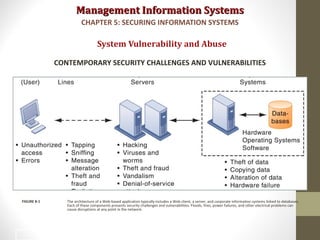
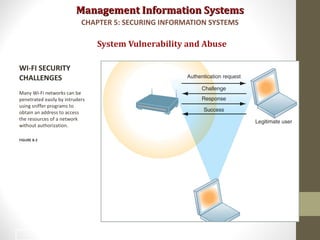
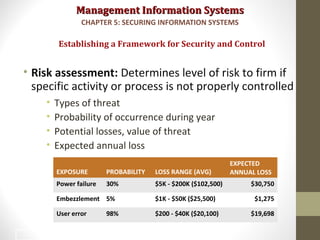
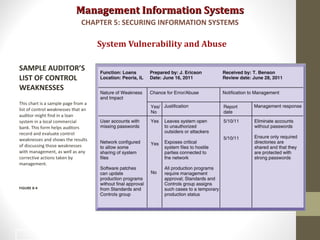
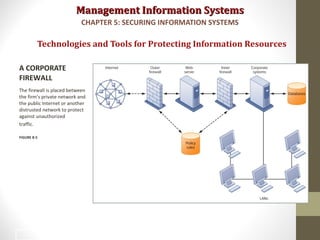
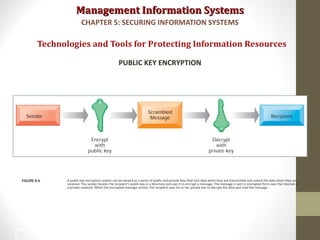
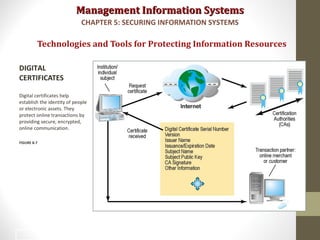
This document discusses security challenges for information systems. It describes how systems are vulnerable through accessibility of networks, software and hardware problems, and disasters. Specific threats are discussed like hacking, malware, identity theft, and internal threats from employees. The document also outlines security controls and policies needed to protect systems and mitigate risks from threats.