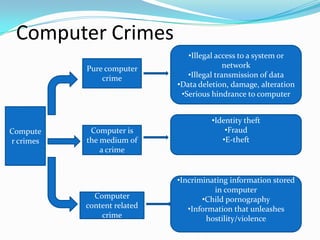
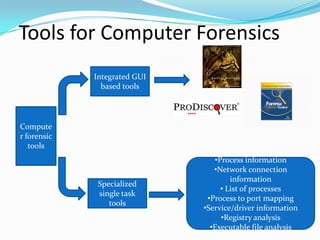
Computer forensics is the scientific process of preserving, identifying, extracting, and interpreting data from computer systems, networks, wireless communications, and storage devices in a way that is legally admissible. It involves using special tools to conduct a forensic examination of devices, networks, internet activities, and images in order to discover potential digital evidence. Common computer forensic tools are used to recover deleted files, analyze financial and communications records, and investigate crimes like fraud, identity theft, and child pornography.