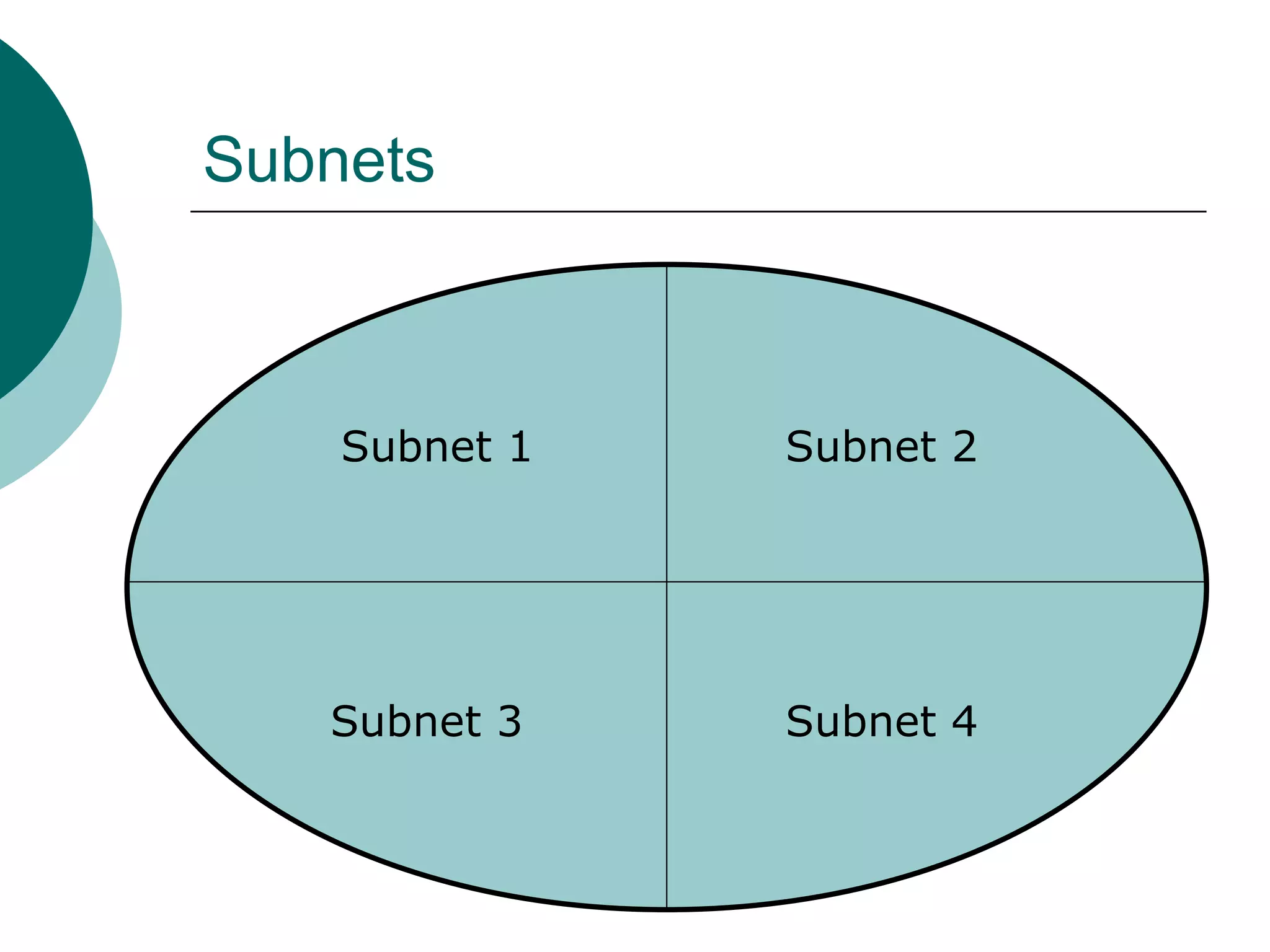
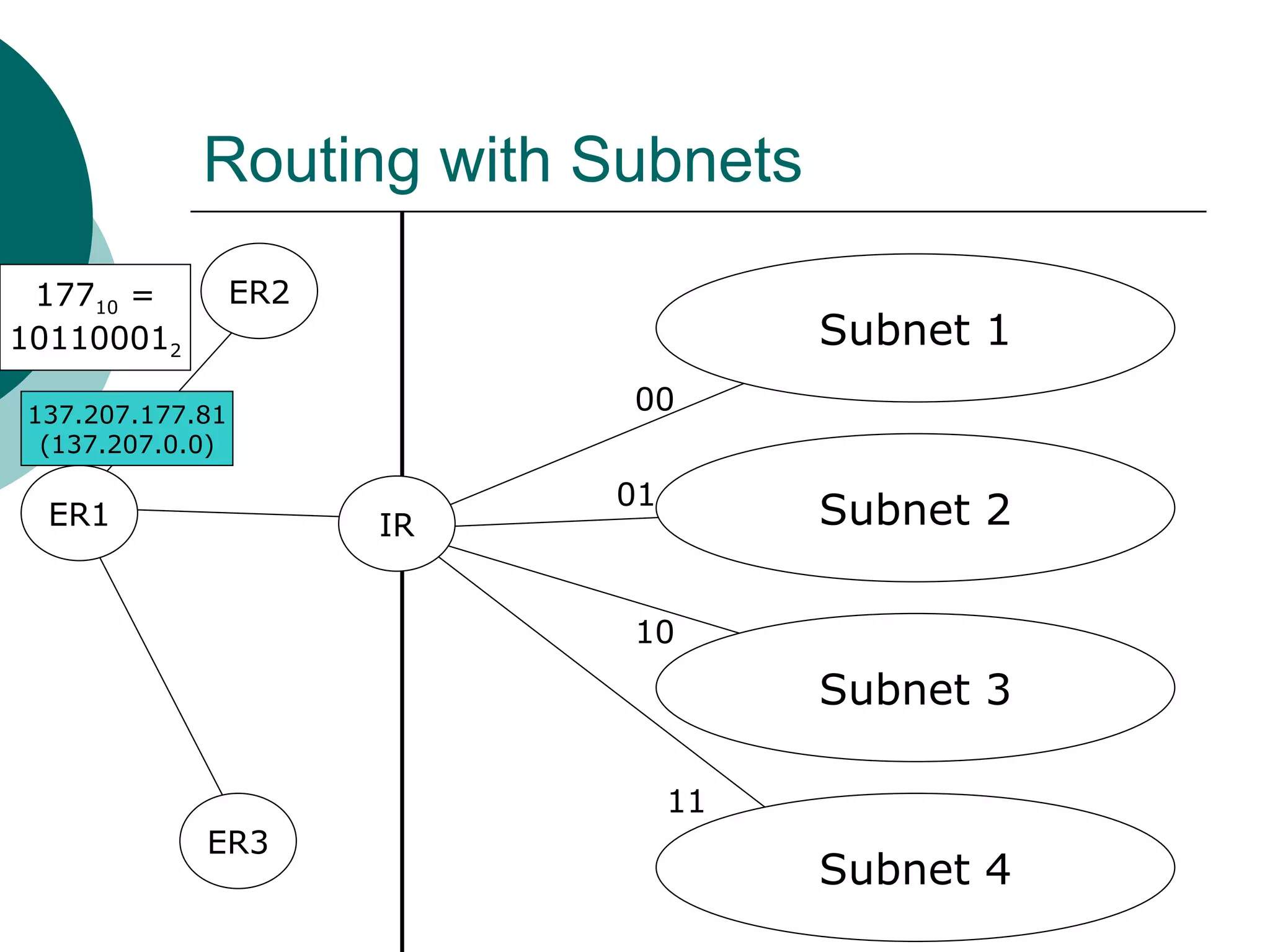
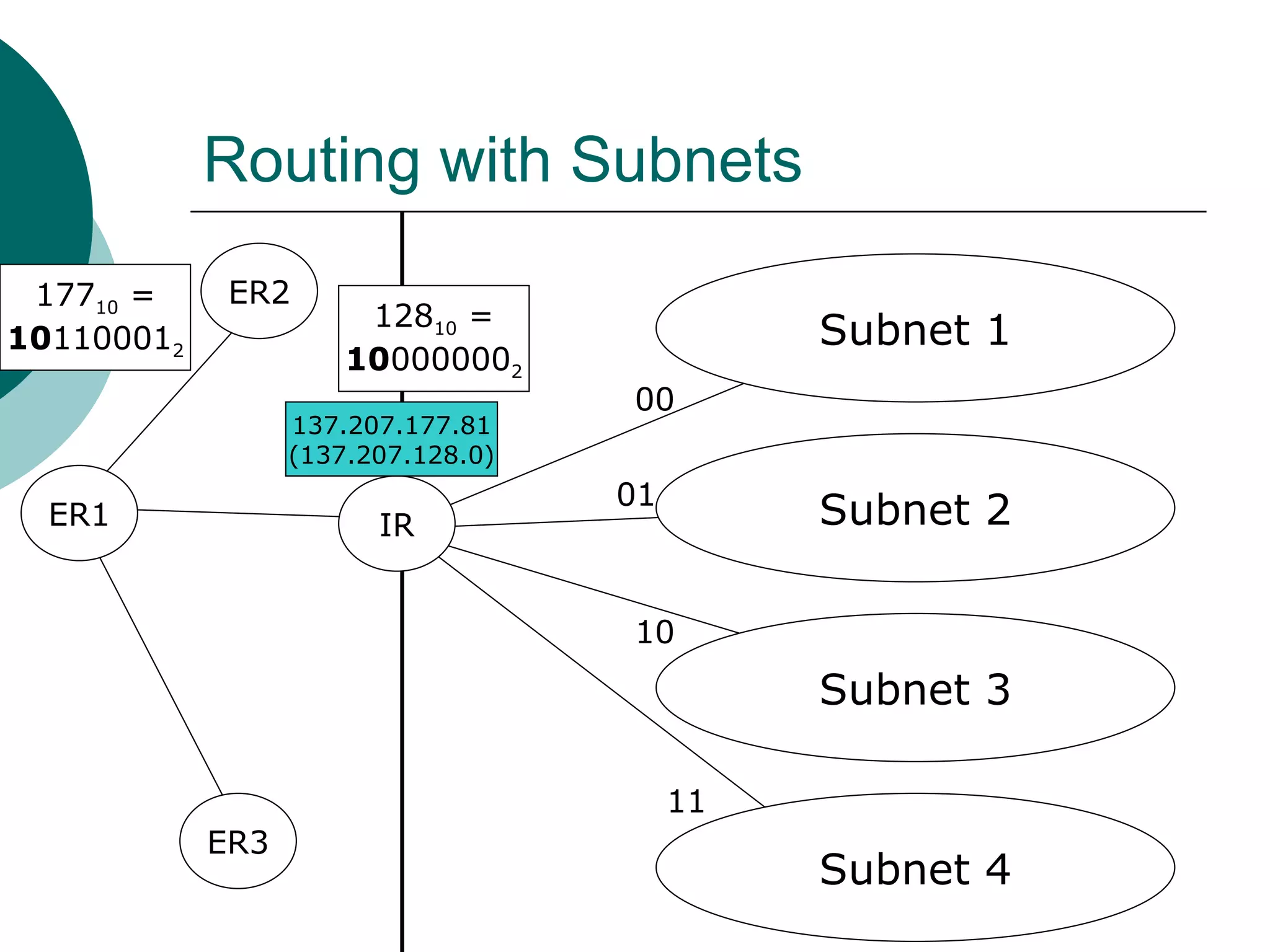
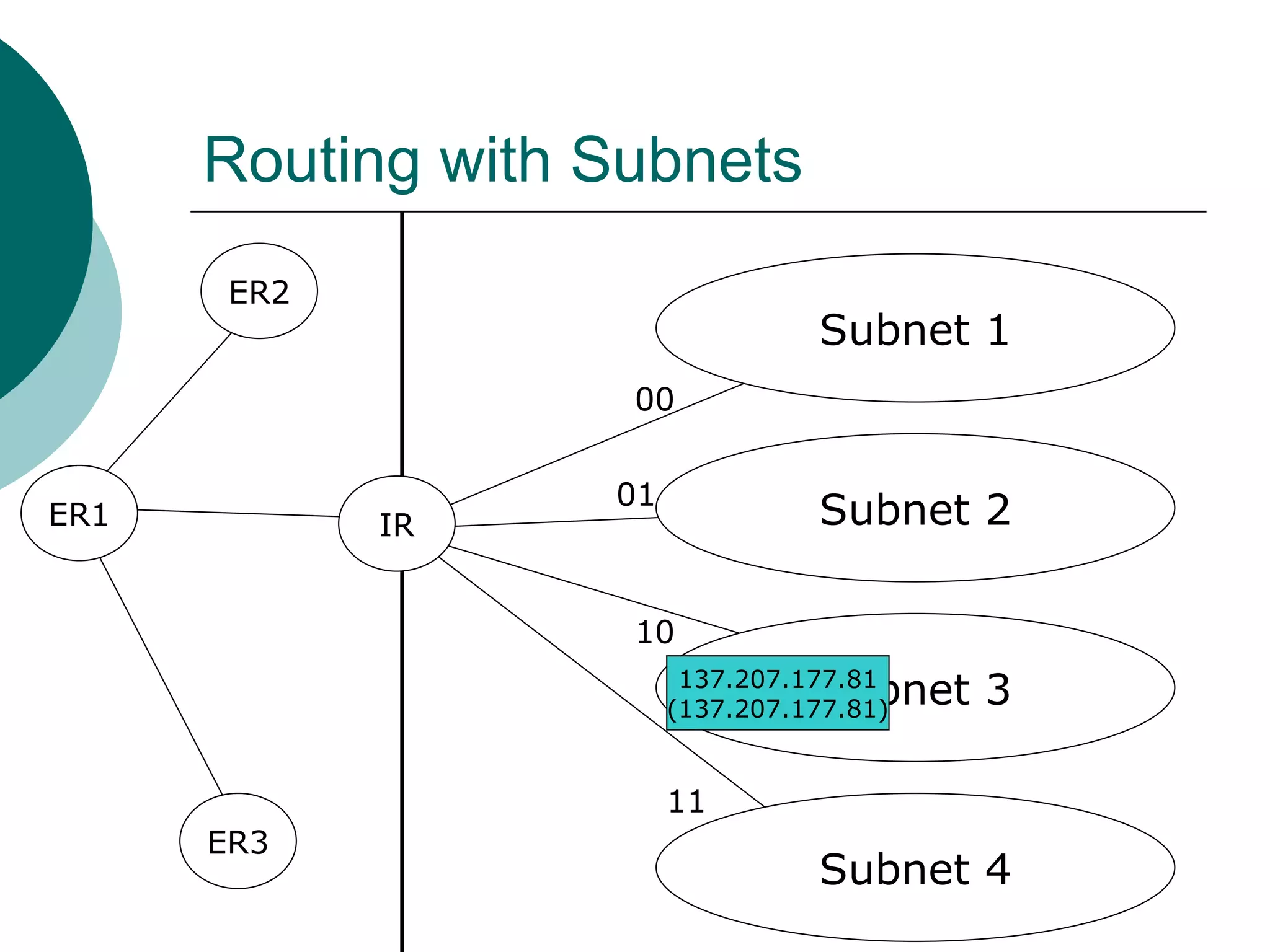
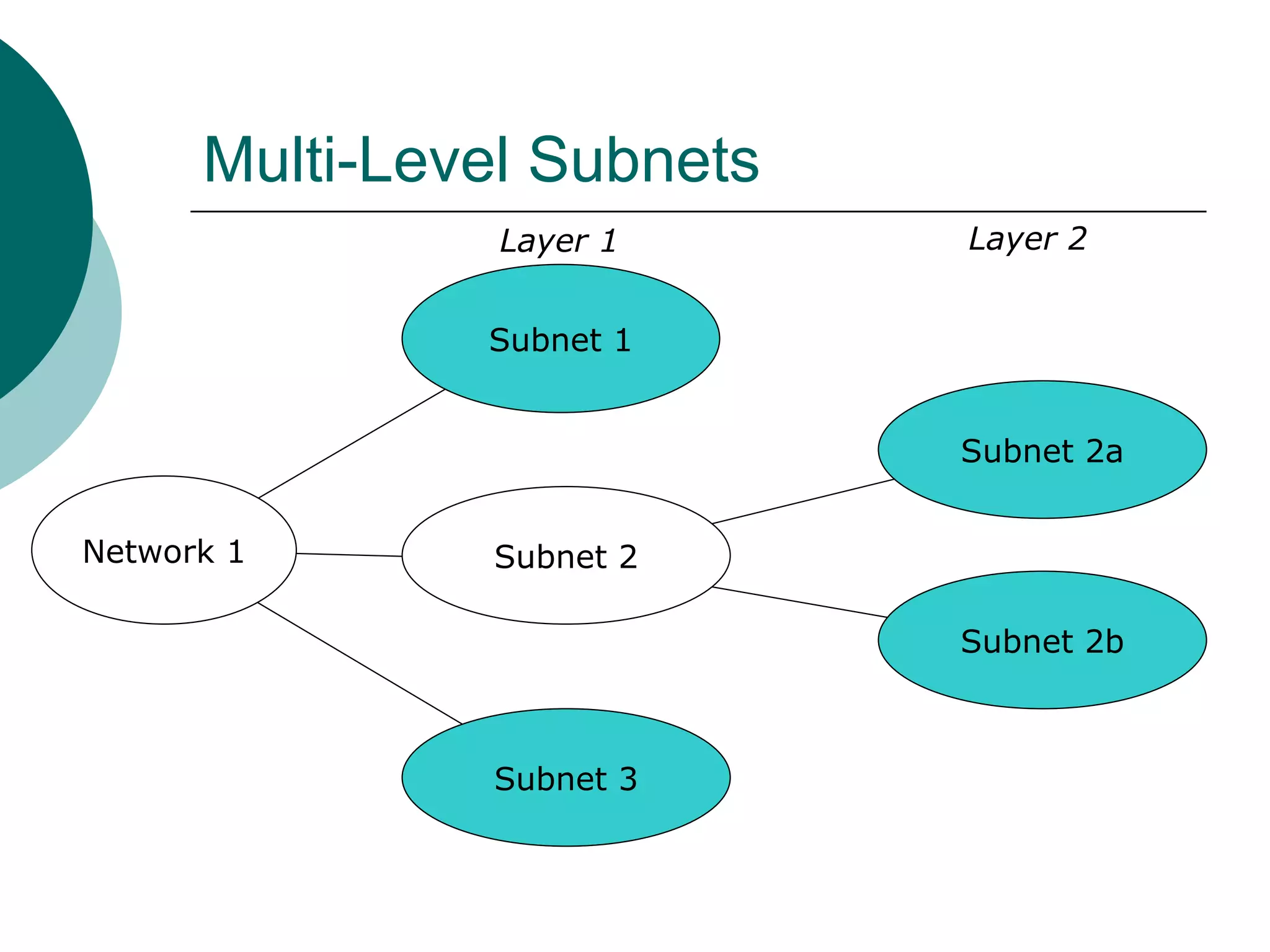
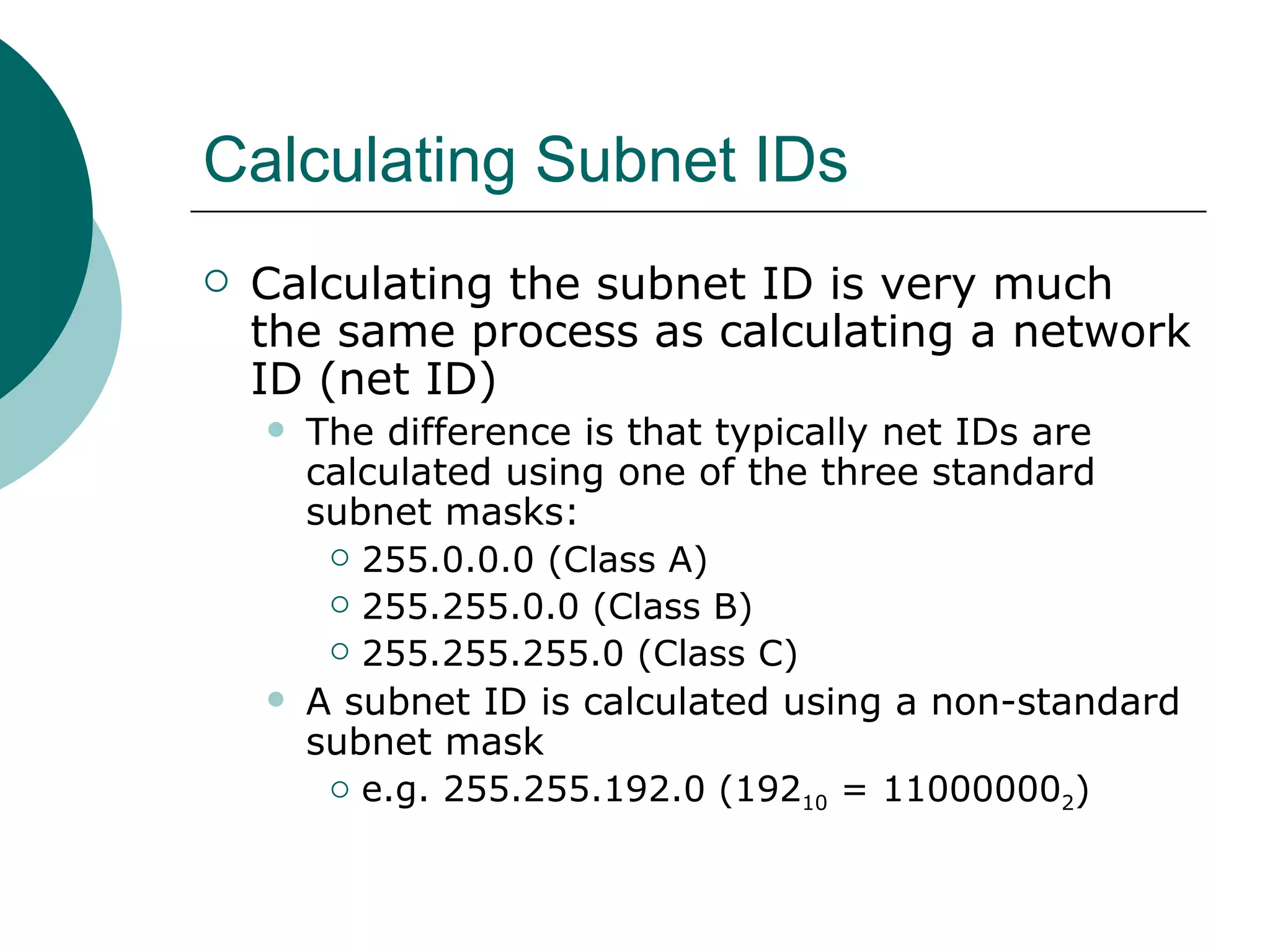
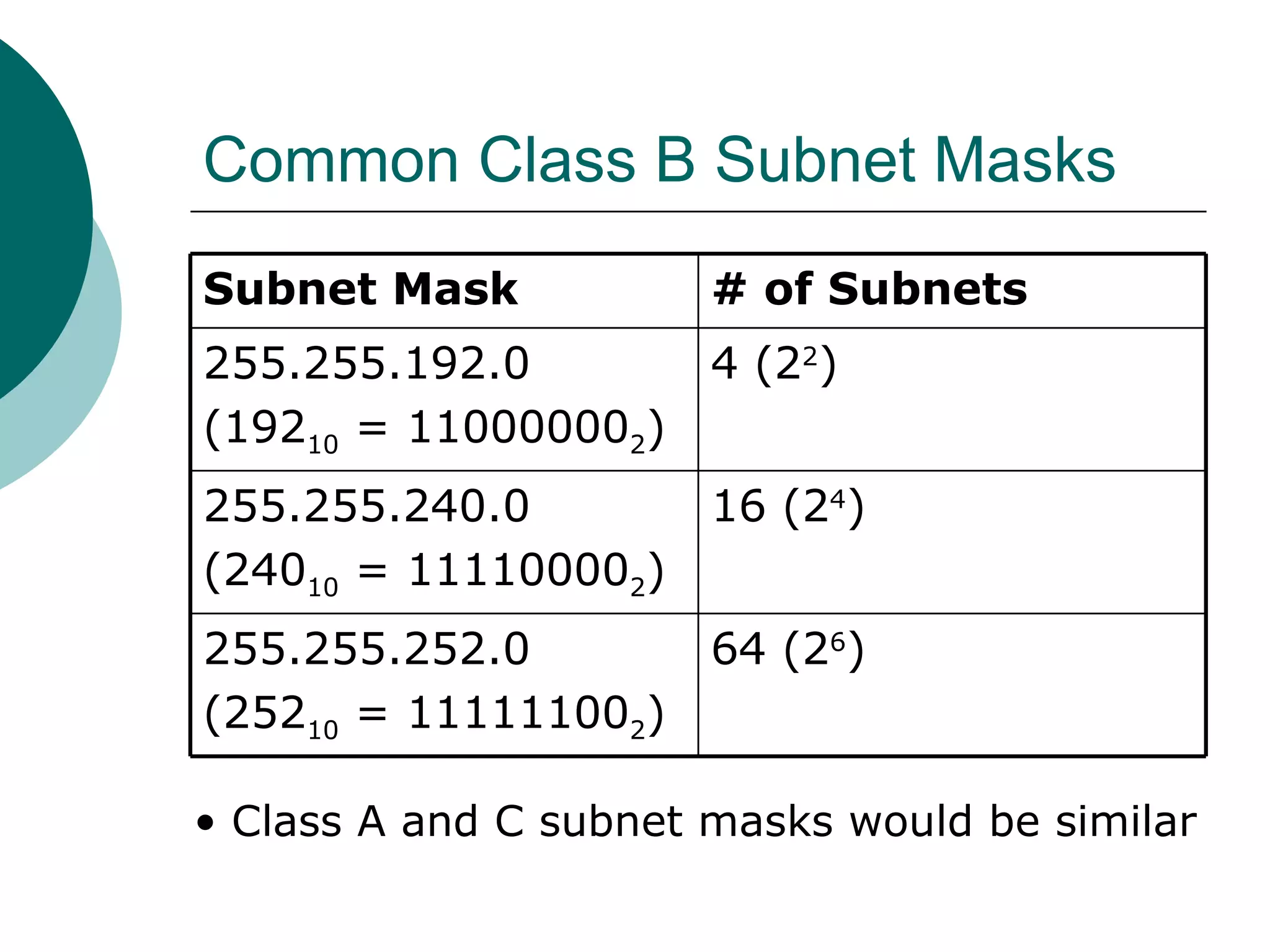
Subnets divide a network into smaller sub-networks or subnets. Each subnet is treated as a separate network and can be further divided. When a packet enters a network with subnets, routers will route based on the subnet ID which is a combination of the network ID and subnet portion of the IP address. Subnets are only relevant for routing within an organization and are transparent outside the organization.