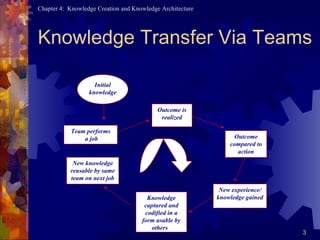
Knowledge is created through teamwork as teams compare experiences to outcomes, translating experiences into knowledge. Knowledge is then transferred to other teams via codification and reuse.
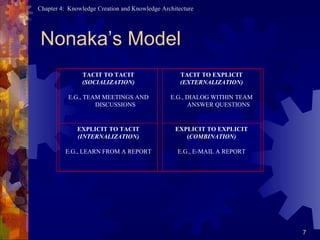
Nonaka's model of knowledge conversion includes tacit to tacit knowledge through socialization like team meetings, tacit to explicit through externalization via team dialogs, explicit to tacit through internalization by learning from reports, and explicit to explicit through combination like emailing reports.
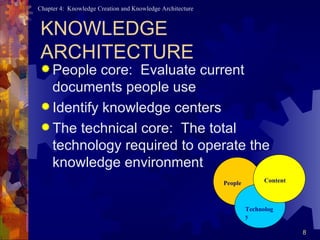
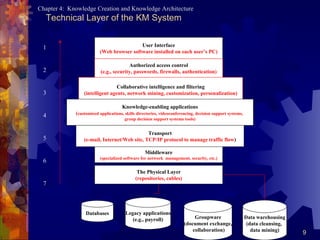
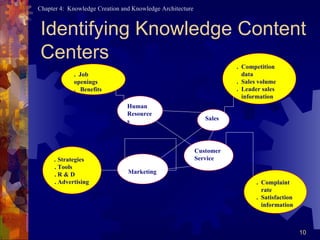
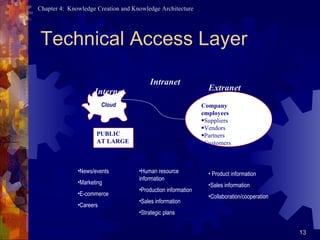
A knowledge architecture includes people as the core, a technical core layer with user interfaces, applications, transport and physical repositories, and a content layer identifying knowledge centers in areas like marketing, HR, R&D and more.