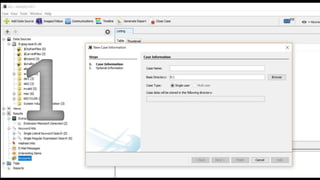
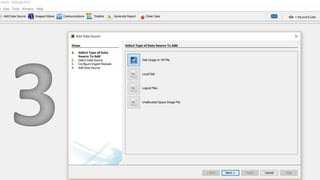
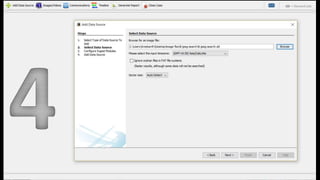
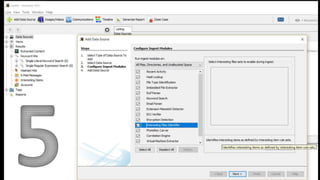
The document introduces Autopsy, an open source digital forensics platform. It provides an overview of Autopsy's features which allow users to efficiently analyze hard drives and smartphones through a graphical interface. Key capabilities include timeline analysis, keyword searching, web and file system artifact extraction, and support for common file systems. The document includes screenshots and references for additional information on Autopsy's functions and use in digital investigations.