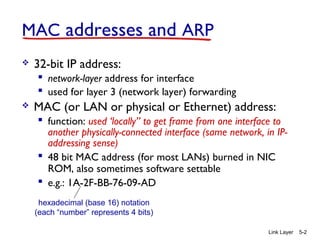
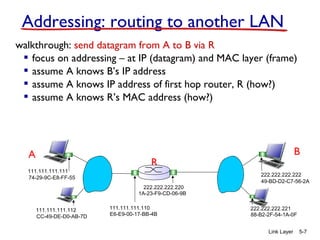
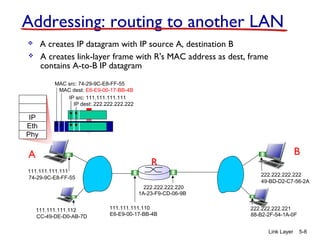
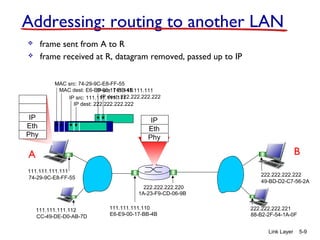
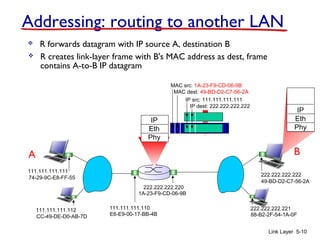
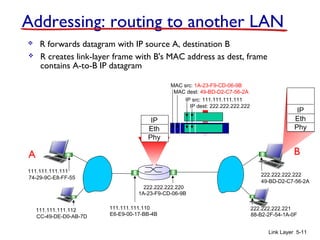
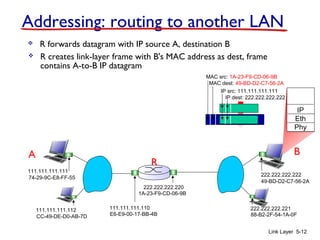
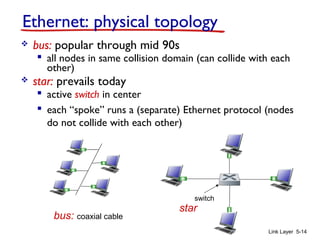
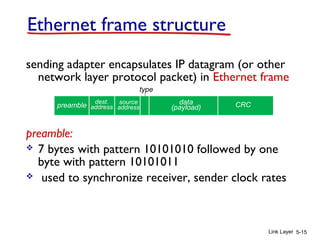
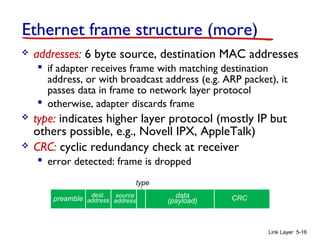
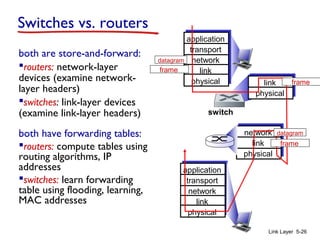
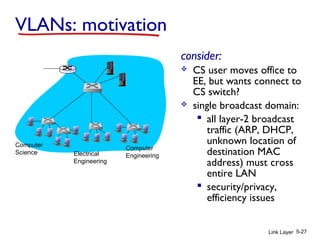
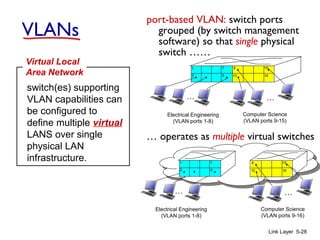
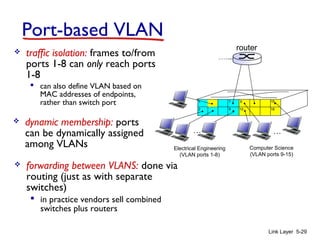
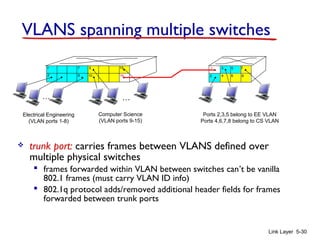
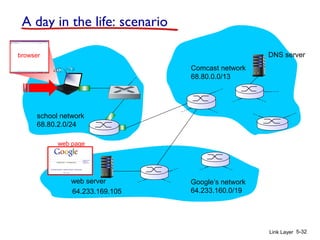
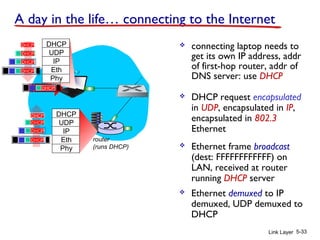
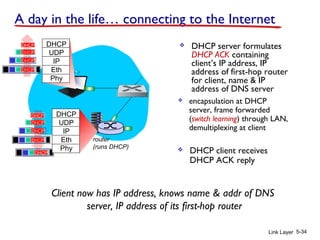
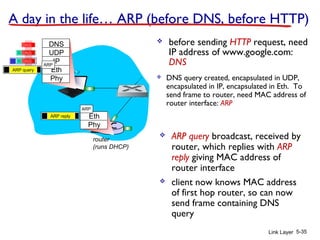
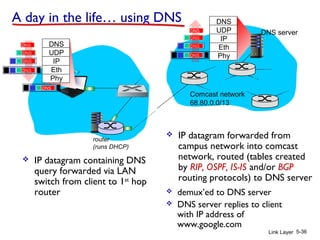
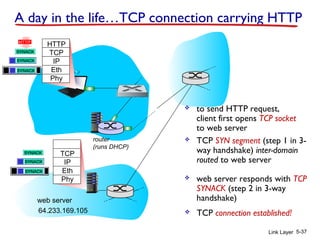
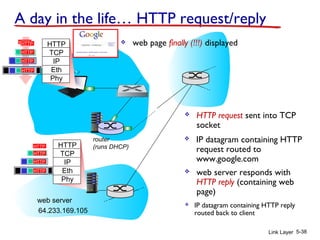
1. The document discusses the link layer in computer networks, including MAC addresses, ARP, Ethernet frames, and switches. MAC addresses are used locally to deliver frames between connected interfaces, while IP addresses are used for network layer forwarding.
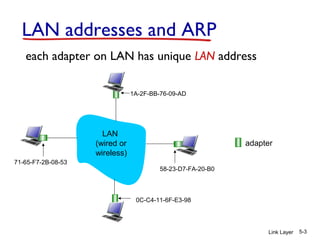
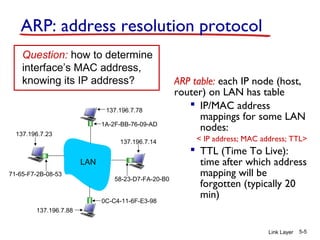
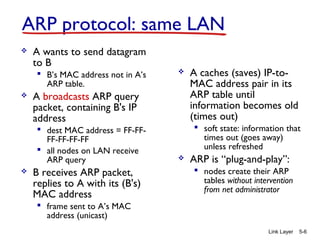
2. ARP is used to map IP addresses to MAC addresses on the same local area network (LAN). Each node maintains an ARP cache that maps IP addresses to MAC addresses of other nodes on the LAN.
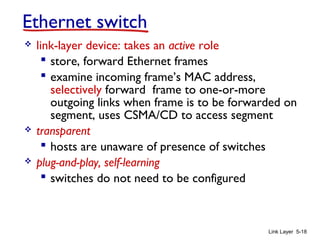
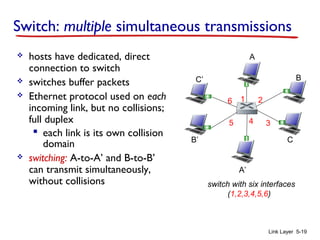
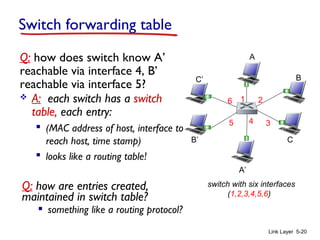
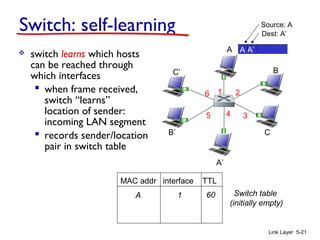
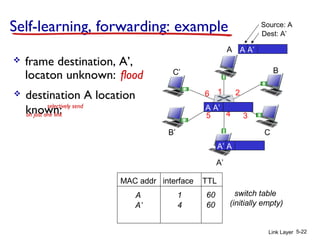
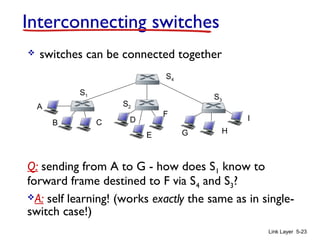
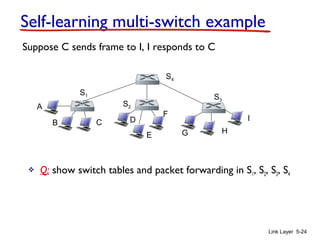
3. Switches learn the location of nodes by examining the source MAC addresses of received frames. They build forwarding tables that map MAC addresses to switch ports. This allows frames to be selectively forwarded to the correct destination port, improving scalability over hubs.