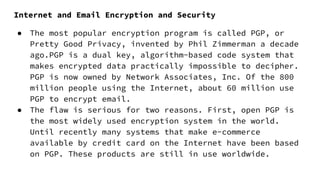
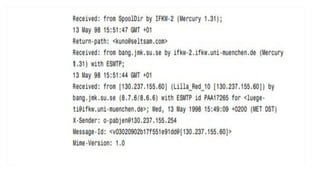
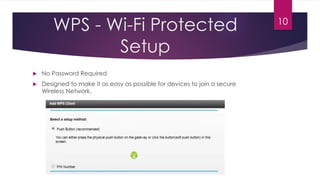
The document outlines the various types of computer forensics technologies utilized in military, law enforcement, and business contexts, emphasizing their role in recovering data and analyzing cyber threats. Key aspects include the objectives of cyber forensics, types of technologies used, and specialized techniques such as live forensics and data recovery. It also discusses encryption methods, vulnerabilities, and the importance of securing data against unauthorized access, as well as cybersecurity measures for wireless networks.






















![Examples:
● CoolWebSearch, a group of programs, takes advantage of
Internet Explorer vulnerabilities. The package directs
traffic to advertisements on Web sites including
coolwebsearch.com. It displays pop-up ads, rewrites
search engine results, and alters the infected computer's
hosts file to direct DNS lookups to these sites.
● FinFisher, sometimes called FinSpy is a high-end
surveillance suite sold to law enforcement and
intelligence agencies. Support services such as training
and technology updates are part of the package.
● Zwangi redirects URLs typed into the browser's address
bar to a search page at www.zwangi.com,[53] and may also
take screenshots without permission.](https://image.slidesharecdn.com/mod2combined-191025004411/85/Cyber-Forensics-Module-2-25-320.jpg)