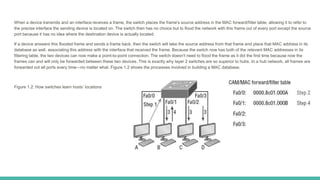
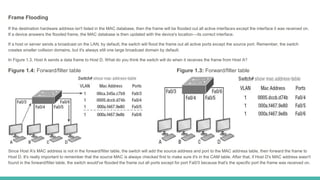
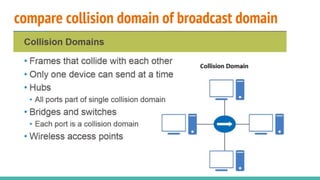
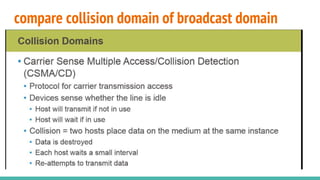
The document covers layer 2 switching concepts, detailing how switches utilize MAC address tables for efficient data forwarding, minimizing collisions by creating separate collision domains for each port. It emphasizes the superiority of switches over hubs, explaining frame filtering and flooding processes, and the structure of Ethernet frames used in data transmission. Additionally, it outlines the concept of collision detection in Ethernet networks via the CSMA/CD method.