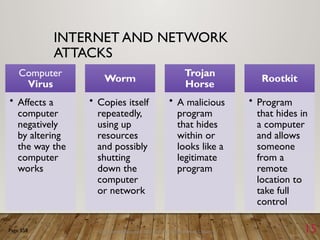
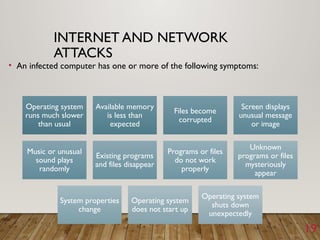
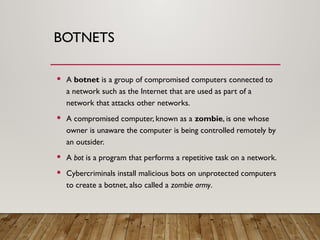
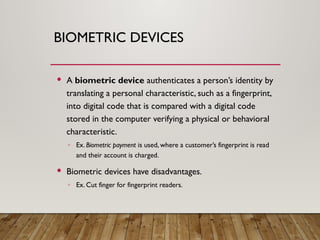
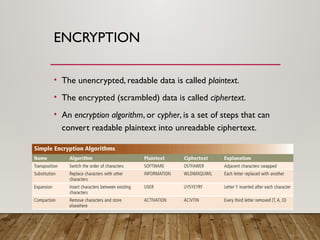
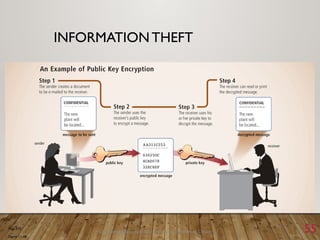
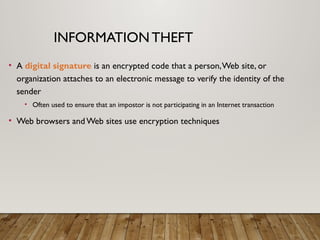
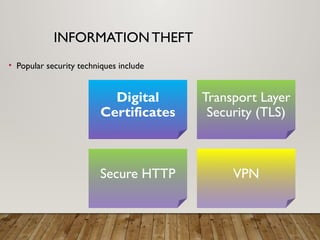
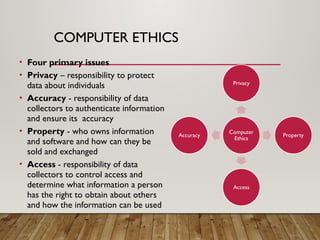
The document outlines a lecture on computer security covering topics such as types of computer crimes, their societal costs, ethical considerations for IT professionals, and methods to enhance data security and integrity. It details various computer security risks, including malware, unauthorized access, and software theft, along with preventative measures like encryption and digital signatures. Additionally, the lecture emphasizes the importance of ethics in computing and the implications of software ownership and licensing.