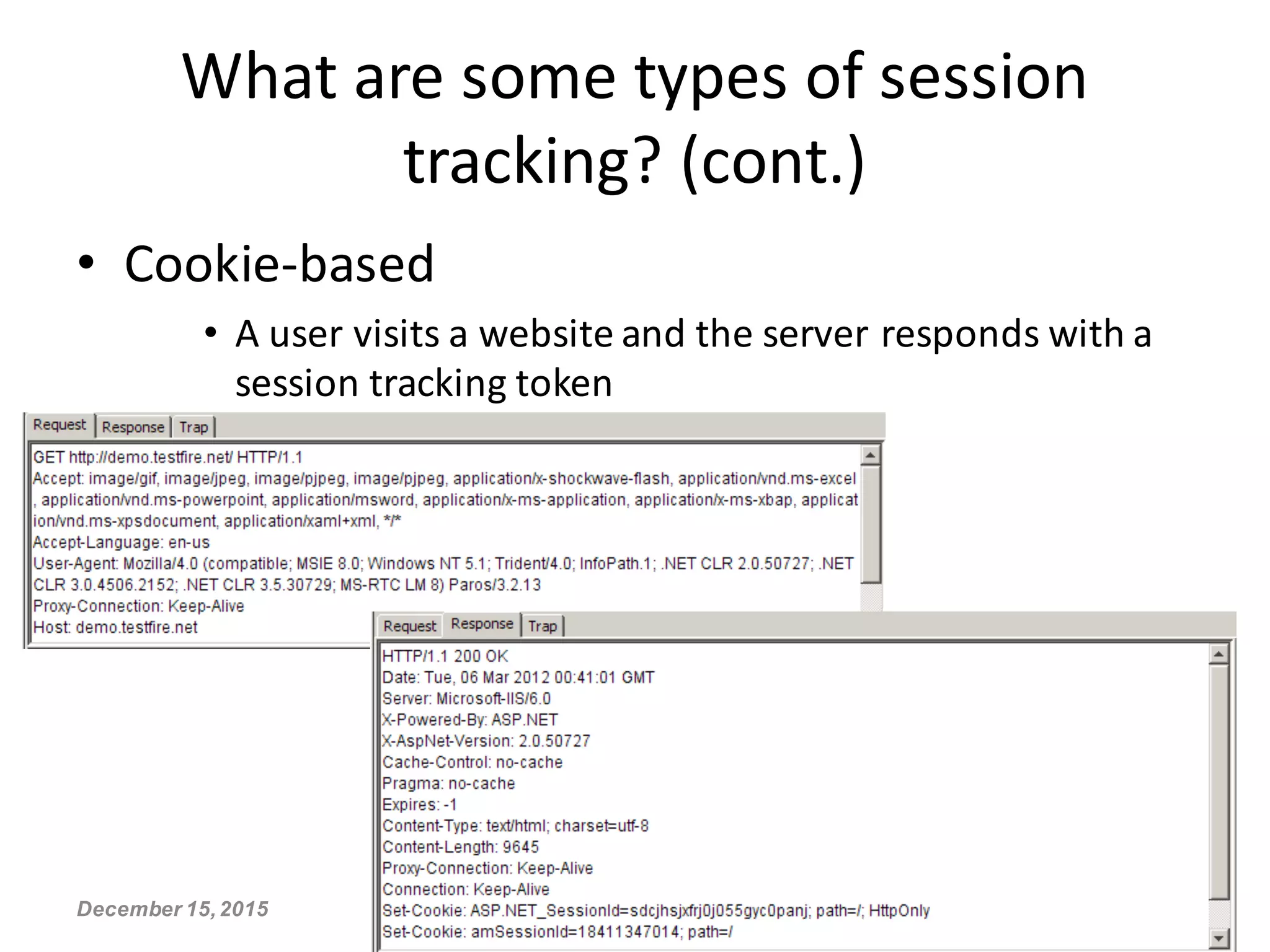
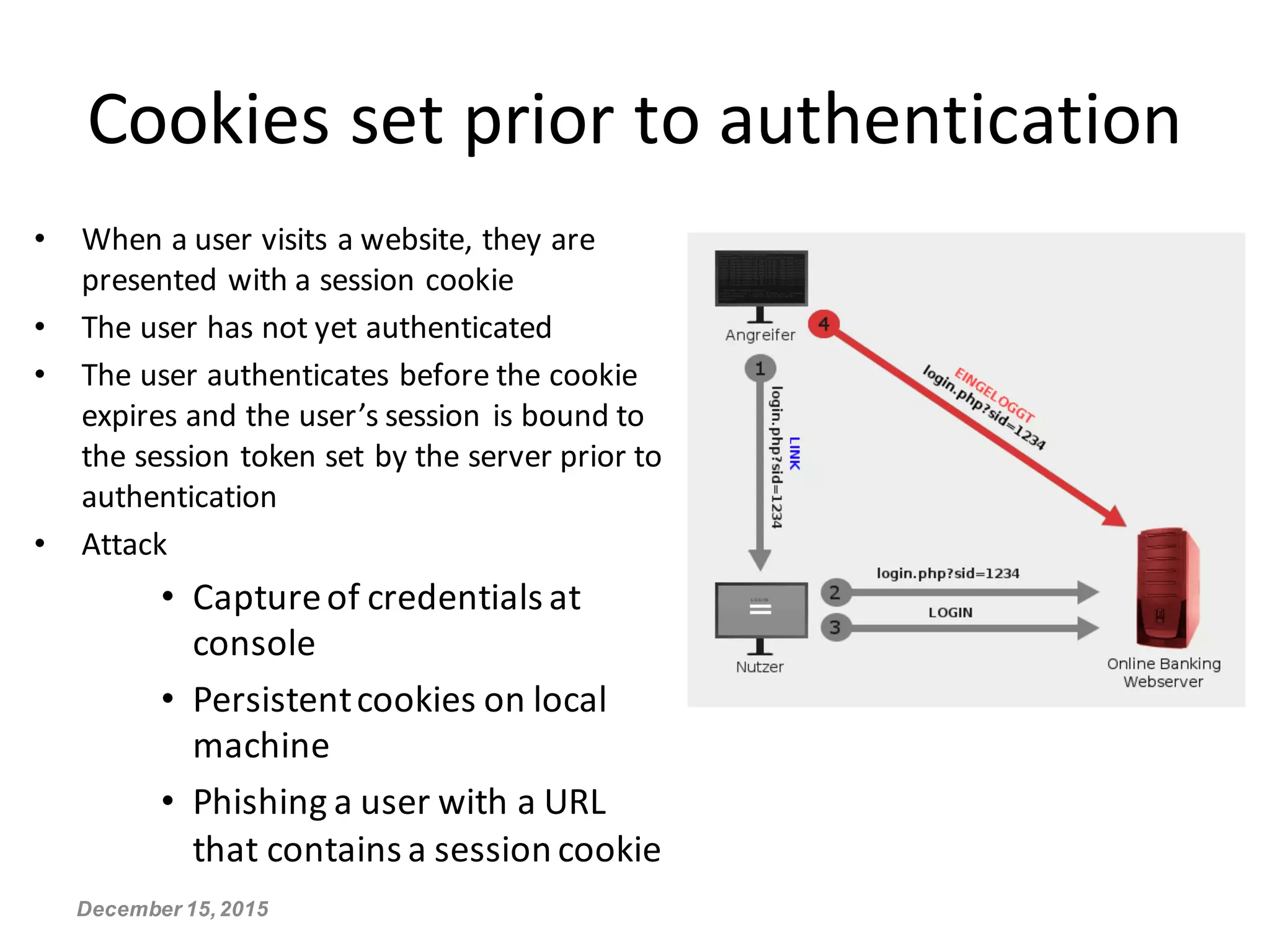
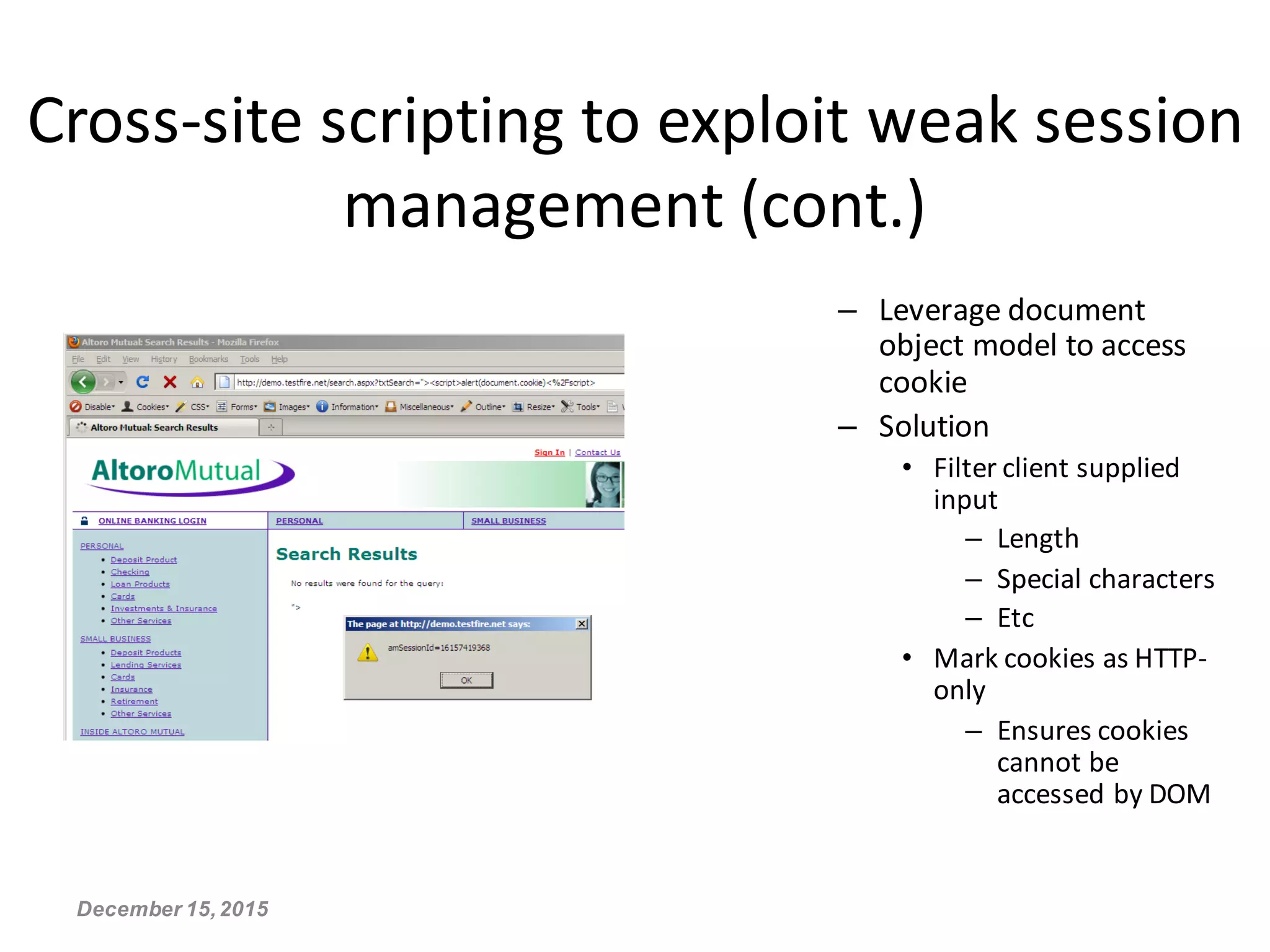
This document discusses secure session management and common session security issues. It explains that capturing a user's session allows an attacker to act as that user. Sessions need to be properly terminated on logout to prevent replay attacks. Weaknesses like cookies set before authentication, non-random session IDs, and failing to remove sessions on logout can enable session hijacking. The document provides guidelines for generating secure random session IDs, setting cookies only after authentication, removing sessions on logout, and using HTTPS to mitigate these risks.