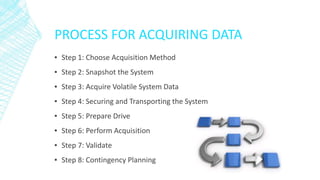
Digital evidence acquisitions can be stored in raw, proprietary, or Advanced Forensics Format (AFF). The document discusses various acquisition methods and tools for disk-to-image, disk-to-disk, logical, and sparse acquisitions. It emphasizes the importance of validation, contingency planning, and minimizing alteration of evidence during the acquisition process. Special considerations are given for acquiring data from RAID systems and using Linux tools or remote network tools.