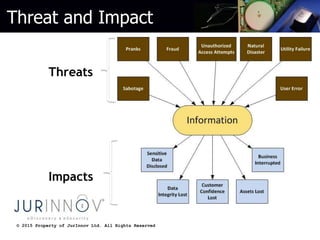
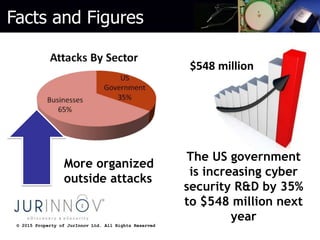
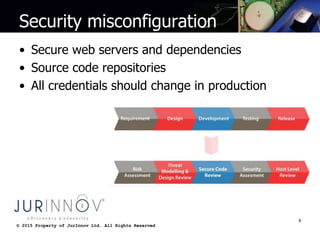
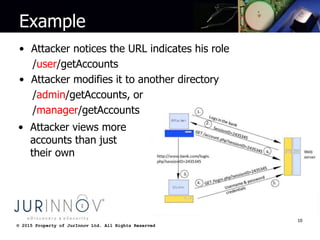
The document discusses common web development security mistakes and how to correct them. It covers security misconfiguration, unrestricted URL access, unvalidated redirects and forwards, direct object references, insecure storage of sensitive data, and insufficient transport layer protection. Mistakes in these areas can allow attackers to access unauthorized data and functionality. The document provides techniques to protect against these risks, such as verifying system configurations, restricting access by URL and role, validating redirect targets, encrypting sensitive data storage and transmissions, and more.