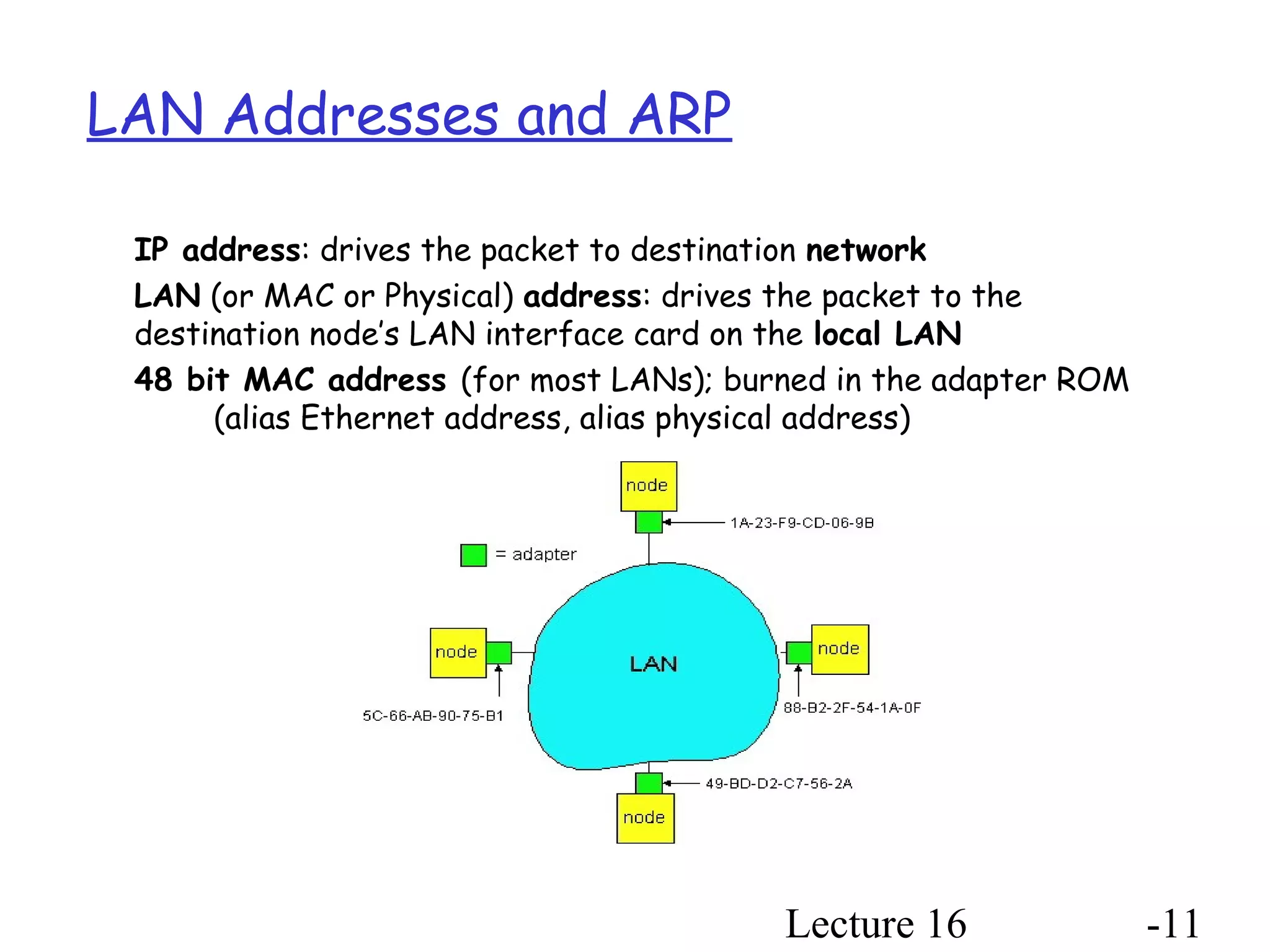
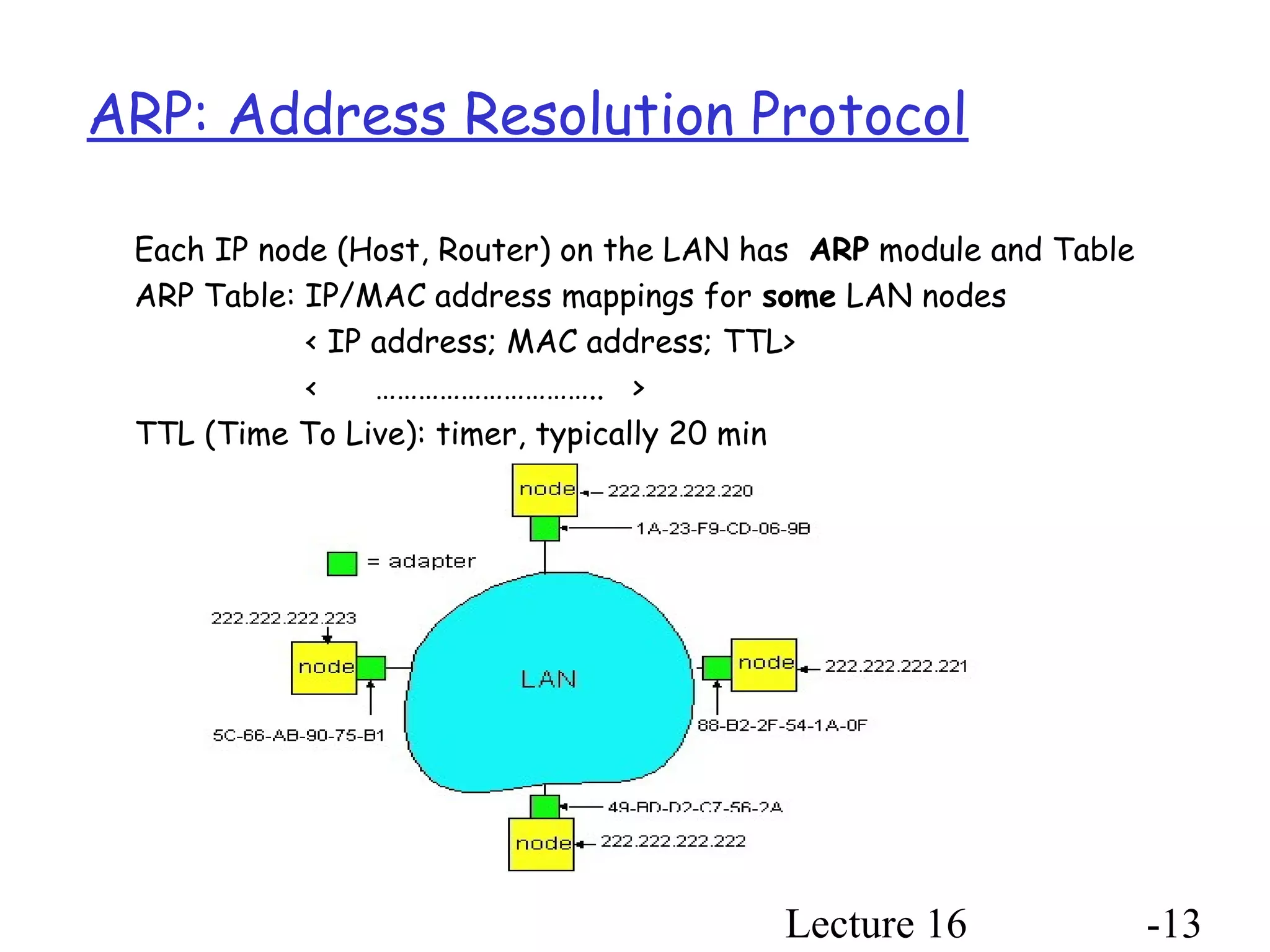
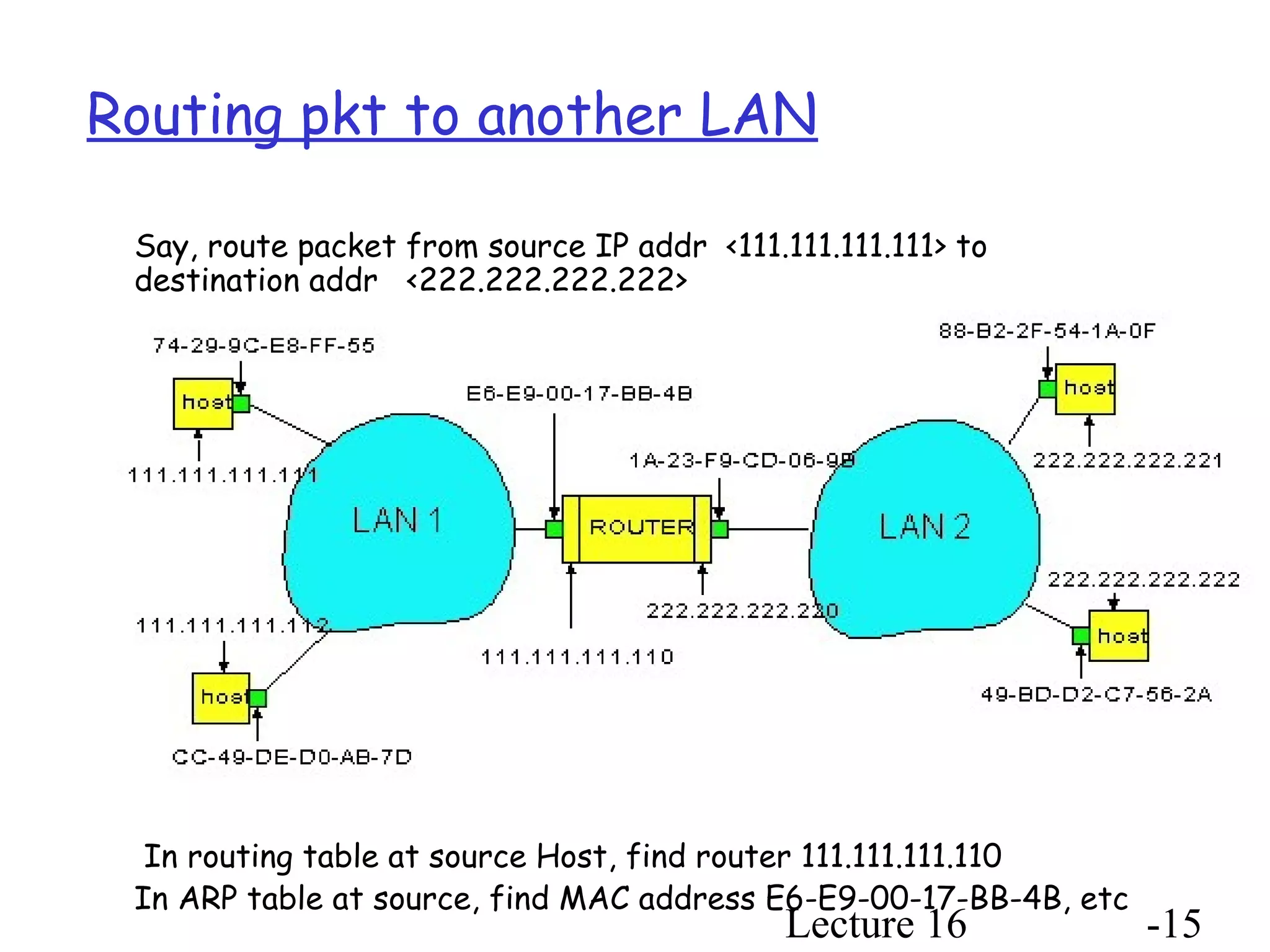
This document discusses different types of random access MAC protocols: Slotted Aloha, Pure Aloha, CSMA, and CSMA/CD. It also covers taking turns MAC protocols like polling and token passing. Key points include:
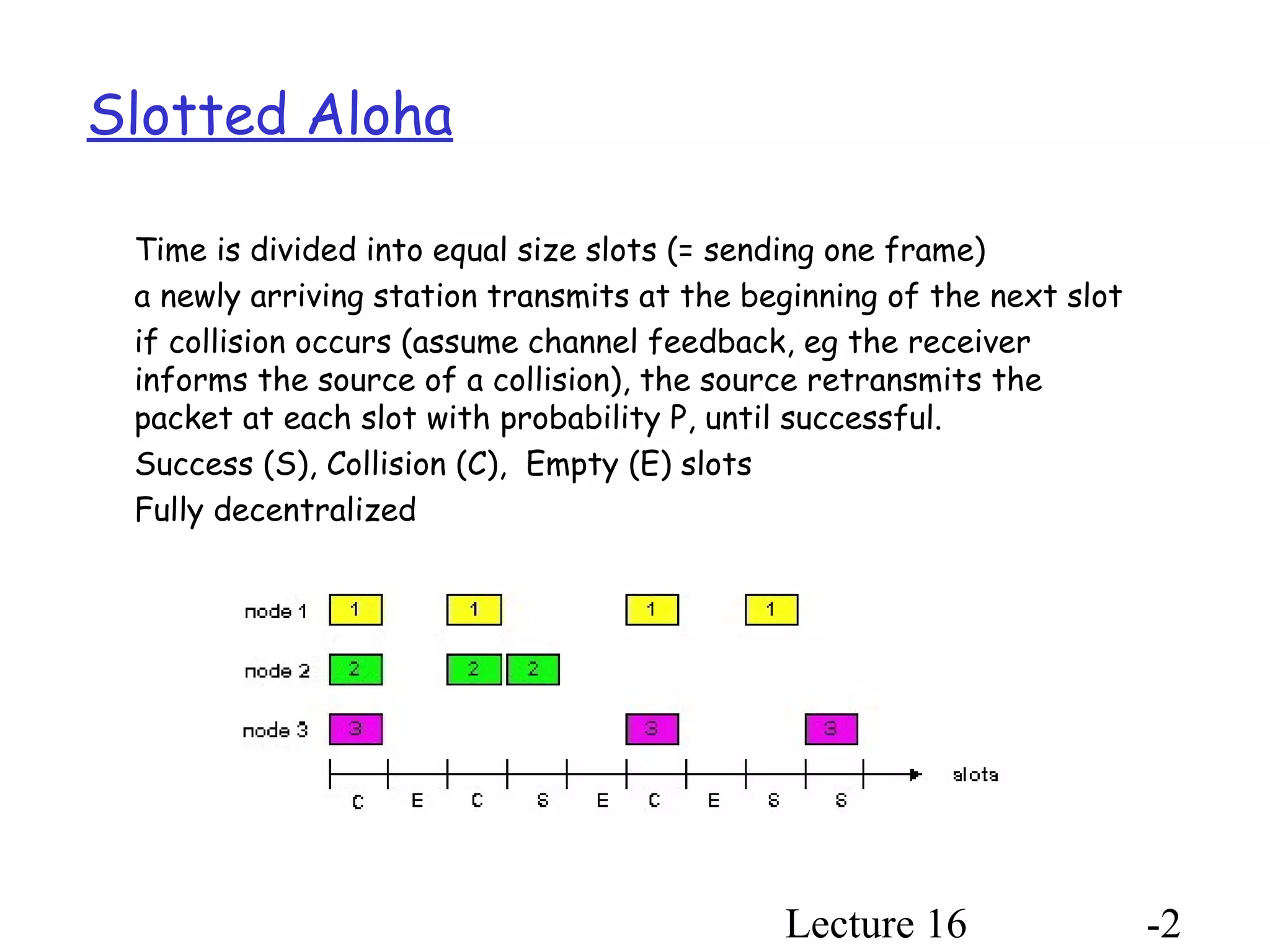
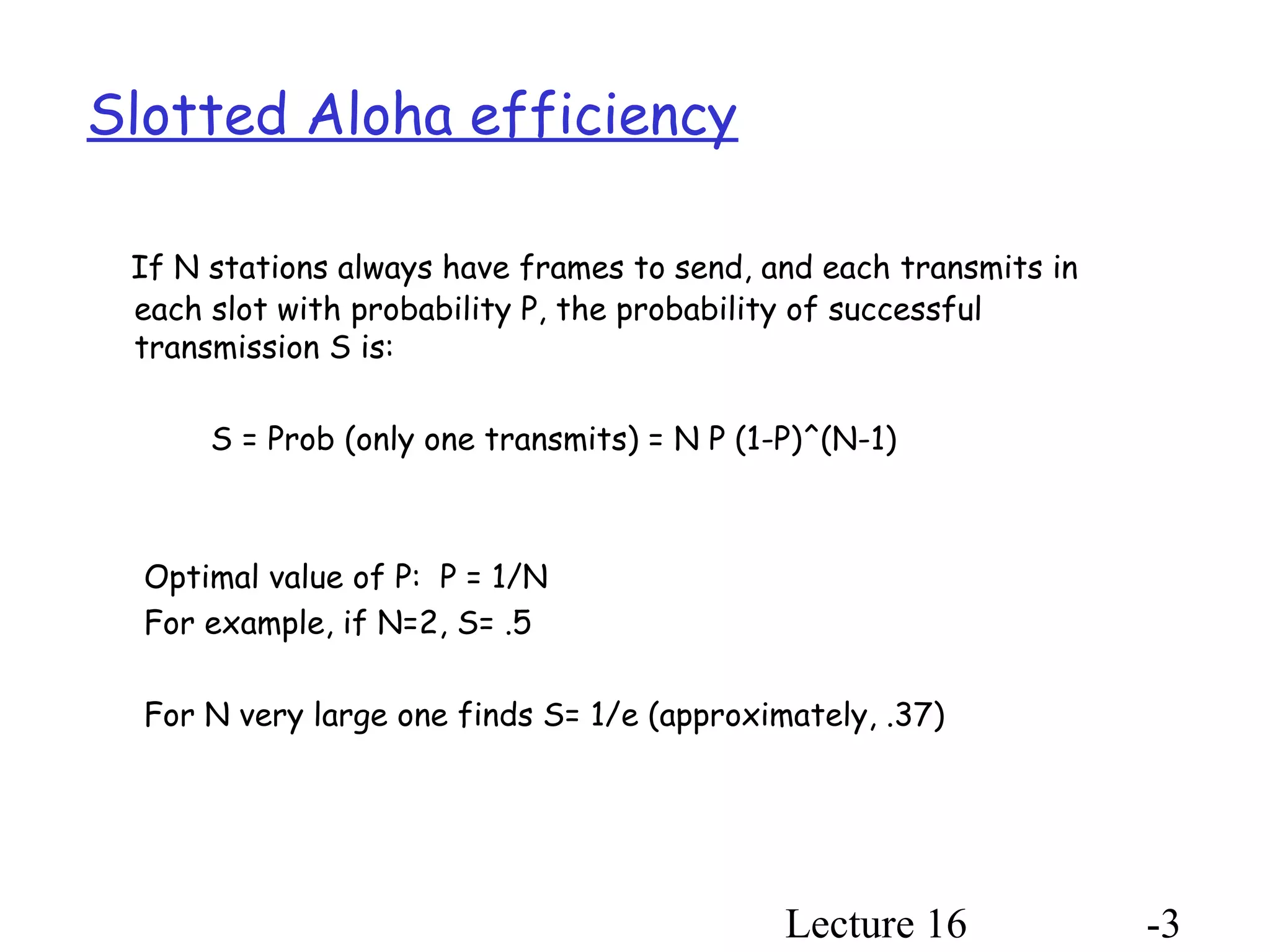
- Slotted Aloha divides time into slots and stations transmit at slot boundaries to avoid collisions. Optimal transmission probability is 1/N where N is number of stations.
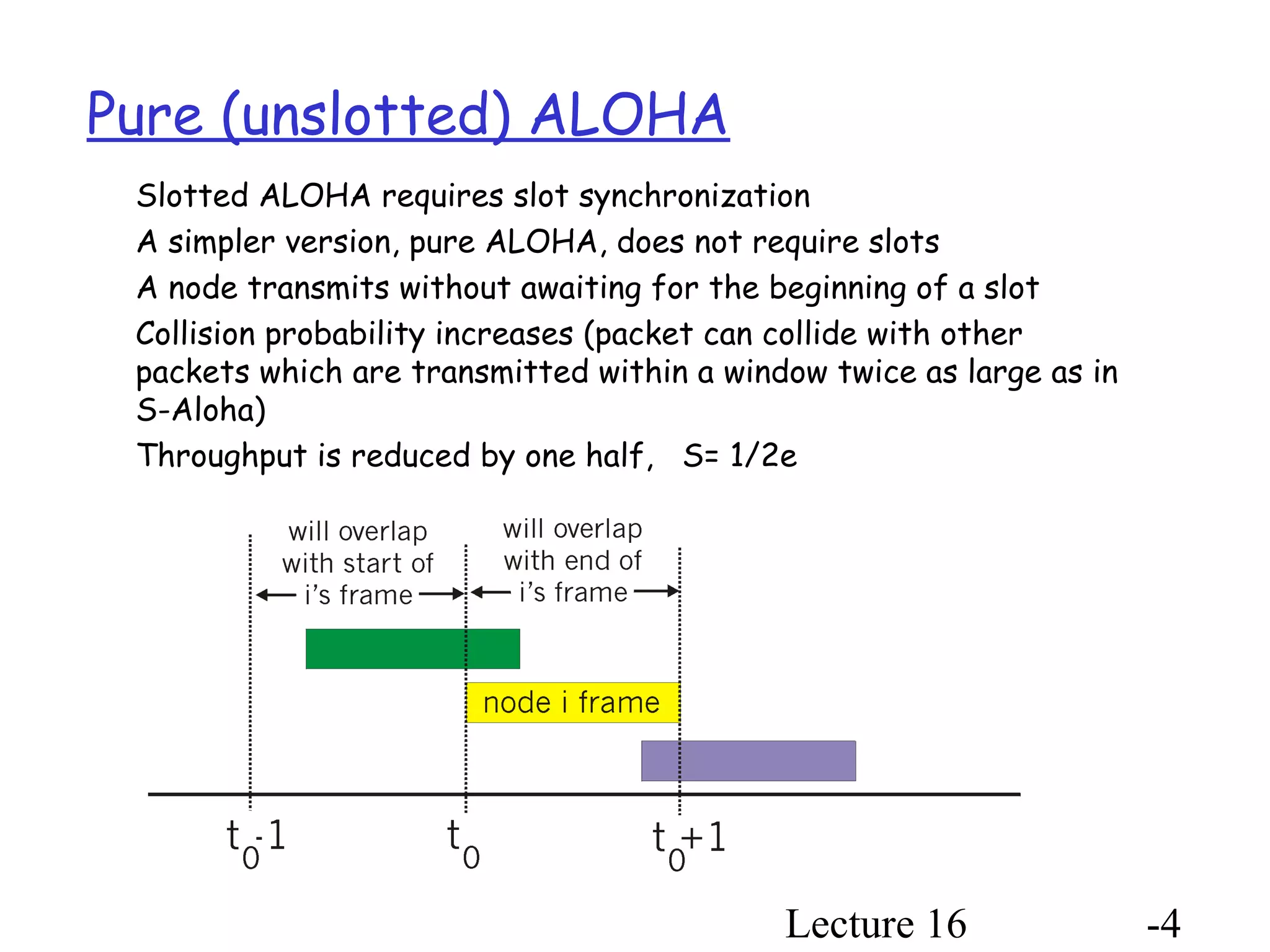
- Pure Aloha does not use slots, increasing collision probability and reducing throughput.
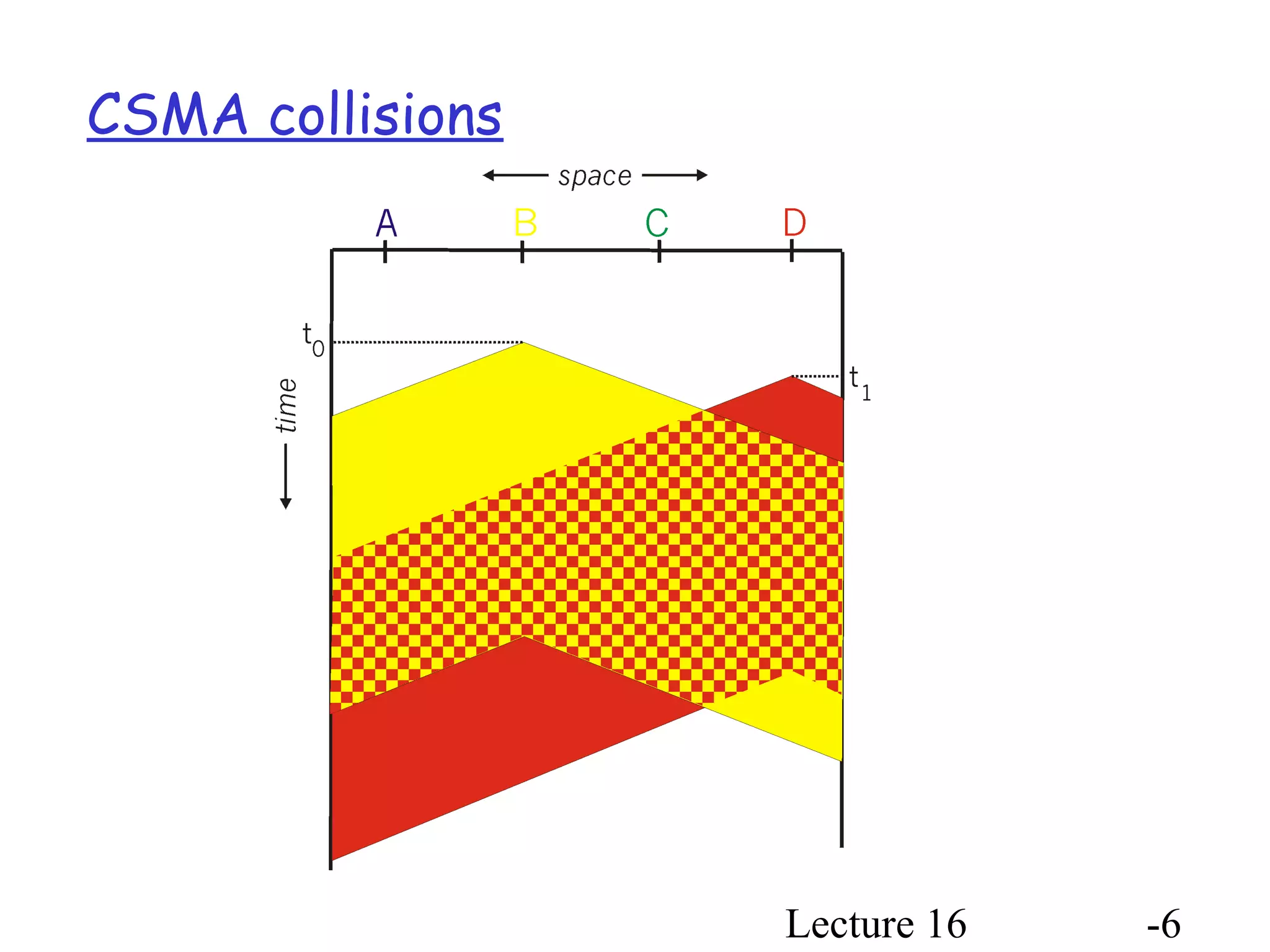
- CSMA involves listening before transmitting to avoid collisions but they can still occur if two stations sense the channel idle simultaneously.
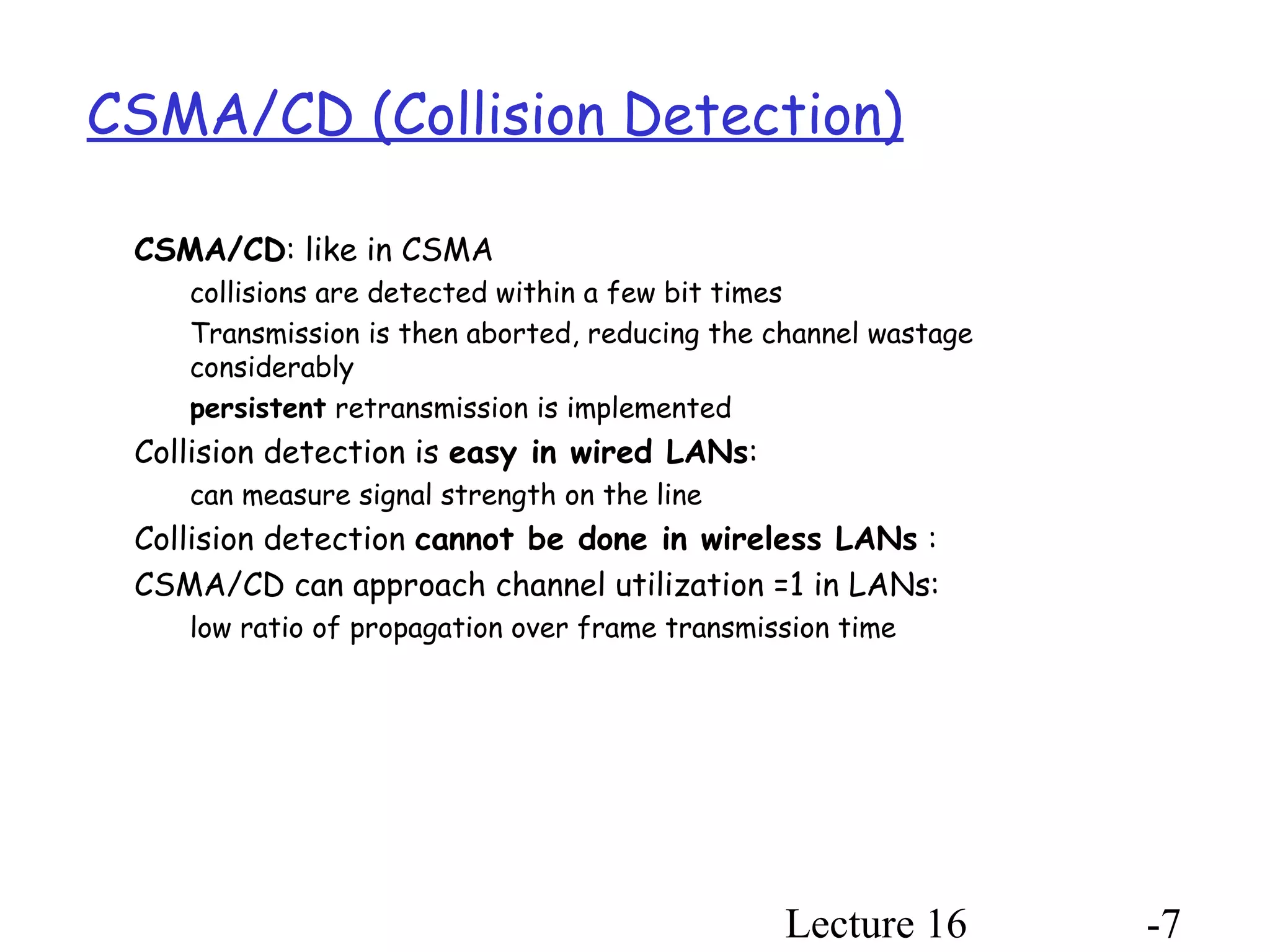
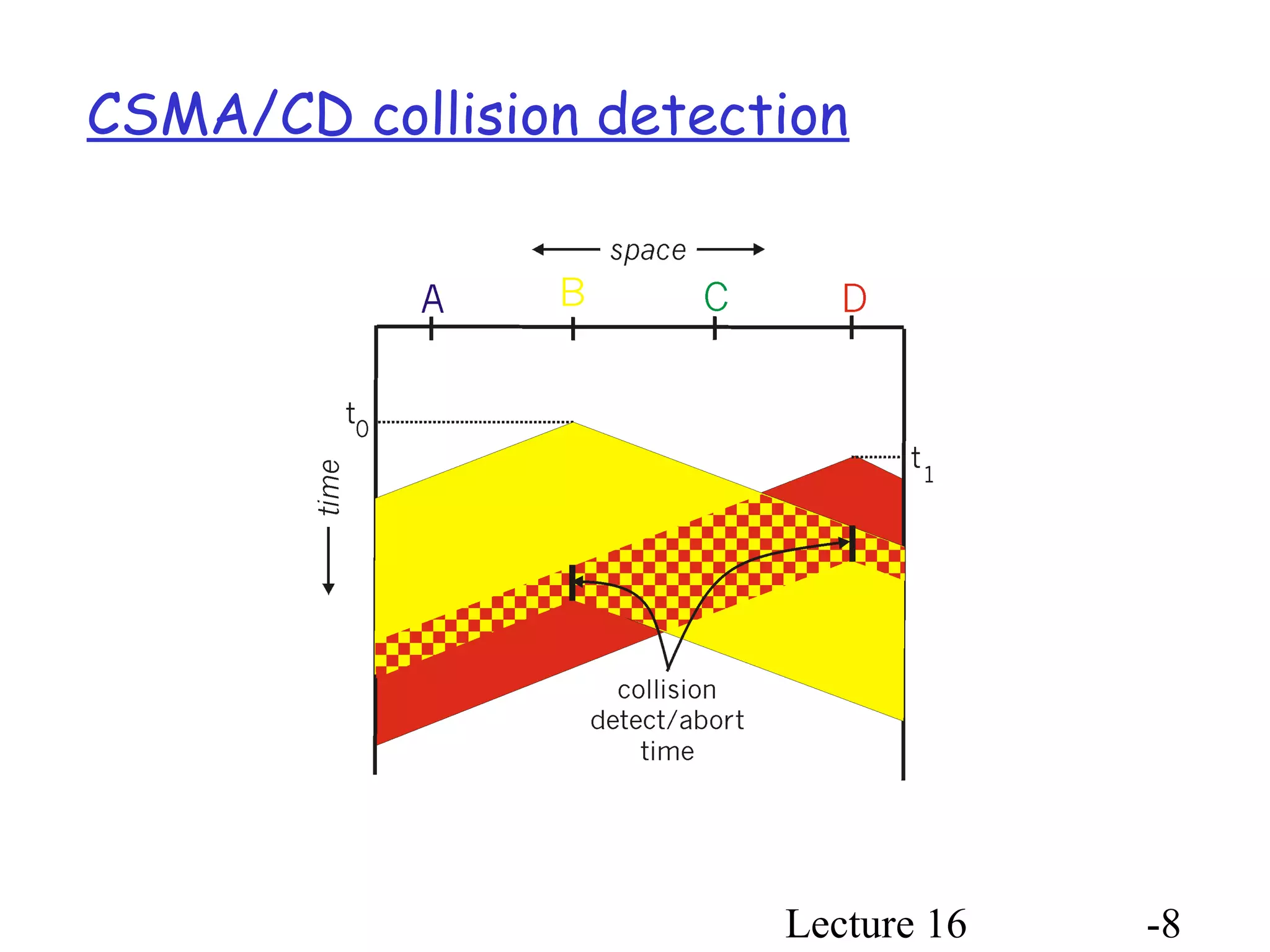
- CSMA/CD adds collision detection, allowing transmitters to abort