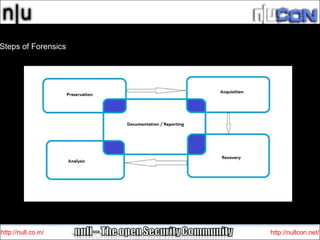
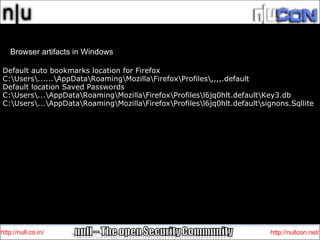
This document summarizes Windows forensic artifacts and tools that can be used for forensic investigations. It discusses the steps of a forensic investigation, rules to follow, common Windows artifacts like event logs and browser artifacts, and tools that can extract user details and system activity from a disk image or memory dump. Examples of artifacts that can be examined without tools include mounted devices, USB storage details, task manager history, event logs and system files.
![Windows Forensic Artifacts http://null.co.in/ http://nullcon.net/ Pardhasaradhi.ch a.k.a babloo 09762310104 [email_address]](https://image.slidesharecdn.com/windowsforensicartifacts-111125003743-phpapp02/85/Windows-forensic-artifacts-1-320.jpg)









![Thank You Pardhasaradhi.ch 09762310104 www.pardhasaradhi.info [email_address]](https://image.slidesharecdn.com/windowsforensicartifacts-111125003743-phpapp02/85/Windows-forensic-artifacts-13-320.jpg)