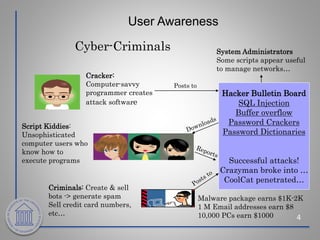
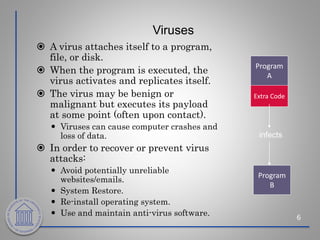
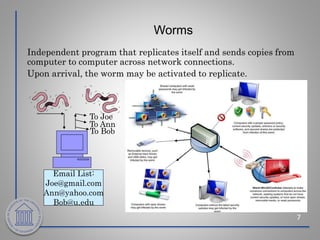
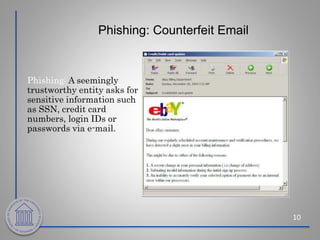
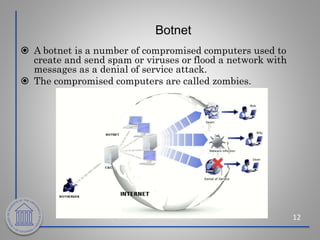
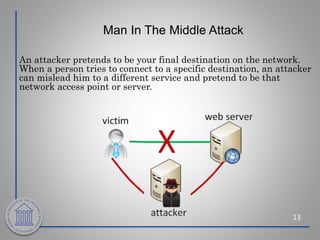
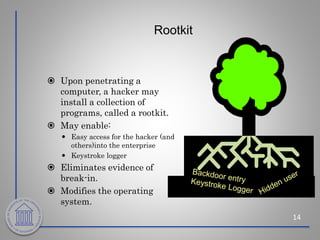
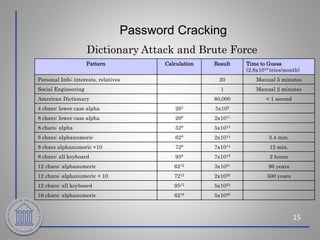
This document provides an overview of cybersecurity topics including the importance of cybersecurity, leading threats such as viruses, worms, and social engineering, best practices to avoid threats such as using strong passwords and antivirus software, and what to do if a cybersecurity incident is suspected. Key points covered include the risks of identity theft and data loss if security is not followed, common vectors for vulnerabilities exploited by cyber criminals, and the need to protect systems in the same way doors are secured at home.