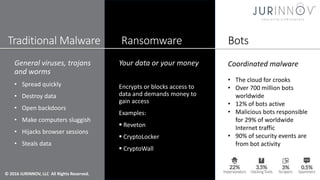
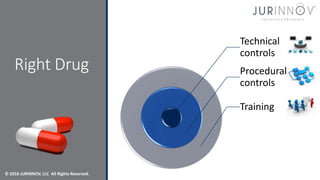
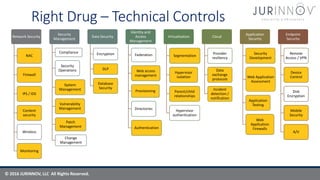
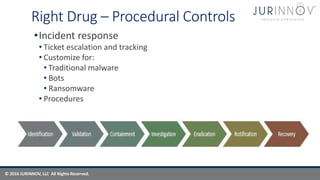
The document discusses cybersecurity strategies to combat malware and advanced persistent threats, highlighting risks associated with traditional malware, bots, and ransomware. It emphasizes the importance of technical and procedural controls, incident response, and continuous improvement in security practices. The content serves as a guide for organizations to strengthen their cybersecurity posture through assessments, governance frameworks, and effective communication of security protocols.