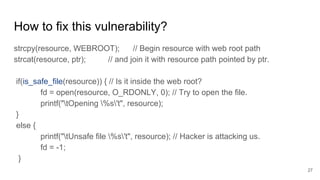
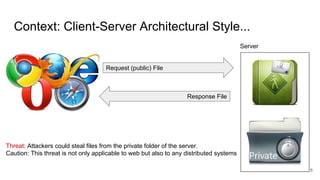
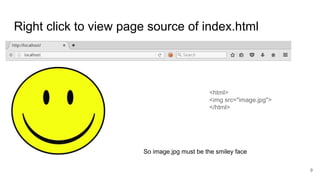
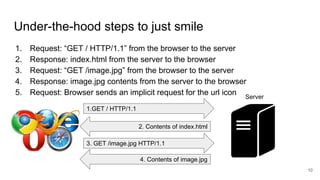
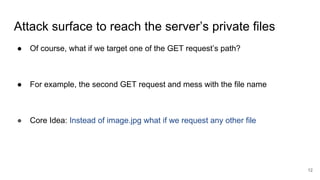
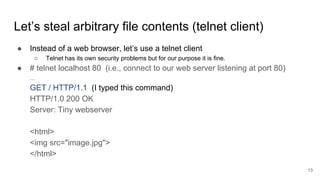
The document discusses remote file path traversal attacks, demonstrating how attackers can exploit web servers to steal sensitive files. It explains the vulnerabilities associated with file path concatenation and emphasizes the need for secure coding practices such as canonicalizing file names and validating file access. The author provides strategies for preventing these attacks and highlights increased coding effort required for secure applications compared to traditional coding.






![Let’s steal server’s /etc/passwd using a telnet client
# telnet localhost 80
...
Connected to localhost.
Escape character is '^]'.
GET /../../../etc/passwd HTTP/1.1
HTTP/1.0 200 OK
Server: Tiny webserver
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
...
Contents of the
/etc/passwd
exposed
14](https://image.slidesharecdn.com/remotefilepathtraversalattacksforfunandprofit-170802022233/85/Remote-file-path-traversal-attacks-for-fun-and-profit-14-320.jpg)




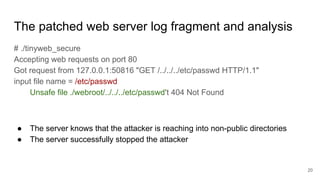
![The patched web server stopped the exploit
# telnet localhost 80
Trying ::1...
Trying 127.0.0.1...
Connected to localhost.
Escape character is '^]'.
GET /../../../etc/passwd HTTP/1.1
HTTP/1.0 404 NOT FOUND
Server: Tiny webserver
<html><head><title>404 NOT Found</title></head><body><h1>URL not
found</h1></body></html>
Connection closed by foreign host 19](https://image.slidesharecdn.com/remotefilepathtraversalattacksforfunandprofit-170802022233/85/Remote-file-path-traversal-attacks-for-fun-and-profit-19-320.jpg)