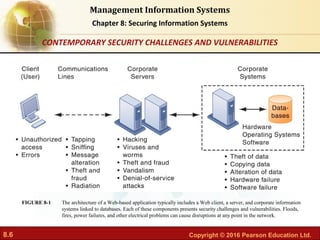
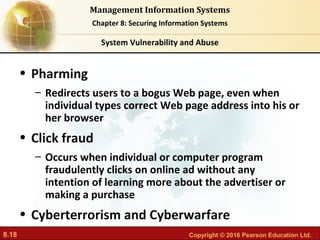
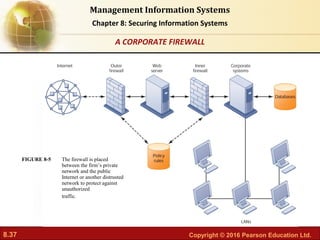
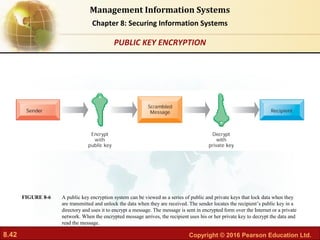
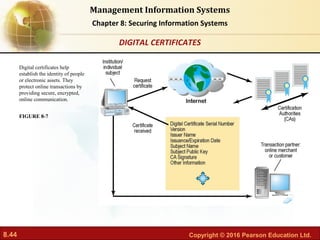
The document discusses security challenges for information systems, including vulnerabilities from hackers, malware, and system flaws. It describes the need for organizations to implement security frameworks including policies, controls, identity management, auditing and disaster recovery planning to protect digital assets and comply with legal requirements. Specific tools mentioned for safeguarding information include identity management software, authentication methods like passwords and biometrics, and security profiles to restrict user access.