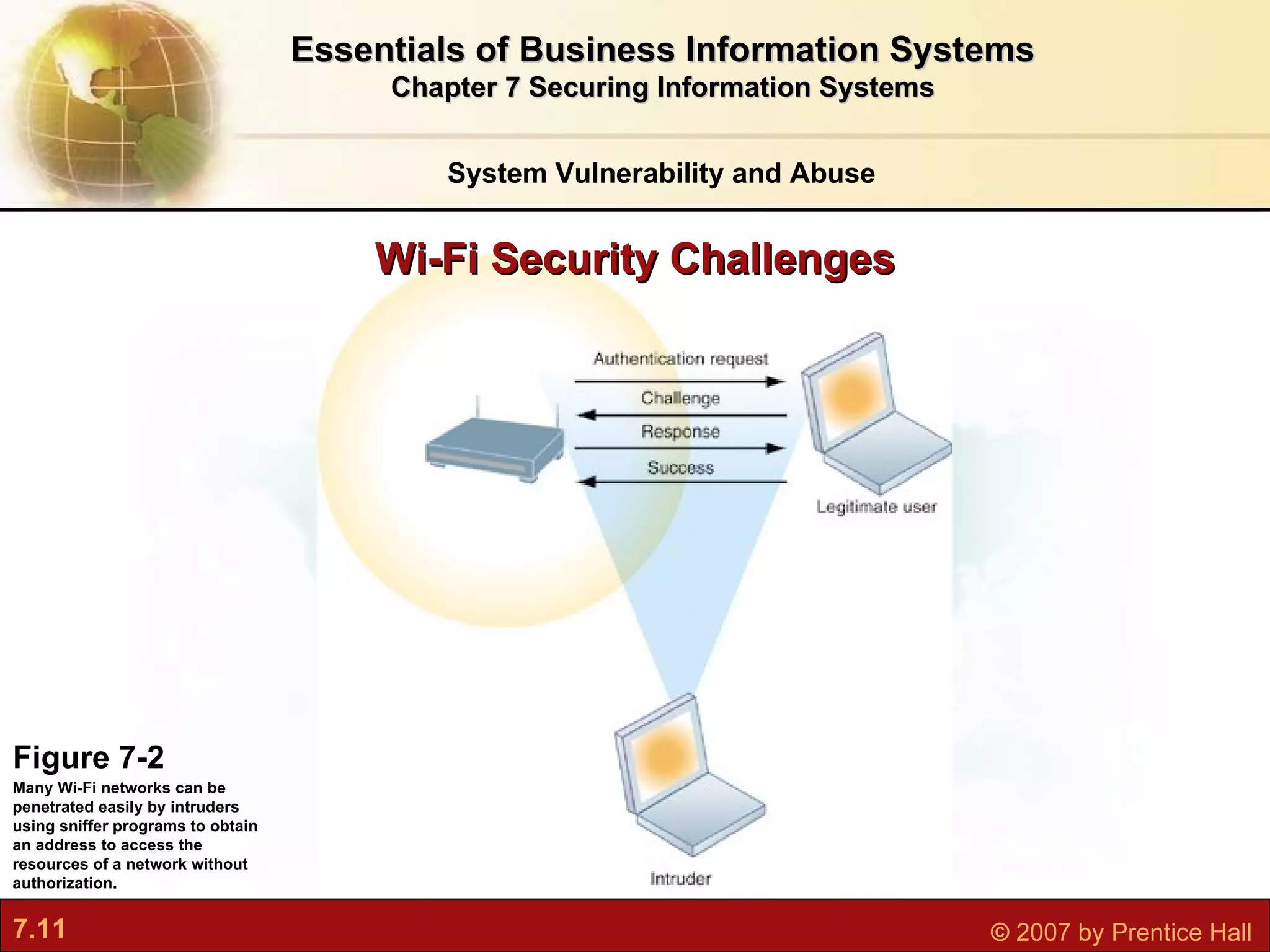
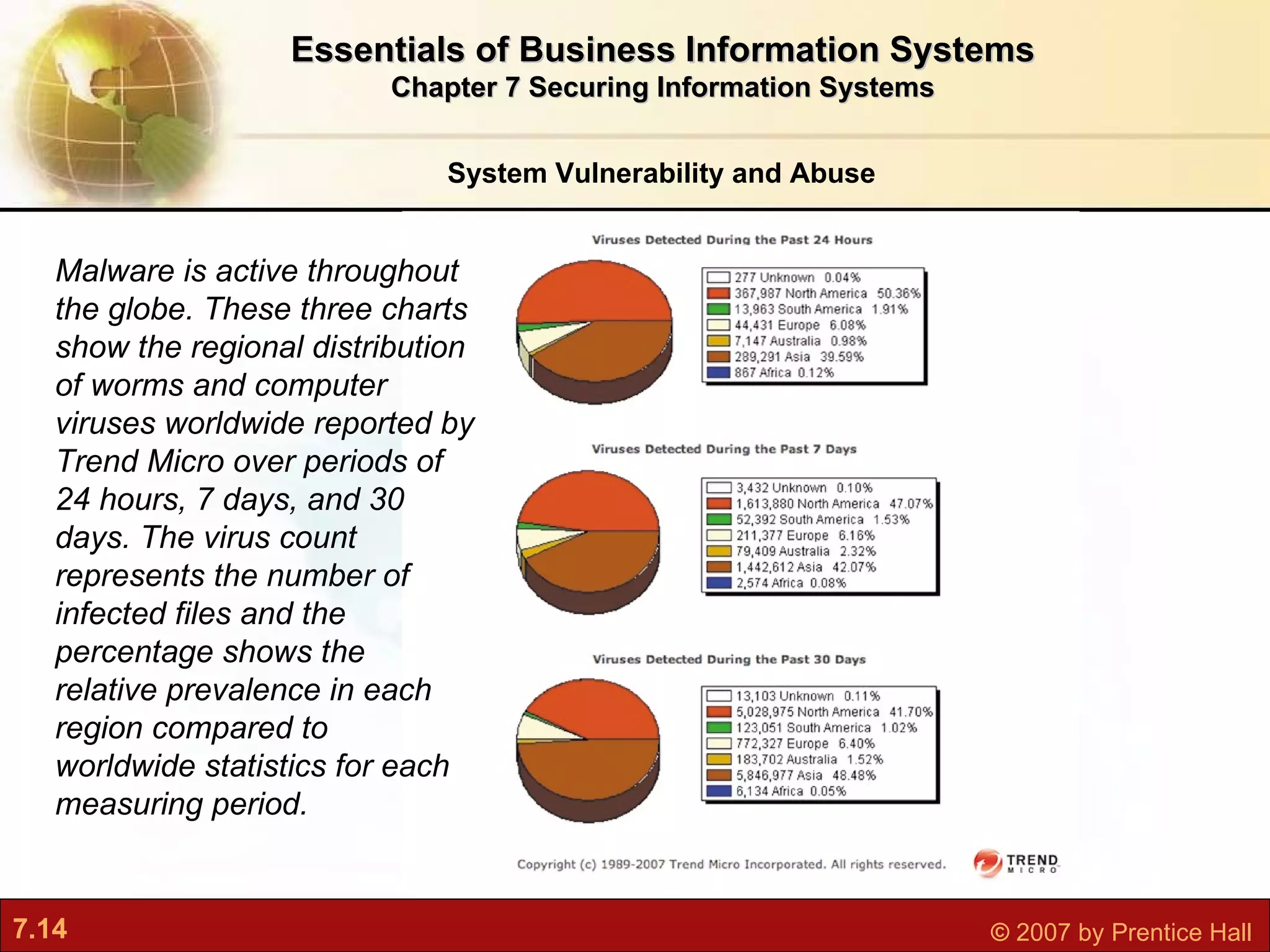
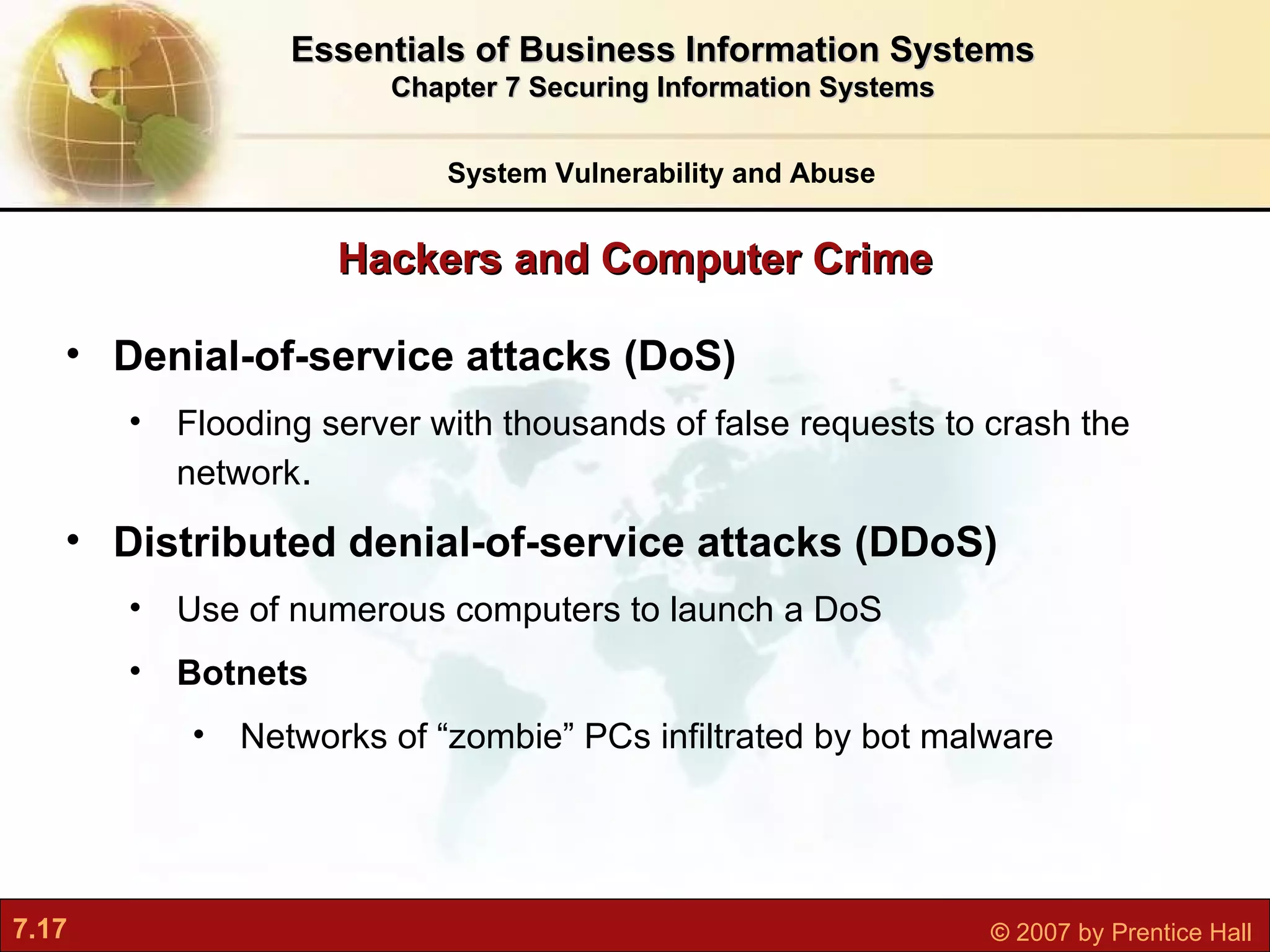
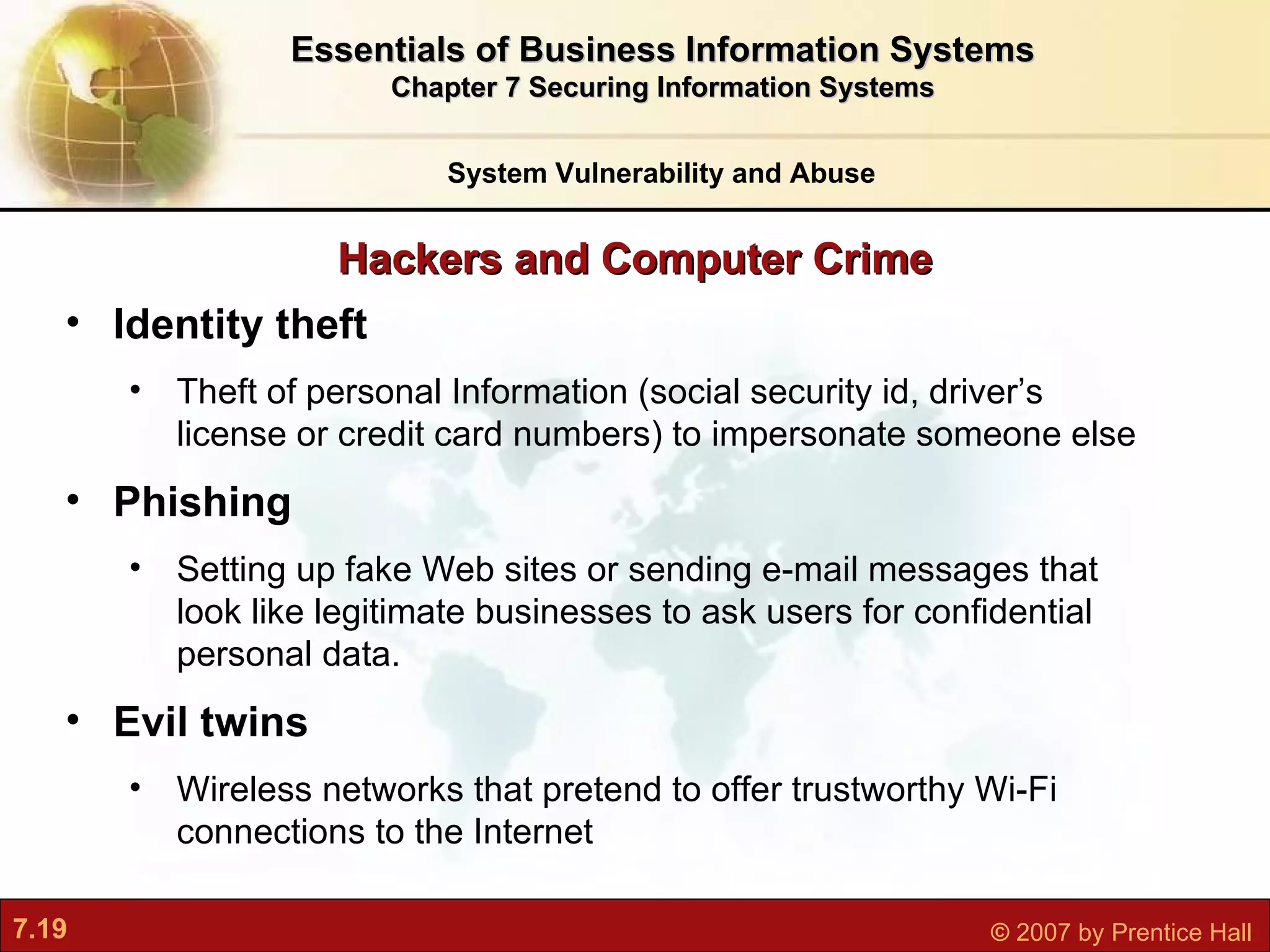
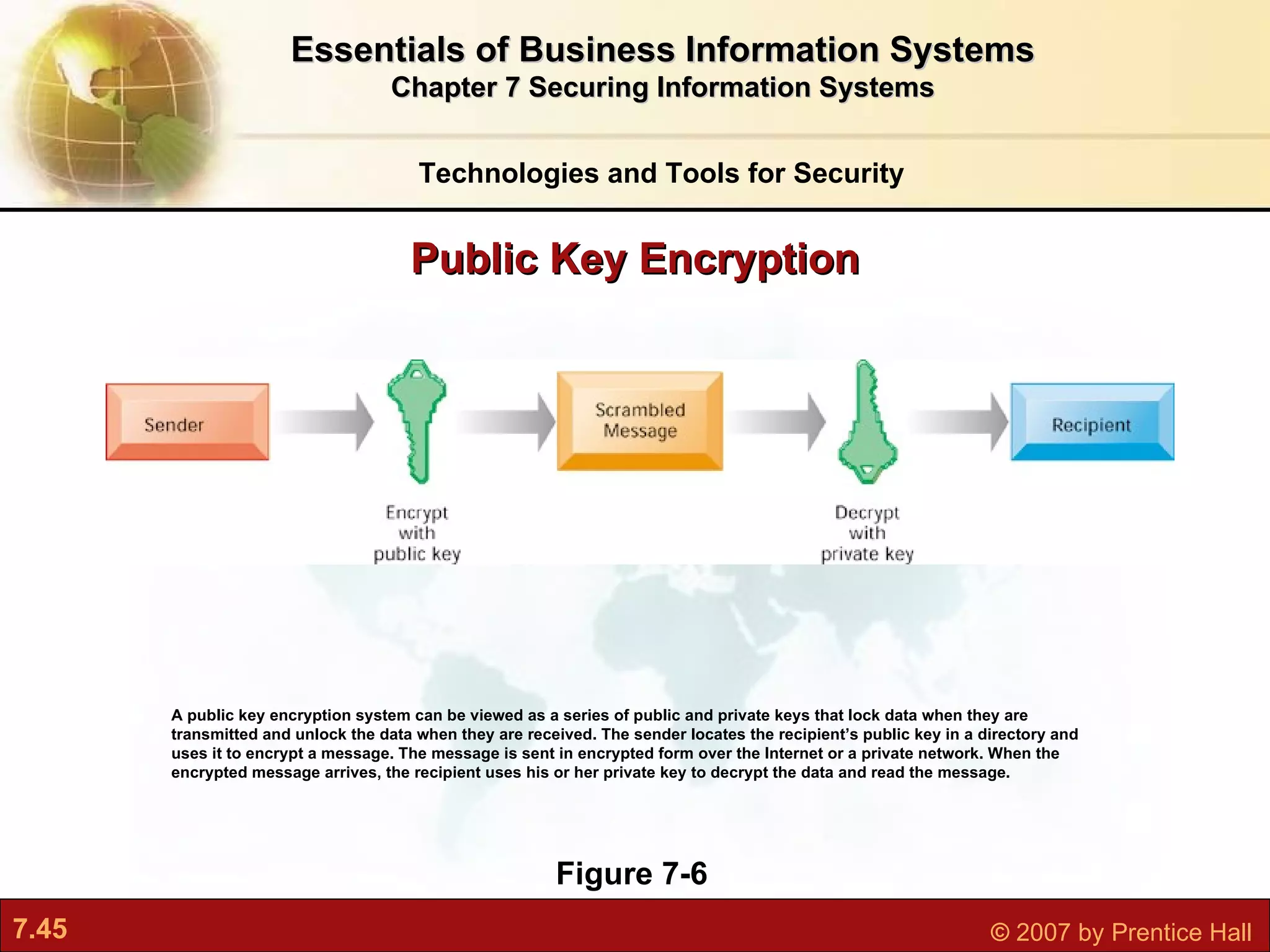
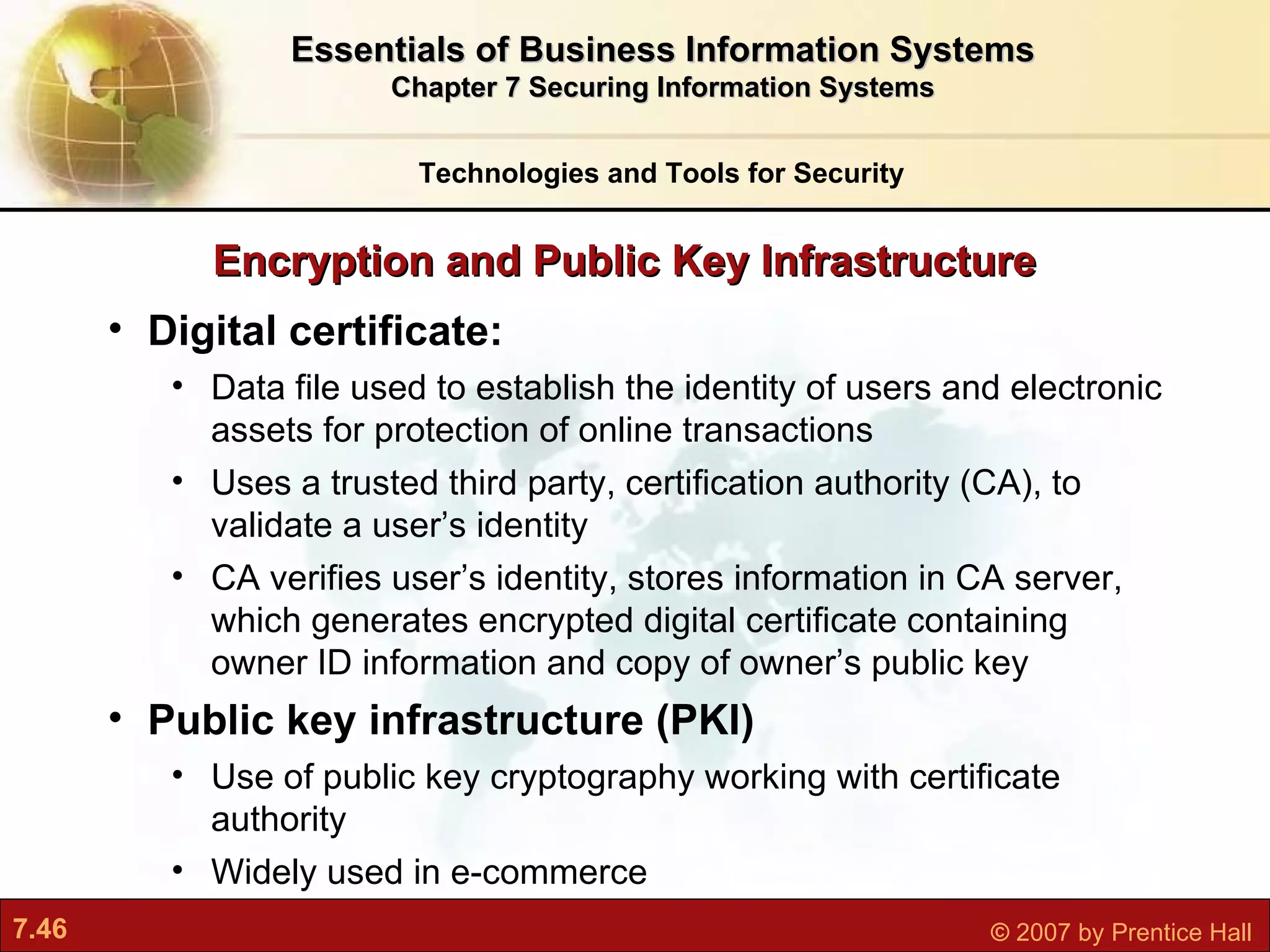
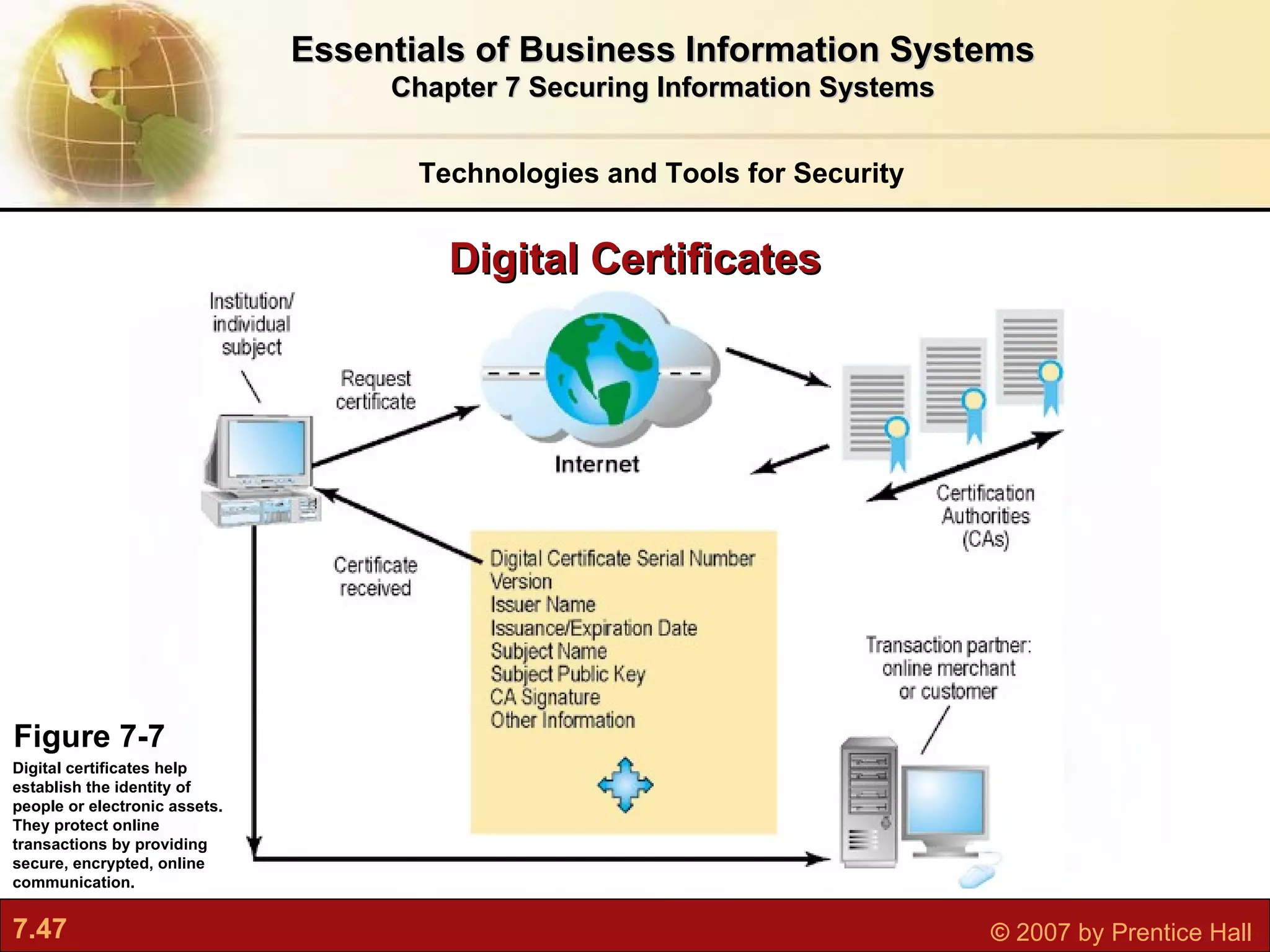
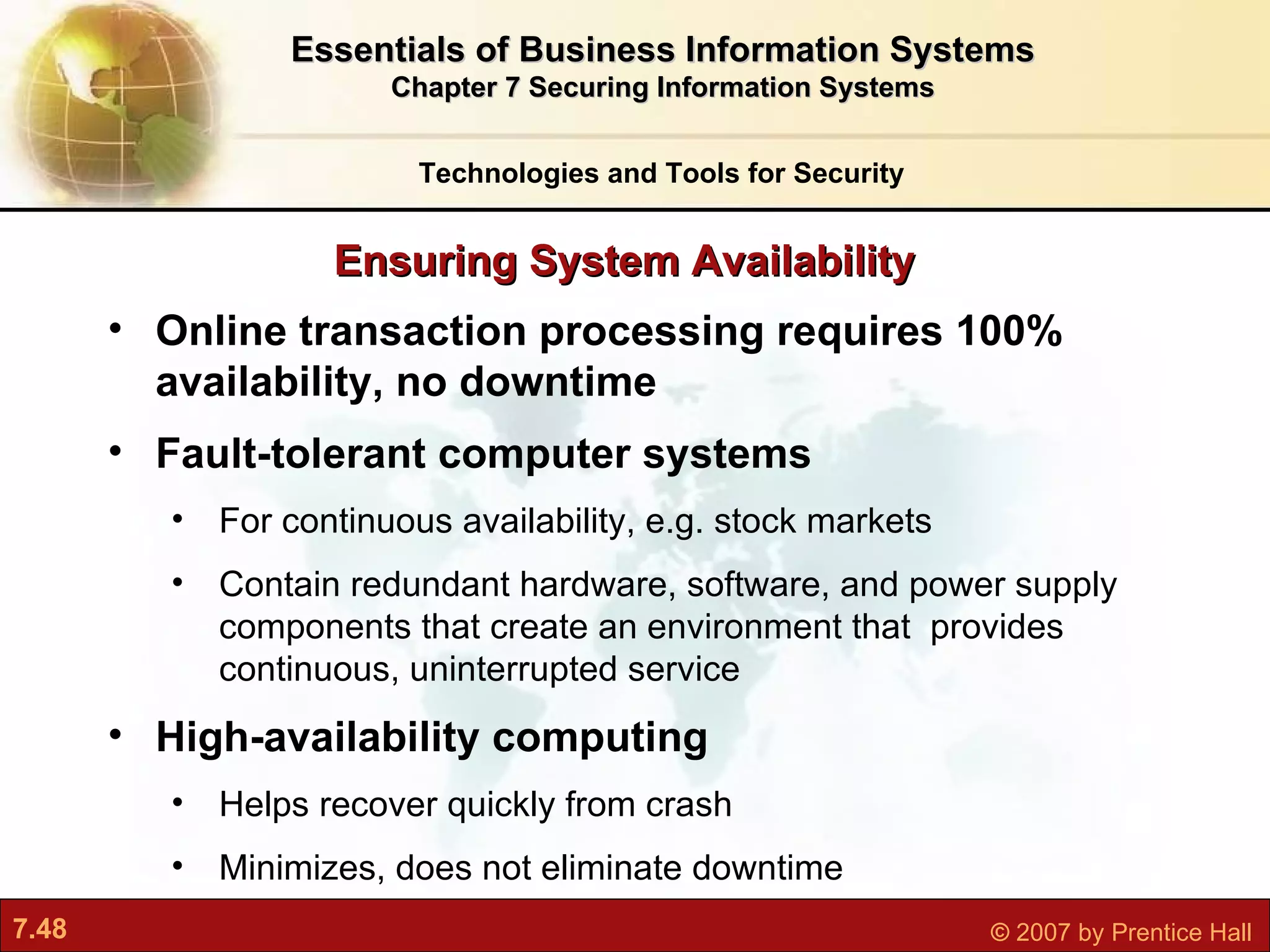
This document discusses securing information systems and provides an overview of security concepts and tools. It covers system vulnerabilities, threats like malware and hackers, establishing security frameworks, and technologies to safeguard systems like firewalls, encryption, and digital certificates. The key topics are securing systems from internal and external threats, implementing controls and policies, and using technical tools to protect information assets and ensure system availability.