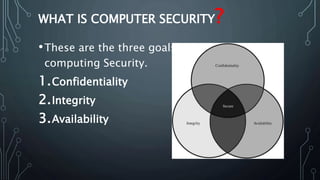
This document discusses basic concepts in computer security. It defines computer security as techniques for ensuring data cannot be read or compromised without authorization, usually through encryption and passwords. The three main goals of computer security are confidentiality, integrity, and availability. Vulnerabilities are weaknesses that can be exploited, and threats are circumstances with potential to cause harm. Common threats include interception, interruption, modification, and fabrication. Controls are protective measures used to reduce vulnerabilities, and physical security and security methods like antivirus software and firewalls can help secure computers.