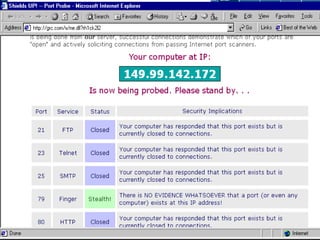
This document discusses hackers and network intruders. It defines key hacking terms and outlines the threats posed by different types of hackers. It also describes common methods used by hackers to gain unauthorized access, such as exploiting software vulnerabilities, password guessing, and using backdoors or trojan horses. The document discusses intrusion detection and prevention techniques and some legal and ethical issues surrounding hacking.