1. The document outlines an agenda for a workshop on advanced ARM exploitation. The agenda includes introductions to memory corruption, buffer overflows, format string exploitation, and techniques for bypassing exploit mitigations like DEP using return-oriented programming (ROP).
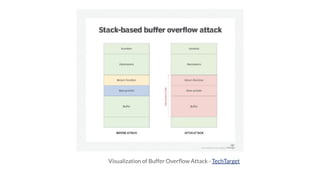
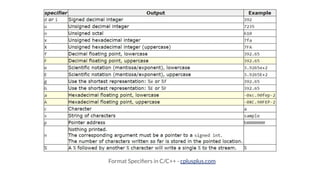
2. Practical demonstrations are provided on topics like visualizing stack corruption from buffer overflows, overwriting the instruction pointer to hijack execution, injecting and executing shellcode payloads, reading and writing arbitrary memory with format strings, and creating ROP chains to bypass DEP.
3. The speakers are introduced as security researchers and instructors specializing in areas like exploit development, malware, rootkits, and reverse engineering. Attendees are encouraged to contact