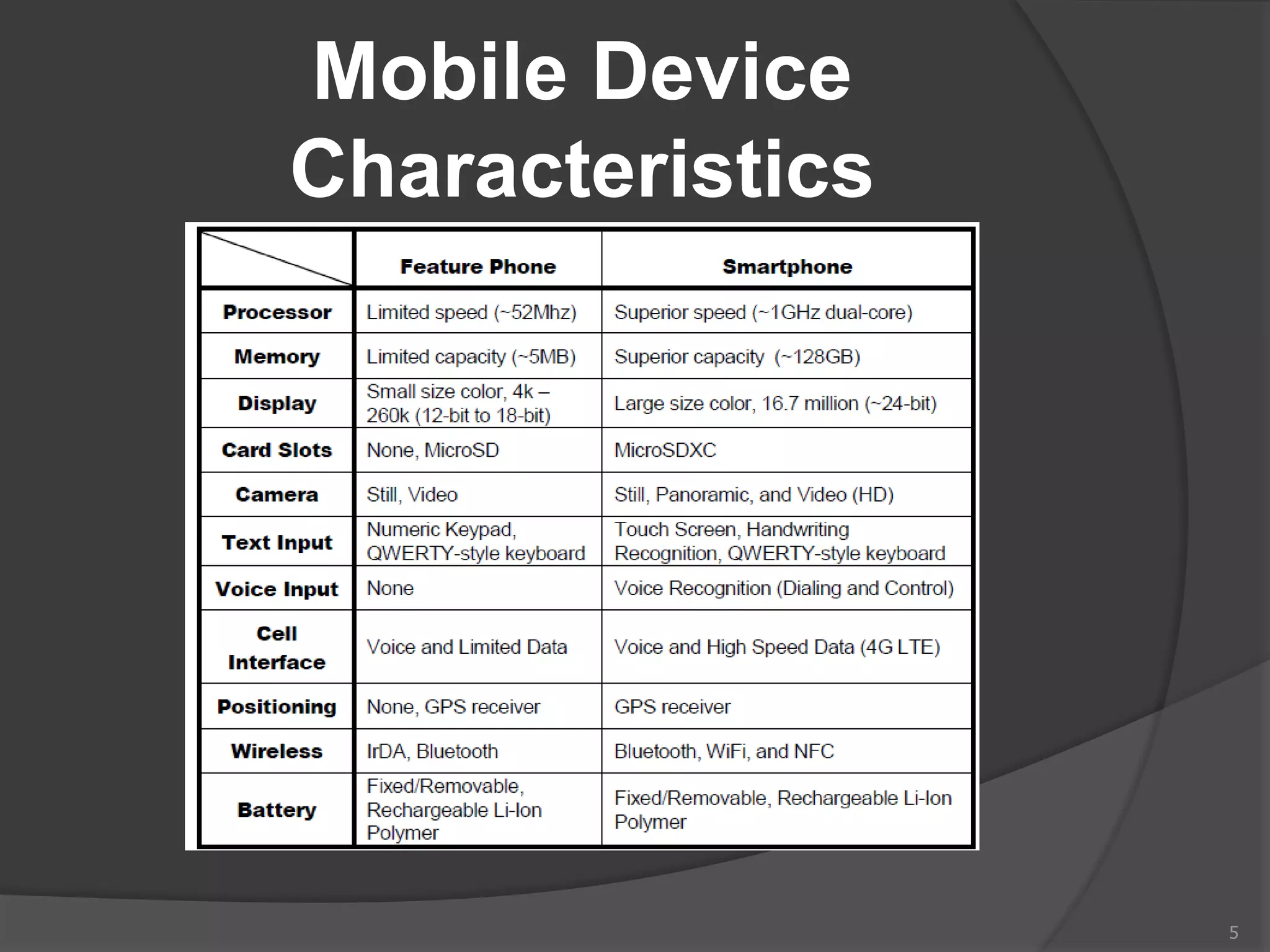
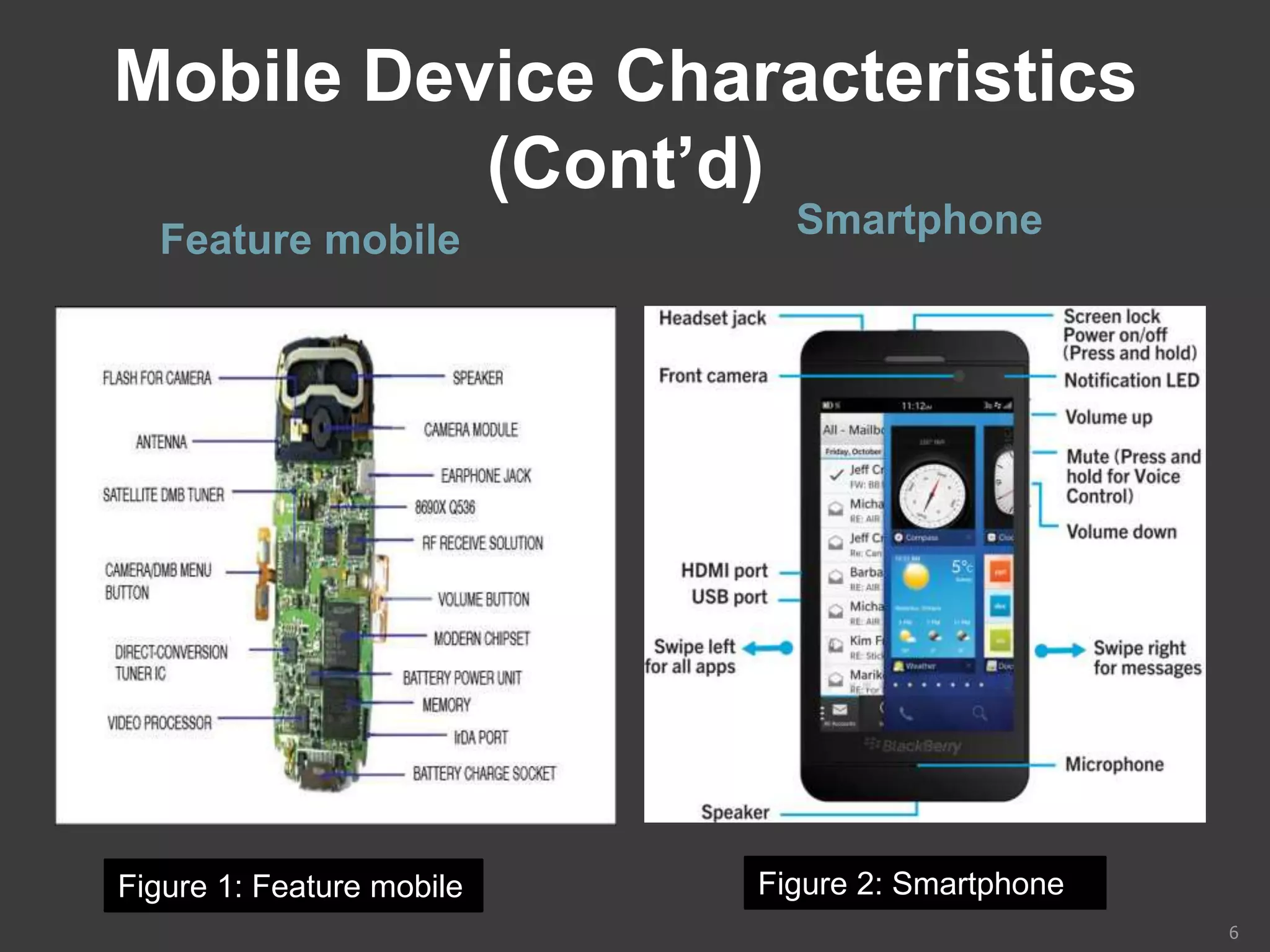
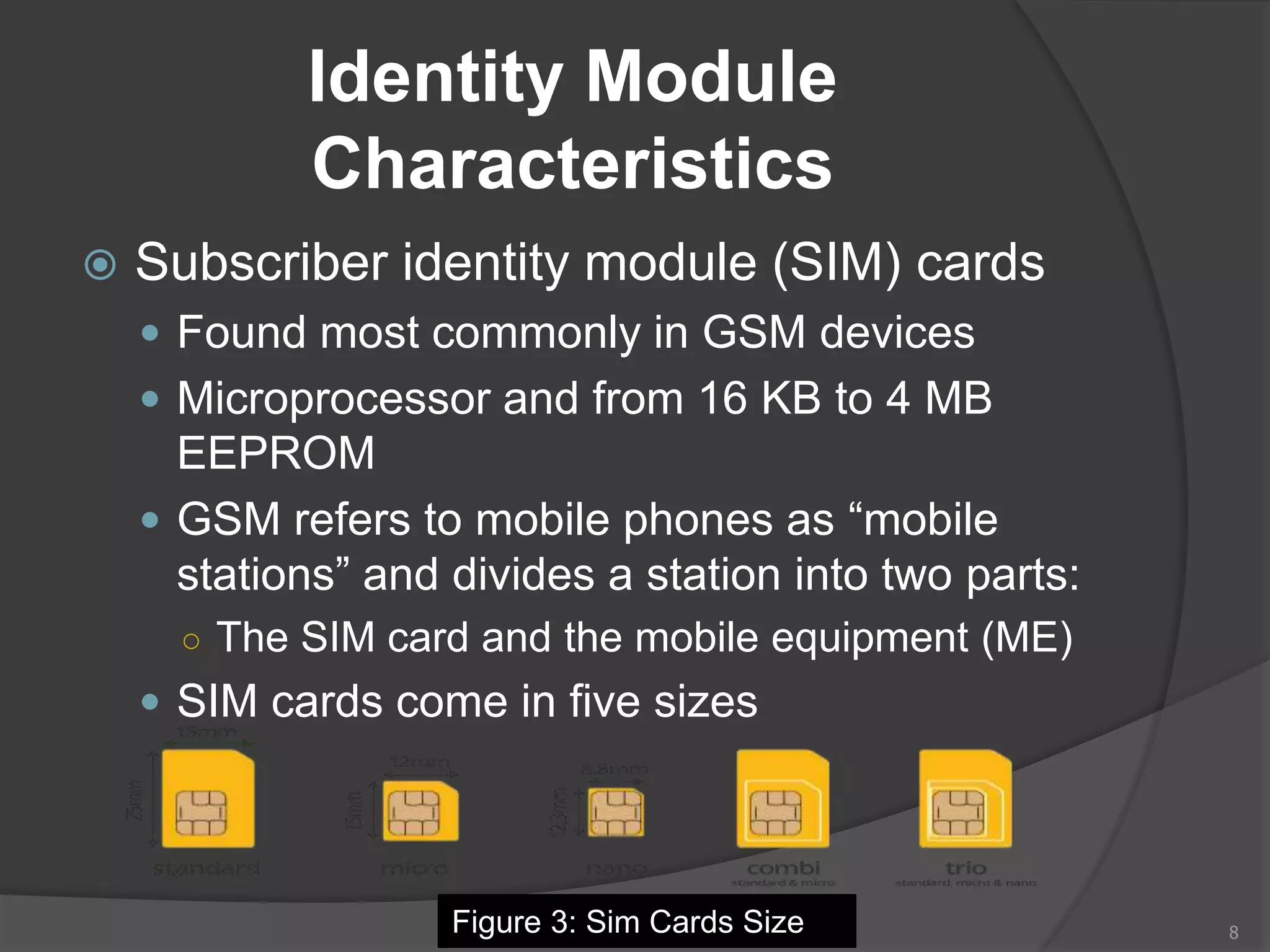
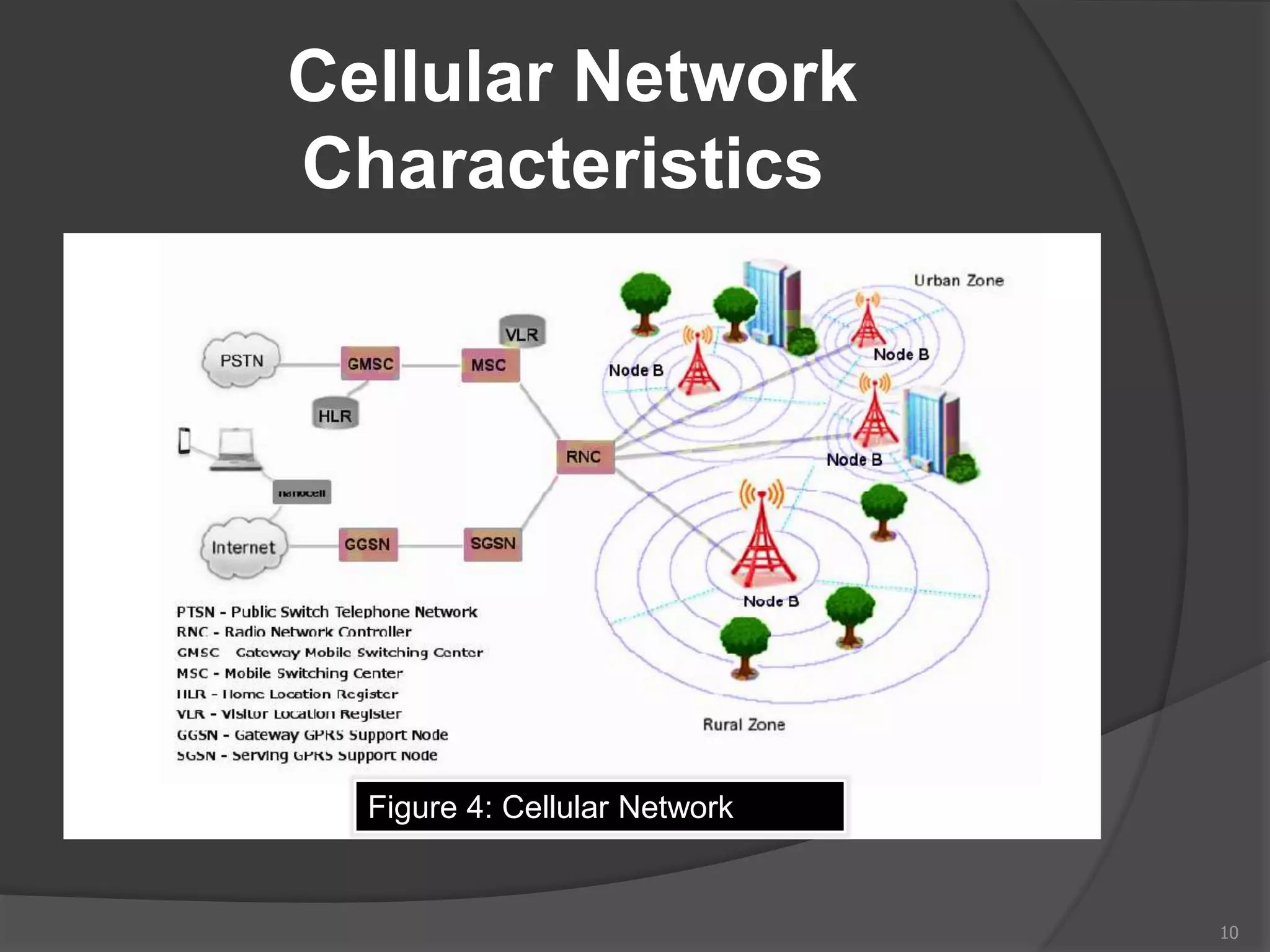
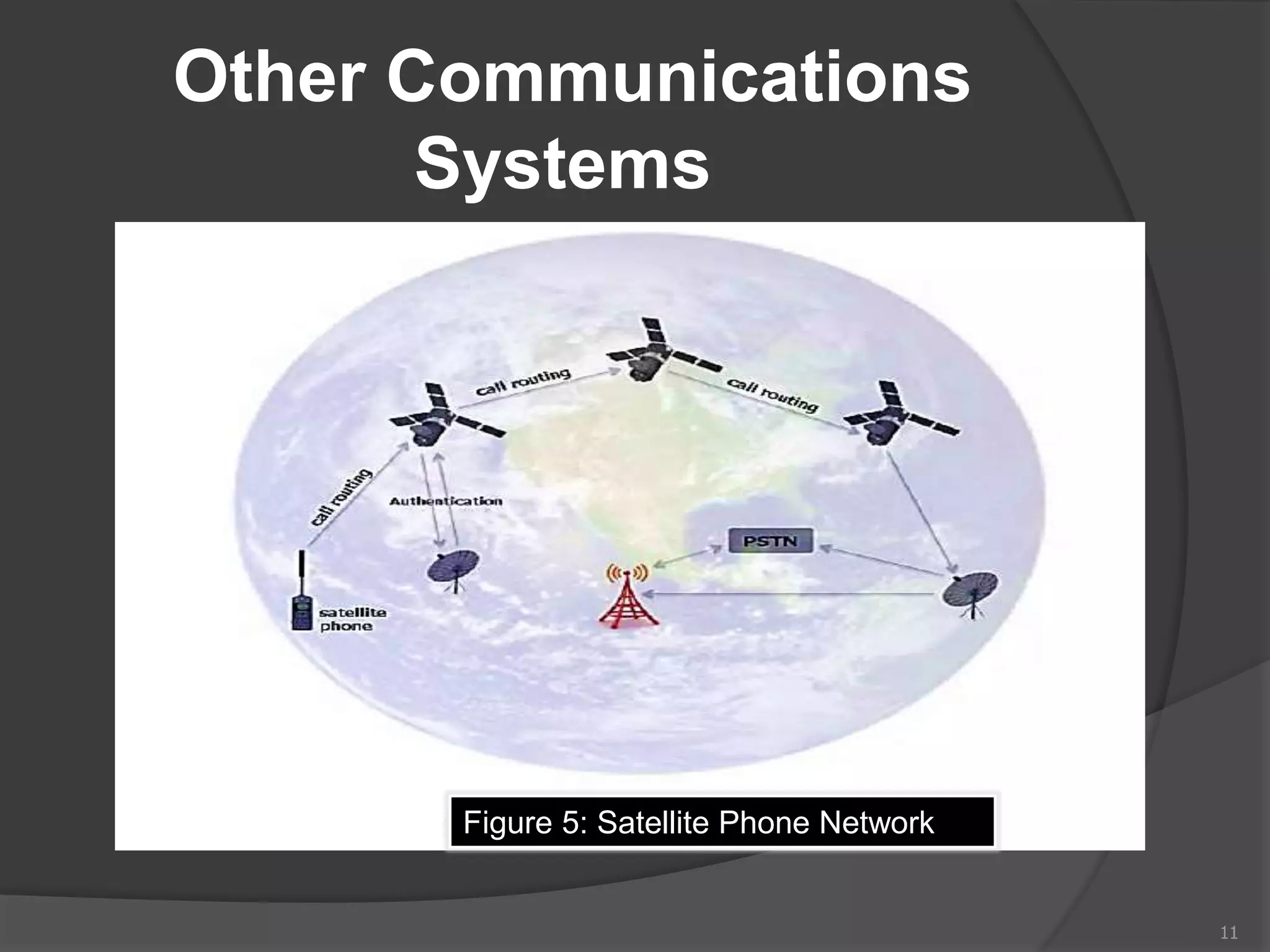
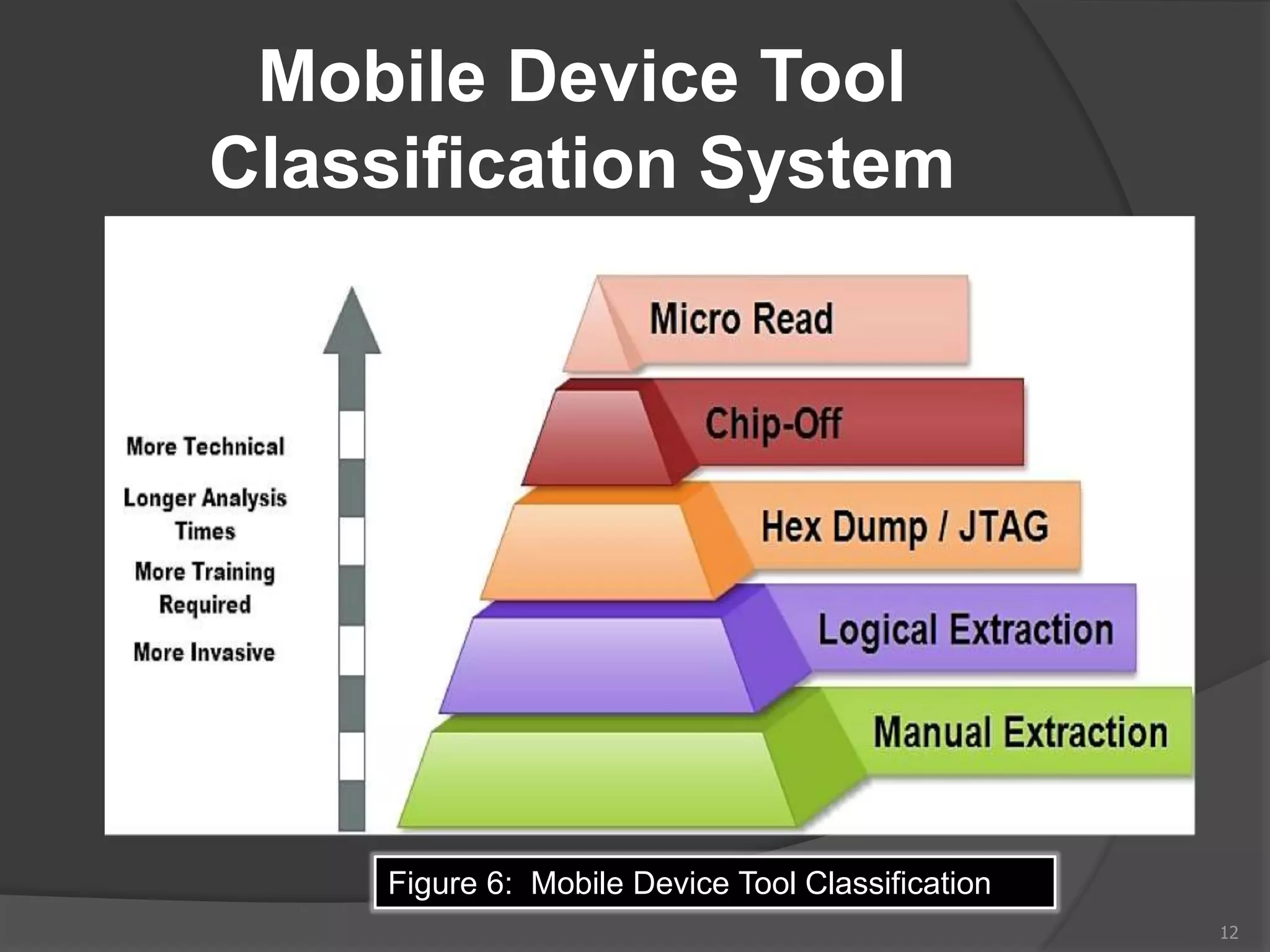
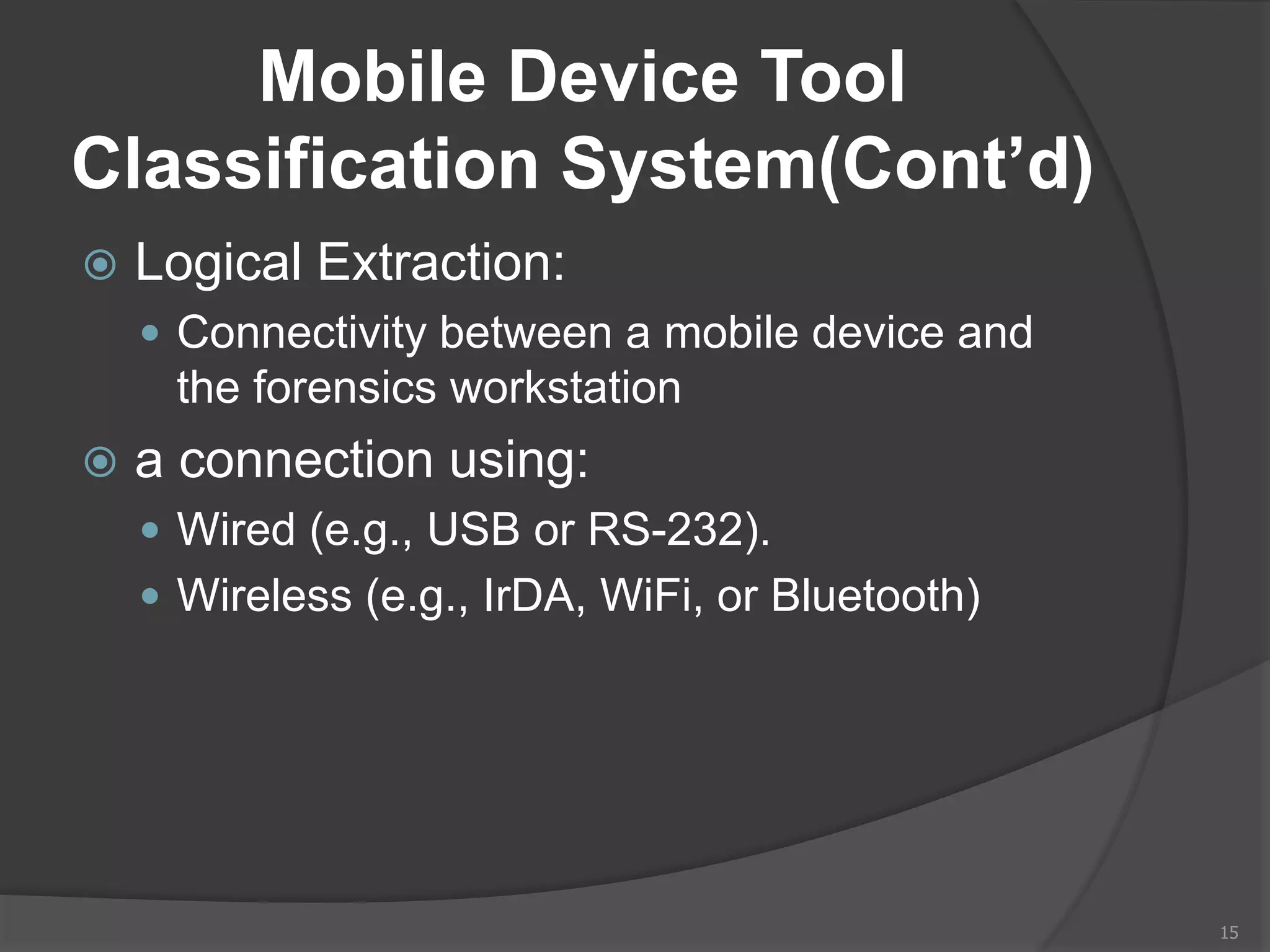
This document provides an overview of mobile device forensics. It discusses how people store personal information on mobile devices and the challenges of investigating these devices. The document covers mobile device characteristics, memory types, identity modules, cellular networks, and investigative tools and methods. These include manual extraction, logical extraction, chip-off acquisition, and preservation techniques like isolation and acquisition of internal memory, SIM cards, and external storage. The objectives are to understand mobile device forensics and the characteristics and challenges involved in acquiring, analyzing, and investigating evidence from mobile devices.