = 1;
i1->name = malloc(8);
i2 = malloc(sizeof(struct internet));
i2->priority = 2;
i2->name = malloc(8);
strcpy(i1->name, argv[1]);
strcpy(i2->name, argv[2]);
HEAP1 –CODE](https://image.slidesharecdn.com/heapbasedexploitation-180820045054/85/Heap-Base-Exploitation-30-320.jpg)
![ This instruction is the important one:
strcpy(i2->name, argv[2]);
We are moving an argument into a pointer stored at i2->name
Can we change the destination of our argument?
HEAP1 – EXPLOIT IDEAS](https://image.slidesharecdn.com/heapbasedexploitation-180820045054/85/Heap-Base-Exploitation-31-320.jpg)