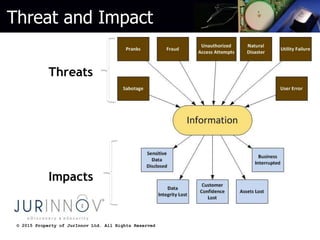
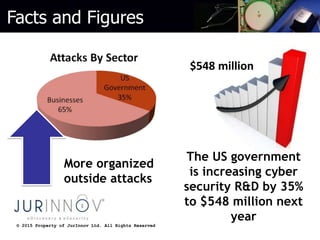
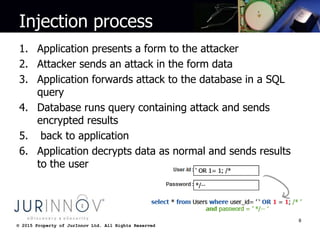
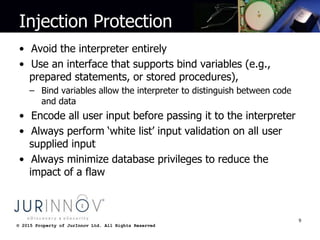
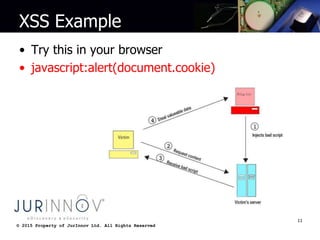
The document discusses various types of website attacks such as injection attacks, cross-site scripting, session management attacks, and object reference attacks. It provides details on the nature of each attack, their potential impacts, and techniques for protecting against them. Some key points are that the average breach costs $214 per record and $7.2 million per incident, while the US is increasing cybersecurity funding by 35% to $548 million. Injection attacks can allow access to entire databases or operating systems if not properly protected against with input validation and encoding. Cross-site scripting can steal user data or install malware if raw user input is reflected in outputs. The document recommends output encoding and validating all user input to prevent attacks.