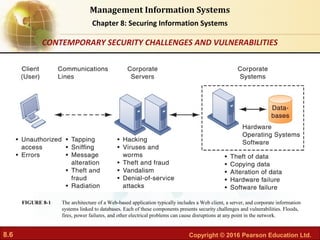
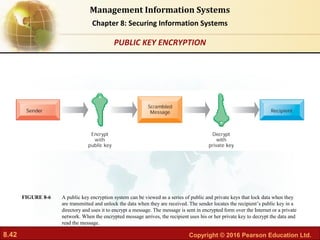
This document discusses security frameworks and tools for information systems. It begins by explaining why systems are vulnerable, such as accessibility of networks and software/hardware problems. It then describes organizational frameworks for security, including risk assessment, security policies, identity management, disaster recovery planning, and information systems audits. Finally, it discusses tools for safeguarding resources, such as identity management software. The document provides an overview of securing information systems from multiple perspectives.