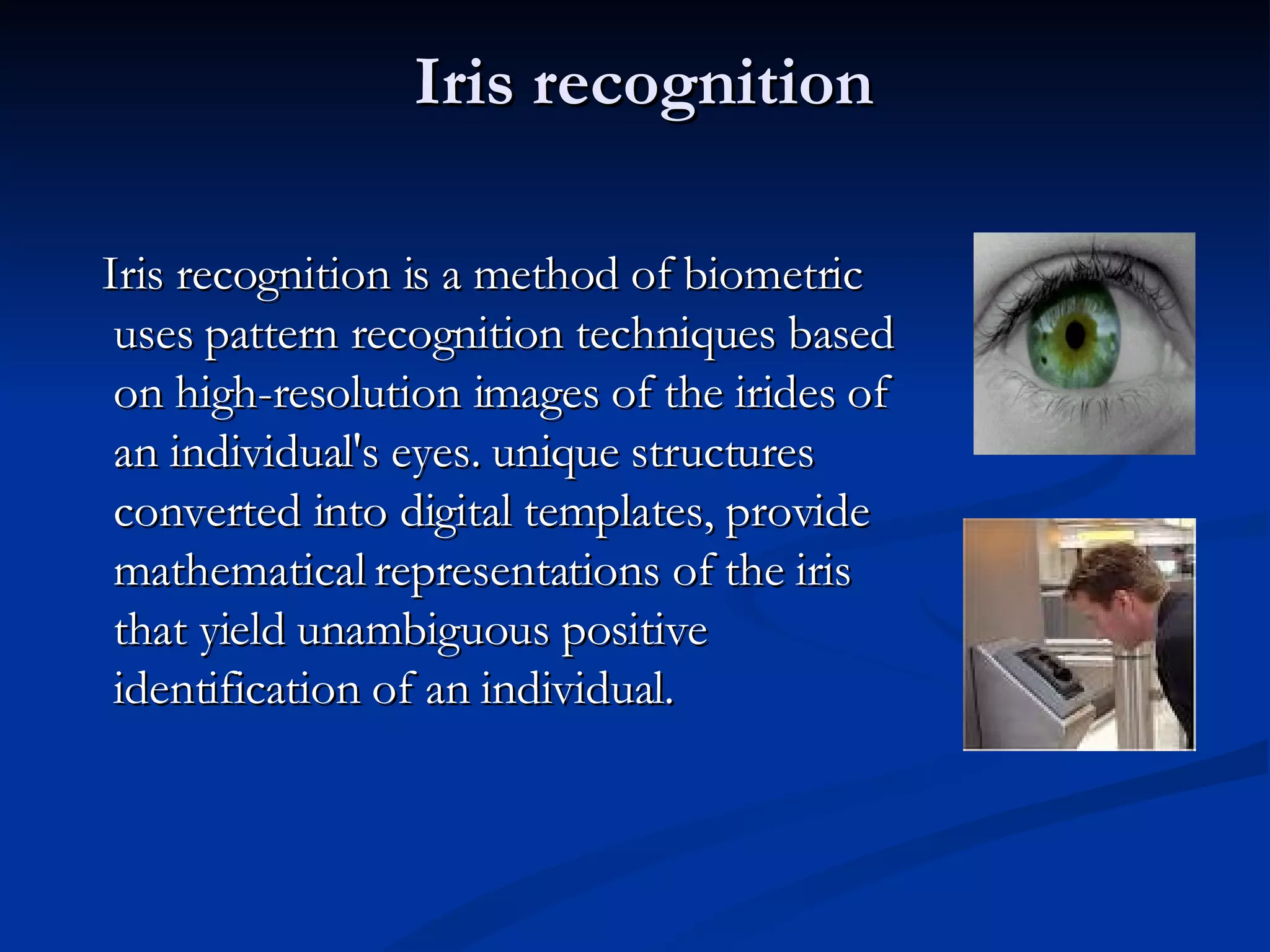
This document provides an overview of biometrics including what biometrics is, why it is used, the history of biometrics, common biometric techniques (e.g. fingerprints, iris scans, facial recognition), and advantages and disadvantages of each technique. It discusses identification vs verification uses of biometrics and covers physical, behavioral, and emerging biometric methods. The document concludes that biometrics provides desirable security characteristics and will continue growing in use for mobile devices, buildings, and more in the coming years.

![BIOMETRICS BY A.V.AJAY KIRAN [email_address]](https://image.slidesharecdn.com/biometrics-1204020769238243-5/75/Biometrics-2-2048.jpg)