The document serves as an introduction to network forensics, aiming to educate on techniques, evidence acquisition, and analysis within the field of digital forensics and incident response. It covers foundational concepts such as the OSI model, types of evidence, and the acquisition and analysis processes using tools like Wireshark. Additionally, the document includes practical exercises aimed at reinforcing the theoretical knowledge presented.




![DIGITAL FORENSICS VS. INCIDENT RESPONSE
Cyber
Forensics
Incident
Response
Sub-discipline of law
Sub-discipline of
disaster recovery
“Post-mortem”
Post or concurrent
to incident
Typically
independent
analysis
Working closely
with IT to control
situation
Must adhere to
rules of evidence
[federal, daubert,
etc.]
Must only be as
reliable as necessary
to determine a
course of action
End Goal:
Determine
sequence of events,
attest.
End Goal: determine
threat extent,
mitigate threat](https://image.slidesharecdn.com/purduetecsupnetforensics-140226070448-phpapp01/85/Network-Forensics-Intro-7-320.jpg)



![QUICK REVIEW: FUNDAMENTAL COMPUTING
LIGHTNING TALKS
Computing
Processing, Storage, and Transmission [I/O]
Systems of Systems
Information
Has both Content and Context that we are interested in
Content – things the user/entity/protocol directly creates, accesses, or
modifies
Context – metadata that frames the content, providing a point of
reference & relativity
Cyber
The man-machine interface – adding people to the mix](https://image.slidesharecdn.com/purduetecsupnetforensics-140226070448-phpapp01/85/Network-Forensics-Intro-13-320.jpg)
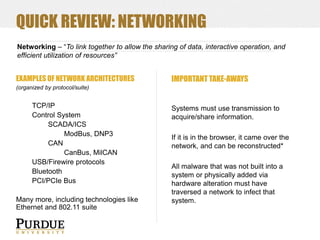
![QUICK REVIEW: NETWORKING (CONT’D)
TCP/IP NETWORKING AND THE OSI MODEL
For today’s exercises, we are only looking at Ethernet/TCP/IP
Several different models exist for defining these networking layers logically – we are going
to focus on the Open Systems Interconnection (OSI) model (slightly modified)
Why does this matter?
[
Logically grasping a unified model of internetworking
fundamentally shapes your process for searching, identifying, acquiring,
and understanding evidence, and your interactions with the tools used
to acquire and analyze that evidence.
]](https://image.slidesharecdn.com/purduetecsupnetforensics-140226070448-phpapp01/85/Network-Forensics-Intro-15-320.jpg)
![QUICK REVIEW: NETWORKING (CONT’D)
The OSI Model of networking for the Internet
[Layer 8] – Human
Layer 7 – Application
e
n
c
a
p
s
u
l
a
t
i
o
n
Layer 6 – Presentation
Layer 5 – Session
Layer 4 - Transportation
Layer 3 – Network
Layer 2 – Data-link
Layer 1 – Physical
[Layer 0] – Media
The OSI Model is typically
composed of 7 layers, with each upper
layer being encapsulated in the
subsequent layer below it (or the next
lowest layer to it).
We’ve modified the OSI model to meet
our needs by adding 2 layers. “Layer 8” is
a concept out of Social Engineering, but
also applies to Forensic investigations.
“Layer 0” is the physical media and can
hold traditional forensic evidence like
latent fingerprints, but can also tell us
about unique constraints.](https://image.slidesharecdn.com/purduetecsupnetforensics-140226070448-phpapp01/85/Network-Forensics-Intro-16-320.jpg)
![QUICK REVIEW: NETWORKING (CONT’D)
The OSI Model of networking for the Internet and common protocols at each level
[Layer 8] – Human
Layer 7 – Application
e
n
c
a
p
s
u
l
a
t
i
o
n
Layer 6 – Presentation
Layer 5 – Session
Layer 4 - Transportation
Layer 3 – Network
Layer 2 – Data-link
Protocol Highlights
HTTP, DHCP, DNS, SMB, OSPF…lots more
MIME
SSL/TLS, NetBIOS, SAP, PPTP, RTP
TCP, UDP
IP, ICMP, IPSec, IGMP, IPX
ARP, PPP, L2TP, Frame Relay
Layer 1 – Physical
Ethernet, USB, FireWire, RS-232, 802.11
Layer 0 – Media
RJ45 ethernet cables, 2.4-5Ghz spectrum](https://image.slidesharecdn.com/purduetecsupnetforensics-140226070448-phpapp01/85/Network-Forensics-Intro-17-320.jpg)
![QUICK REVIEW: NETWORKING (CONT’D)
The OSI Model of networking for the Internet
[Layer 8] – Human
Layer 7 – Application
e
n
c
a
p
s
u
l
a
t
i
o
n
Layer 6 – Presentation
Layer 5 – Session
Layer 4 - Transportation
Layer 3 – Network
Layer 2 – Data-link
Layer 1 – Physical
[Layer 0] – Media
Content can be found mainly at the
application and transport layers,
although technically could exist
anywhere via obscure/custom protocols
(such as the use of covert channels).](https://image.slidesharecdn.com/purduetecsupnetforensics-140226070448-phpapp01/85/Network-Forensics-Intro-18-320.jpg)
![QUICK REVIEW: NETWORKING (CONT’D)
The OSI Model of networking for the Internet
[Layer 8] – Human
Layer 7 – Application
e
n
c
a
p
s
u
l
a
t
i
o
n
Layer 6 – Presentation
Layer 5 – Session
Layer 4 - Transportation
Layer 3 – Network
Layer 2 – Data-link
Layer 1 – Physical
[Layer 0] – Media
Context can be found at every level
of the OSI model, however the most
useful context is typically:
Layer 2 – MAC addresses to ID devices
Layer 3 – IP Addresses, ICMP response
flags (OS Finger Printing)
Layer 4 – Timing/sizing information (OS
Finger Printing)
Layer 7 – Meta data provided by HTTP,
NBNS, and Routing protocols
Layer 8 – naming conventions and other
indicative habits/patterns](https://image.slidesharecdn.com/purduetecsupnetforensics-140226070448-phpapp01/85/Network-Forensics-Intro-19-320.jpg)

![WHERE DOES POTENTIAL EVIDENCE EXIST?
What sources are we trying to acquire?
[
It is paramount to understand that this is not a discrete question –
these are SYSTEMS of systems that are interdependent. A pcap alone
is not the extent of network forensics.
]](https://image.slidesharecdn.com/purduetecsupnetforensics-140226070448-phpapp01/85/Network-Forensics-Intro-21-320.jpg)
![WHERE DOES POTENTIAL EVIDENCE EXIST?
EVIDENCE PROVIDERS FOR A SINGLE SYSTEM OF A SERVER/CLIENT DEVICE
Network
Transmissions
Volatile
[Main]
Memory
Persistent
[Secondary]
Memory](https://image.slidesharecdn.com/purduetecsupnetforensics-140226070448-phpapp01/85/Network-Forensics-Intro-22-320.jpg)

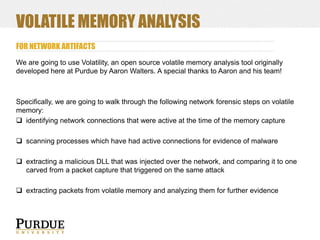
![WHAT POTENTIAL EVIDENCE EXISTS?
EXAMPLE NETWORK ARTIFACTS IN STORAGE MEDIA [NON-EXHAUSTIVE]
Volatile (Primary/Main) Memory
(this includes buffers on NICs)
open/prior connections, paired with processes that initiated them
recently used/downloaded programs and temporary files
recently run command output (ping/tracert/etc)
DNS cache
routing/arp table information
packets (buffered in memory)
Persistent (Secondary) Memory
recently run network programs (prefetch on Windows >= XP for instance)
logs/event records
recently visited URLs
IP addresses in email headers, configuration files, etc
Network captures (did the person have packet captures on their machine?)](https://image.slidesharecdn.com/purduetecsupnetforensics-140226070448-phpapp01/85/Network-Forensics-Intro-24-320.jpg)