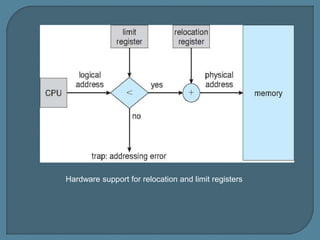
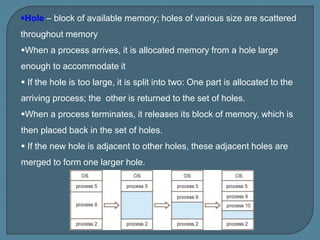
The document discusses various methods for managing contiguous memory allocation, focusing on logical and physical addresses, and the use of relocation and limit registers for memory protection. It outlines memory partitioning strategies, including fixed-sized partitions and different allocation strategies like first-fit, best-fit, and worst-fit, along with issues of fragmentation. Compaction techniques and noncontiguous memory allocation are suggested as solutions to external fragmentation challenges.