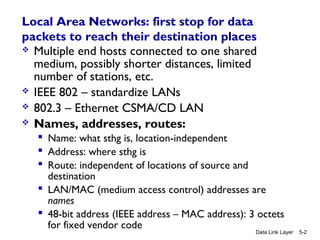
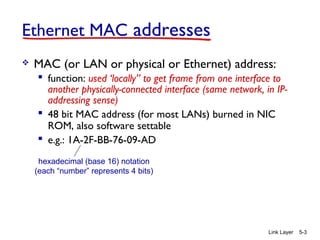
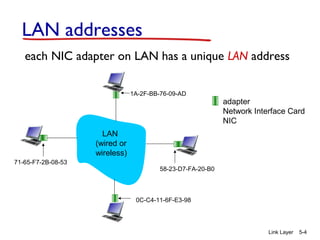
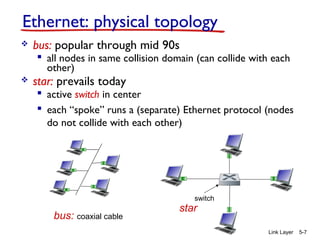
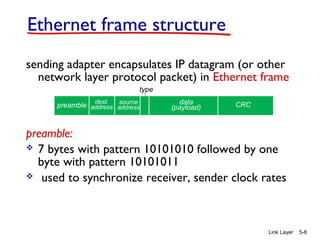
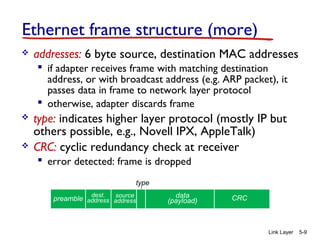
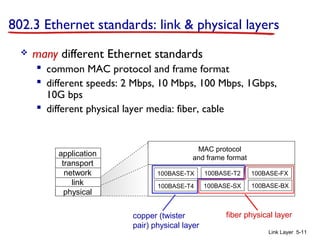
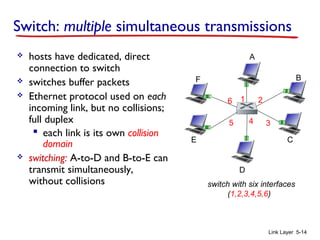
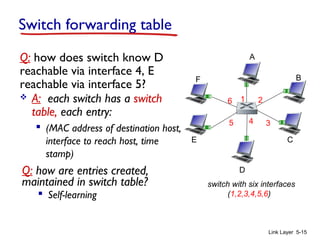
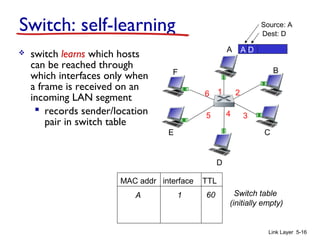
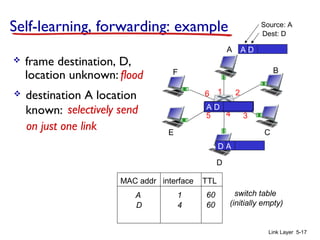
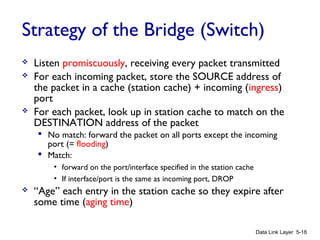
Chapter 5 of 'Computer Networking: A Top-Down Approach' discusses the link layer and local area networks (LANs), focusing on Ethernet technology and MAC addresses. It covers the structure of Ethernet frames, the function of network interface cards (NICs), and the operation of switches, including their self-learning mechanisms. The chapter emphasizes the importance of MAC address allocation, Ethernet's connectionless and unreliable characteristics, and various Ethernet standards.