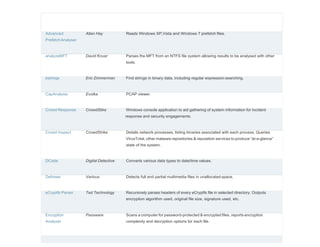
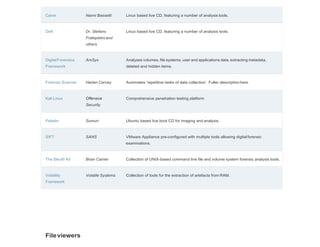
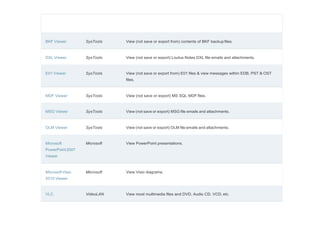
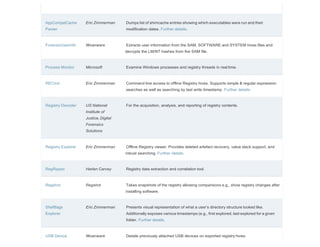
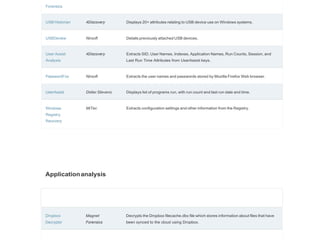
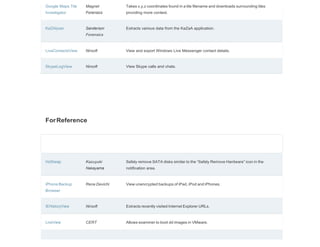
This document is a comprehensive list of free computer forensic tools compiled by Forensic Control, last updated on November 29, 2017. It emphasizes that the listed software is provided without support or warranties, and users are responsible for verifying licensing agreements. The tools are categorized into various sections, including disk tools, email analysis, data analysis, internet analysis, and more, covering a wide range of forensic applications.

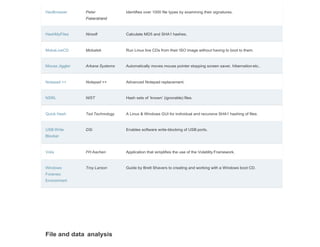
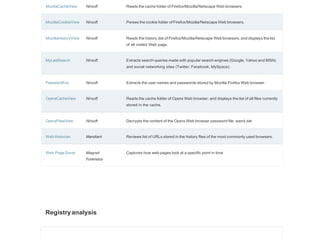
![Disk tools and data capture
ArsenalImage
Mounter
Arsenal
Consulting
Mounts disk images as complete disks in Windows, giving access to Volume Shadow
Copies, etc.
DumpIt MoonSols Generates physical memory dump of Windows machines, 32 bits 64 bit. Can run from
a USB flash drive.
EnCaseForensic
Imager
Guidance
Software
Create EnCase evidence files and EnCase logical evidence files [direct download link]
EncryptedDisk
Detector
Magnet
Forensics
Checks local physical drives on a system for TrueCrypt, PGP, or Bitlocker encrypted
volumes.
EWF MetaEditor 4Discovery Edit EWF (E01) meta data, remove passwords (Encase v6 andearlier).
FAT32 Format Ridgecrop Enables large capacity disks to be formatted as FAT32.
Forensics
Acquisition of
Websites
Web Content
Protection
Association
Browser designed to forensically capture web pages.
FTK Imager AccessData Imaging tool, disk viewer and image mounter.
Guymager vogu00 Multi-threaded GUI imager under running under Linux.](https://image.slidesharecdn.com/freecomputerforensicsoftware-240709144809-16c11346/85/Free-Computer-Forensic-Software-s-list-by-Forensic-Control-2-320.jpg)