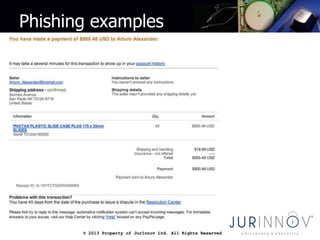
The document provides guidelines for safe computing practices, highlighting the importance of protecting personal and sensitive information from cybercriminals. Key topics include secure password creation, recognizing phishing attempts, and safe browsing habits, especially on public computers. It emphasizes the role of individuals in maintaining cybersecurity and mitigating risks associated with malware and data breaches.