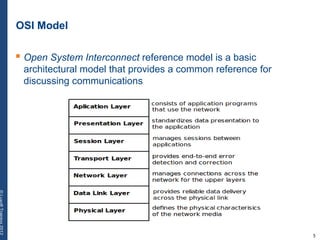
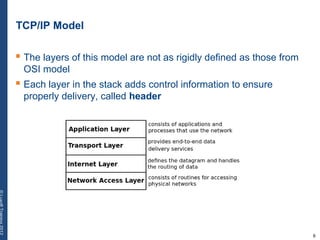
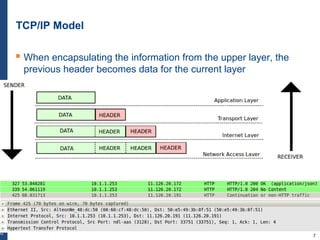
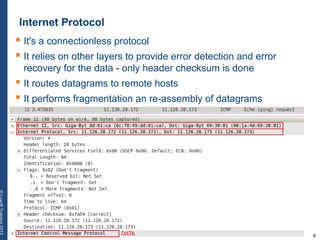
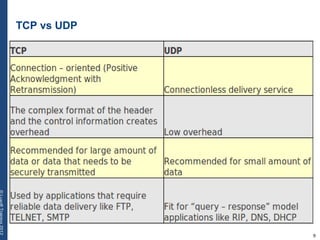
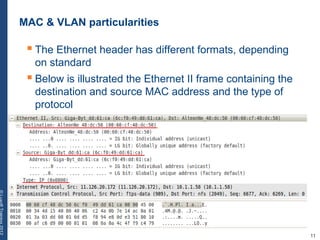
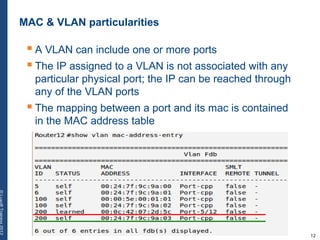
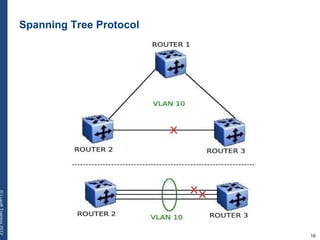
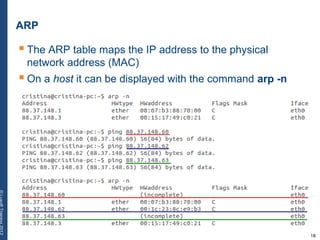
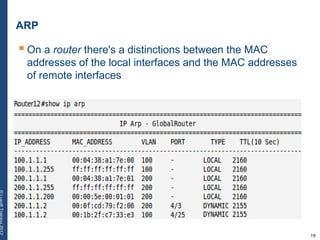
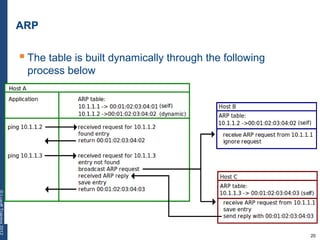
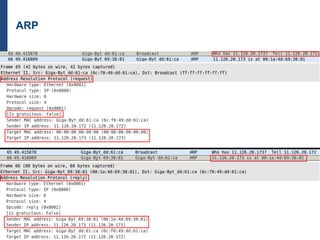
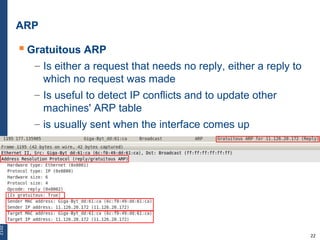
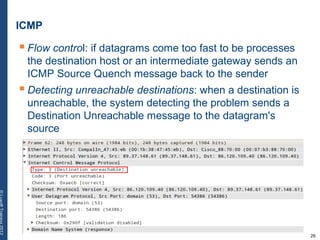
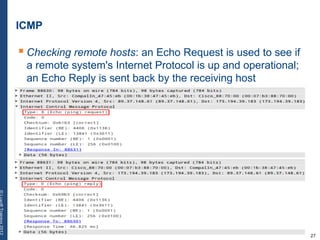
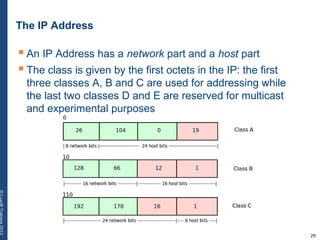
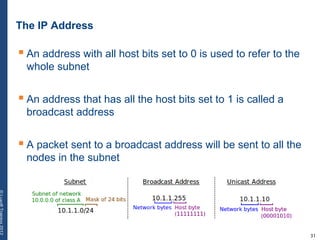
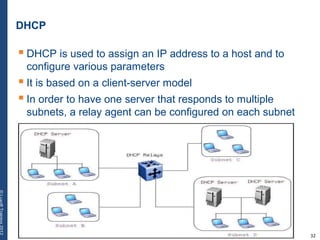
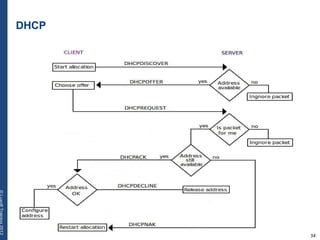
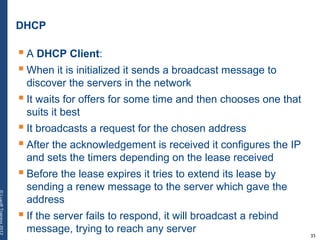
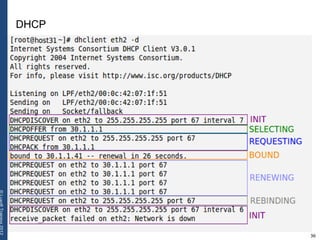
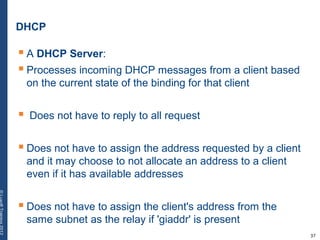
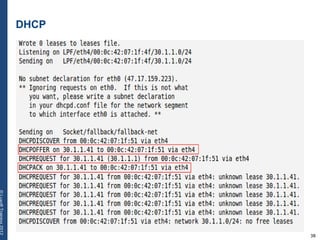
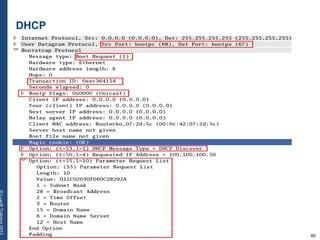
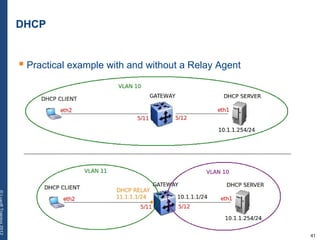
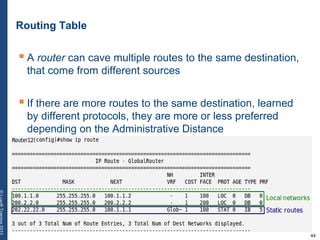
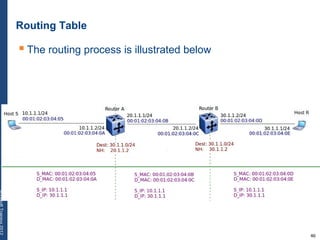
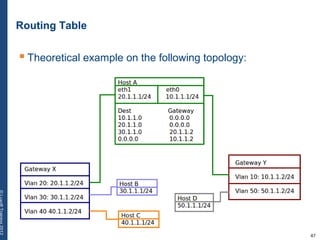
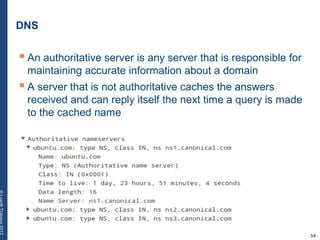
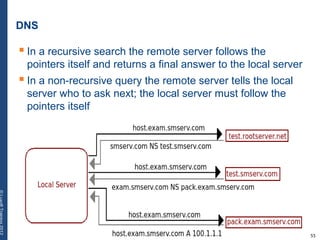
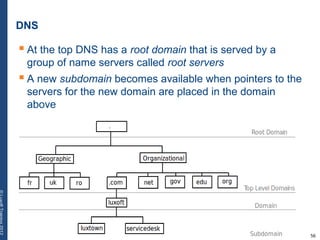
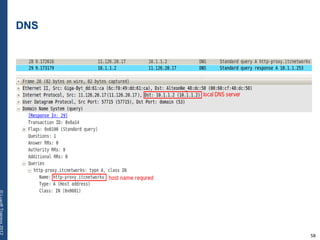
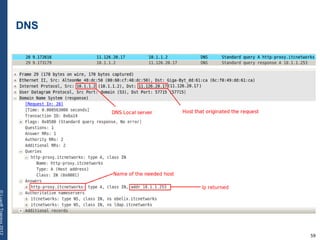
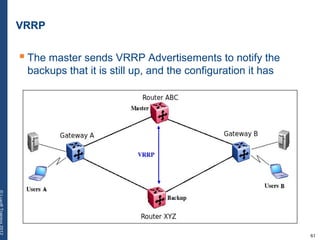
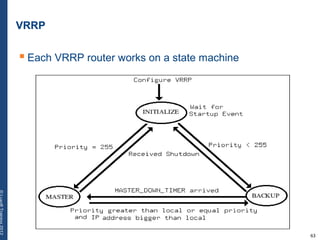
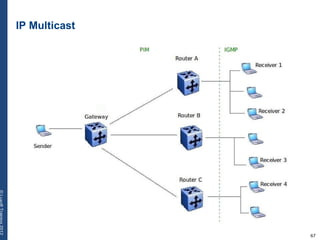
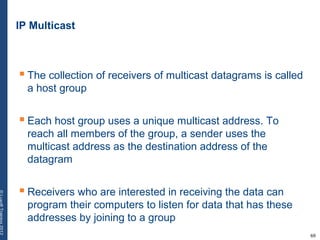
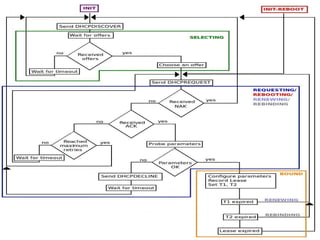
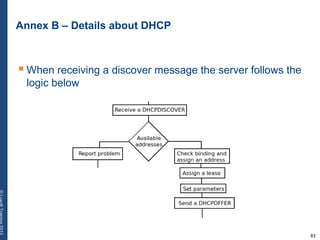
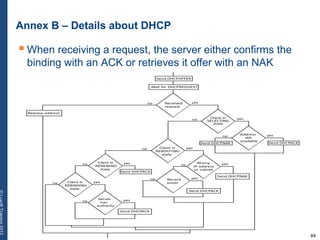
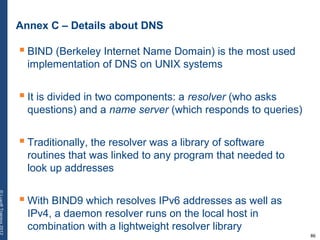
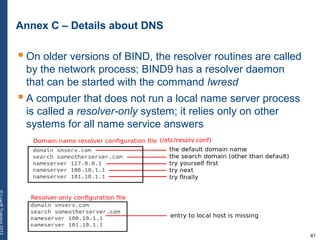
The document provides a comprehensive overview of basic networking concepts, including telecommunications history, OSI and TCP/IP models, MAC and VLAN specifics, and routing protocols. It covers key topics such as ARP, DHCP, ICMP, DNS, and IP multicast, offering insights into their functionalities and operations in network communication. Additionally, it discusses practical implications like routing decisions, DHCP client-server interactions, and the use of VRRP for increasing network reliability.